“Urban environments’ physical environment characteristics present unique challenges in any of their three dimensions of above, below, or at ground level. Maneuver, protection, intelligence gathering, communications, fires, and battle damage assessment are among the issues. Vertical and subterranean features  will disrupt line-of-sight (LOS), complicating situational awareness, increasing risk, and requiring adaptive leaders trained and practiced in the nuances of mission command.” — TRADOC Pamphlet 525-92-1, The Changing Character of Warfare: The Urban Operational Environment, April 2020, p. 19.
will disrupt line-of-sight (LOS), complicating situational awareness, increasing risk, and requiring adaptive leaders trained and practiced in the nuances of mission command.” — TRADOC Pamphlet 525-92-1, The Changing Character of Warfare: The Urban Operational Environment, April 2020, p. 19.
[Editor’s Note: Storytelling — creative fictional writing and narrative building — is one of the tools Army Mad Scientist uses to help the Army explore how concepts, technologies, and other capabilities could be employed and operationalized. As previously shared by proclaimed Mad Scientists and best-selling authors P.W. Singer and August Cole, narrative effectively packages information the way our brains are designed to absorb it, creating lasting messages. By connecting information to our emotions, narrative is more likely to promote action. People are driven to share narratives, leading the audience to become part of its marketing. This virality contributes to the creation of a network of people with increased understanding of potential futures.
Mad Scientist Laboratory is pleased to feature today’s guest post by the Radio Research Group, with their compelling story about the challenges a Special Operations team face in executing a SubTerranean (SubT) mission beneath Dense Urban Terrain in the future Operational Environment. Degraded situational awareness and comms, lethal autonomous weapons, psychotropic gas, and a transparent battlefield, all wrapped within Great Power Competition — Aqsa and her SubT Quantum Team 1 “embrace the suck,” adapt, and overcome to execute their harrowing mission and exploit their target beneath the streets of Singapore — Read on!]
SubT Quantum Team 1, Singapore
 The utility tunnel stretched deep into the dark, industrial nest of cables and pipes. Infrared illuminators lit up the subterranean tropical humidity with beams of vicious light. Sounds of quiet footsteps filled the tunnel, the squad of women walked silently, specifically selected and trained for SubTerranean (SubT) combat.
The utility tunnel stretched deep into the dark, industrial nest of cables and pipes. Infrared illuminators lit up the subterranean tropical humidity with beams of vicious light. Sounds of quiet footsteps filled the tunnel, the squad of women walked silently, specifically selected and trained for SubTerranean (SubT) combat.
 Aqsa paused to sip water from her Camelbak, adjusting her night vision. It’s damned hot, she thought to herself, kitted out in ceramic body armour, laden with weapons and comms gear.
Aqsa paused to sip water from her Camelbak, adjusting her night vision. It’s damned hot, she thought to herself, kitted out in ceramic body armour, laden with weapons and comms gear.
Her Next Generation Squad Weapon sat heavy in her hands, made by Sig Sauer and running plastic-cased 6.8mm ammunition.
Freaking ridiculous, Aqsa thought to herself, looking down at the heavy rifle, a relic of the War on Terror. The least useful piece of kit we have. Give me a Glock and a more powerful tactical computer.
 She stood amidst a battle of bits and qubits, a combat of influence and electromagnetic dominance. In fifth generation warfare, a tiny 6.8mm projectile was meaningless — dead weight.
She stood amidst a battle of bits and qubits, a combat of influence and electromagnetic dominance. In fifth generation warfare, a tiny 6.8mm projectile was meaningless — dead weight.
Aqsa and her battalion were a select group of female warriors, specially trained in SubT combat and infiltration. The women came from a diverse background of computer scientists, physicists, cryptographers, and even a digital artist — true modern warriors.
“Going Hot! Smoke, Smoke, Smoke!” whispers from the point woman filled Aqsa’s earpiece.
 An explosion of light filled the tunnel; each member flipped up their night vision devices. She removed her SGE gas mask, lifting parts of her combat hijab to assure a good seal. She checked her rebreather status with her flexible ATAK (Android Team Awareness Kit) display strapped around her forearm.
An explosion of light filled the tunnel; each member flipped up their night vision devices. She removed her SGE gas mask, lifting parts of her combat hijab to assure a good seal. She checked her rebreather status with her flexible ATAK (Android Team Awareness Kit) display strapped around her forearm.
The Breacher stabilized an oxygen acetylene torch, and the tunnel filled with toxic smoke.
Each member of the twelve woman unit was kitted out with ELABS (Extreme Limited Access Breathing Systems). These units were SCBA (Self-Contained Breathing Apparatus) systems specifically designed for SubT combat. A single thermobaric grenade could remove the oxygen from an entire tunnel network, hence the need for ELABS.
 The Point woman held a bulletproof barricade behind the Breacher, in case someone fired through the locked door. She looked down at her E-INK (Electronic Ink) ATAK wrist display; inertial guidance placed them just meters from their target.
The Point woman held a bulletproof barricade behind the Breacher, in case someone fired through the locked door. She looked down at her E-INK (Electronic Ink) ATAK wrist display; inertial guidance placed them just meters from their target.
Aqsa looked up at the conduits above, bundles of wires, ethernet, and quantum encrypted fiber snaked above. One of these was their target. She wished they could simply cut and splice the damned cable, then and there. Lives had been taken for this mission, and it was never as simple as just “a simple splice” — not in a post-quantum key cryptography world.
 “Breach, Breach, Breach!” came through Aqsa’s bone conduction headset. The torch was silenced, and a sledgehammer sounded out upon a door. “Alarm tripped, Mark!”
“Breach, Breach, Breach!” came through Aqsa’s bone conduction headset. The torch was silenced, and a sledgehammer sounded out upon a door. “Alarm tripped, Mark!”
A drone was thrown into the room.
Fifteen seconds,
“Clear!”
The women flooded the new chamber, trained since childhood for a mission like this.
Slow is Smooth. Smooth is fast. Aqsa worked her feet and her rifle as she entered the room. A flashlight was lit, and her night vision came off, revealing a tightly confined server room.
Nothing, no enemy, no weapons, just servers and bundles of wires.
The air was still trash, so with her gas mask fogged out, Aqsa moved up to the shimmering server rack. A large cable snaked up through the floor.
 The HASEX-1 (Hong Kong and Singapore Exchange) fiber optic cable stared back at Aqsa, front and center. The bright orange cable glistened in their headlamps at the center of the room. The cable had been built by “private investors” to reduce latency between the two most active stock markets in the world. Samples of the fiber optics “borrowed” during manufacture showed a completely new crystalline structure, something far more clear and stable than anything coming out of Asia before.
The HASEX-1 (Hong Kong and Singapore Exchange) fiber optic cable stared back at Aqsa, front and center. The bright orange cable glistened in their headlamps at the center of the room. The cable had been built by “private investors” to reduce latency between the two most active stock markets in the world. Samples of the fiber optics “borrowed” during manufacture showed a completely new crystalline structure, something far more clear and stable than anything coming out of Asia before.
Intel was convinced it was being used as part of an elicit quantum command and control network — an Asian quantum MILNET. The elegance of quantum  encryption is that a simple “wiretap” destroys the quantum state. With current understandings of physics, it’s unbreakable, as observing the information destroys it.
encryption is that a simple “wiretap” destroys the quantum state. With current understandings of physics, it’s unbreakable, as observing the information destroys it.
But Aqsa, like the rest of her colleagues knows that nothing is “unbreakable” — there is always a way. Aqsa wrote her PhD on the topic. She kneeled down before the shimmering server rack, or a Quantum multiplexer, to be more precise. She retrieved a small black box from her belt, and plugged it into her SDR (Software Defined Radio). A temperature was displayed on her ATAK display.
Near absolute zero degrees kelvin.
Aqsa set the portable quantum computer atop the fiber optic multiplexer, and plugged in a dangling CAT-7 running from the portable quantum computer.
The multiplexer rebooted. Logs began appearing on her display. Aqsa wiped the sweat from the outside of her gas mask. She looked down to her ATAK display trapped to her arm, code scrolled up the 30 Hz, full color, flexible display.
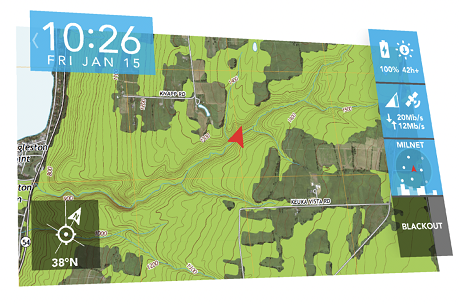
The display was hooked up to her SDR. It held a considerable amount of computing power, which in this case was being used to run an exploit model on a commercially manufactured ethernet switch.
Intel couldn’t provide the manufacturer of the switch, but if it is not SSITH (Systems Security Integration Through Hardware and firmware)-certified, or used commercial cryptography in any way, Aqsa would break it.
“We’ve got company, automated, entering the tunnel” the head ISR officer sounded out calmly, “Five units, verified enemy.”
The sounds of safeties flicked off, as two Soldiers surrounded an Israeli-made ballistic barricade in front of the door.
Nav looked to Aqsa, “Time?”
 She looked down at her display, not every model had run, but the switch wasn’t cracking. The model was being run across all of her unit’s tactical SDRs, using the MANET (Mobile Ad Hoc Network) as a distributed computing network. “Unknown — It’s not using a commercial curve or known zero days. We haven’t seen this level of security before.”
She looked down at her display, not every model had run, but the switch wasn’t cracking. The model was being run across all of her unit’s tactical SDRs, using the MANET (Mobile Ad Hoc Network) as a distributed computing network. “Unknown — It’s not using a commercial curve or known zero days. We haven’t seen this level of security before.”
ISR looked down to her display, “We’ve gotta go!”
Aqsa made a quick decision, unstrapping her SDR, unplugging her display and removing velcro patch antennas from her shoulders. She tucked the radio into the server rack, leaving the antennas at random locations behind the server.
She plugged her display and comms cables into her backup SDR located on the back of her plate carrier, and ran the new patches.
A feeling of intense anxiety crept over the team. The exploit had failed — for now, and enemy forces had entered the tunnel.
“Lights out!”
The server room descended into darkness, as Aqsa flipped on her night vision.
“Comms check,” Her radio synchronized with the MANET using spread spectrum LPI/ LPD (Low Probability of Intercept / Low Probability of Detection) waveforms.
“Roger,” her colleague retorted back.
An ISR notification pinged across the MANET, detecting a slight decrease in electronic background noise entropy. Someone, or something was transmitting encrypted data nearby. Our local instance of EWIRDB (Electronic Warfare Integrated Reprogramming Database) declared it was most likely a Red-made generic SDR, a copy of a Persistent Systems unit, and was attempting to jam.
“Visual Contact!”
Several robotic grenades were thrown into the tunnel. Gunfire erupted.
“Gas, Gas, Gas!” someone yelled. “AQGR-12” flashed across their wrist screens.
 Aqsa’s skin began to tingle. While technically non-lethal, the nerve agent AQGR-12 caused a strange sensation on any open skin. If inhaled, it would cause intense, nightmarish psychedelic effects. While local teenagers had been reported to take the nerve agent for fun, it would mark certain death in a tactical situation requiring the utmost mental clarity.
Aqsa’s skin began to tingle. While technically non-lethal, the nerve agent AQGR-12 caused a strange sensation on any open skin. If inhaled, it would cause intense, nightmarish psychedelic effects. While local teenagers had been reported to take the nerve agent for fun, it would mark certain death in a tactical situation requiring the utmost mental clarity.
Aqsa checked her gas mask, and ensured everyone’s ELAB was running nominally from her ATAK display.
One of the robotic grenades exploded on target as a nightmarish scene unfolded in the tunnel ahead.
“Formation!” the point woman yelled, showing a hand signal for a charge. Two women fired semi-automatic Benelli shotguns into the void. Command had refused to purchase shotguns, arguing they had already made a significant investment in new 6.8mm assault weapons. The automatic shotguns had to be “smuggled” into their unit from the States. Counter robotic units had found them to be invaluable.
Gunfire erupted from ahead, slamming into the self-healing, ballistic barrier. Another robotic grenade went off, then gunfire stopped.
Aqsa, now working to control her breathing, checked her display. Still connected via 60 GHz MANET to the quantum computer in the server room. The exploit had made its way into the ethernet controller using a cracked certificate, and was working on the multiplexer’s CPU. A popup appeared: “Success, rebooting…”
“Exploit Delivered, Nice job ladies!” Aqsa whispered into her radio. She triggered a self-destruct of the SDR.
The exploit was complex, and classified to everyone except Aqsa. It would take months to know if it had worked.
Now it was time to get the hell out.
 The unseen UAU (Unknown Autonomous Unit) fired an infrared dazzler, destroying nearly everyone’s night vision devices. If everyone hadn’t been wearing UV shielded gas masks, the entire team would have been blinded. Most of the unit flicked up their destroyed NVDs. White headlamps flicked on. A bright spotlight illuminated the tunnel ahead from atop the handheld barricade.
The unseen UAU (Unknown Autonomous Unit) fired an infrared dazzler, destroying nearly everyone’s night vision devices. If everyone hadn’t been wearing UV shielded gas masks, the entire team would have been blinded. Most of the unit flicked up their destroyed NVDs. White headlamps flicked on. A bright spotlight illuminated the tunnel ahead from atop the handheld barricade.
Someone threw a flare into the smoky, noxious gas filled void. The visible flash from the dazzler was still wearing off. They were going in blind.
Another autonomous grenade went off.
ISR: “We’ve still got signal!”
 Someone on point fired their machine gun. A shotgun blast. They charged forward, passing the destroyed ruins of an unnamed bipedal vehicle of Asian origin. Aqsa fired two shots into the AU for good measure. Asian script marked the side with the name “Dot.”
Someone on point fired their machine gun. A shotgun blast. They charged forward, passing the destroyed ruins of an unnamed bipedal vehicle of Asian origin. Aqsa fired two shots into the AU for good measure. Asian script marked the side with the name “Dot.”
A soft thump echoed through the chamber, Grenade!
An explosion.
Aqsa screamed as she was knocked on her fourth point of contact. Her Team Wendy helmet scraped against cement. She heard her colleagues crying out, someone lost their gas mask, inhaling the psychoactive atmosphere.
More gunfire.
Aqsa steadied herself, grabbing a second level barricade. The first layer had been wiped out. Three of her colleagues were down.
“I need backup here, three down. Taking point!” Aqsa held up the barricade and moved forward. Two of her team joined behind and fired through the barricade, launching two more robotic grenades. An Explosion.
ISR: “Signal Gone, No movement!”
Aqsa reached the staircase to the surface, retrieving the robotic grenades and clipping them to her plate carrier. Their rear ISR drone floated above the spiral staircase in the smoke, its LED lights flashing the “friendly” color code for the day. Their medic, who had inhaled some of the toxins, had been sedated and was now under oxygen — but not before she confirmed two of her colleagues KIA, and applied medical aid (still hallucinating) to another.
They carried the bodies of their downed teammates behind them and hoisted the corpses up the staircase.
 Tunnel Exfil represented the gutted server room of a bombed out highrise. Clearly the AUs had located their position. The probability that the AUs had gotten a message out from the tunnel (during active jamming) was calculated by ATAK to be at least 10%. It was time to send a sitrep to command, and get the hell back to FOB Bali.
Tunnel Exfil represented the gutted server room of a bombed out highrise. Clearly the AUs had located their position. The probability that the AUs had gotten a message out from the tunnel (during active jamming) was calculated by ATAK to be at least 10%. It was time to send a sitrep to command, and get the hell back to FOB Bali.
Aqsa stripped off her gas mask, without checking CBRN, and nearly finished the contents of her Camelbak.
“Watch out for your hands and face,” Aqsa spoke into her bone mic. “The Chems are active for 12 hours unless neutralized. Comms?”
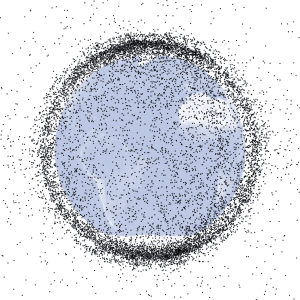
Comms: “I’ve got nothing on the uplink.” While their local MANET was live, and extremely difficult to jam (due to the short range of 60 GHz), SATCOMs had been taken out months ago. Low earth orbit had gone full Kessler, meaning the cascading effect of a few anti-sat missiles had caused every single object in low earth orbit to be completely obliterated.
No GNSS, no Comms, no LEO ISR. The remaining SATCOMS in geostationary, and even arctic elliptical were blown. While SOCOM was working on launching a few interplanetary optical relays (Try shooting SATCOMs out in Legrange points, Reds!), such deployments were still months away.
Allied forces at that point in time relied on a “Targeting Mesh,” made up of millions of small drones for ISR and comms.
The only problem was that the Targeting Mesh wasn’t there!
Aqsa sat down in a rubble covered office chair, her headlamp glowing red, night vision fried by the IR dazzler. The office building’s ceiling had collapsed, posters lined what was left of the walls encouraging workers to “Wear a Mask”, and “Social Distance”. She laughed, and looked over to Comms, who had stripped off her gas mask and was working a Harris SDR from a tablet.
“We need to get outside,” Comms looked up to Aqsa, who was now in command. “It’s like the Mesh isn’t even there. Even HF is out. No Barrage Jamming, just silence.”
There was only one way to get a message back to command, and it was insane. “Get me the latest sky charts,” Aqsa ordered Comms, opening Google Earth on her tablet, “You know what I’m thinking. SOCOM is going to be pissed!”
 ISR instructed each member of the team to remove their Israeli-made Fobrotex “GhostHoods.” These were essentially near and long range infrared camouflage ghillie suits, designed to conceal from enemy UAVs. The entire lightweight suit could fit into a small pocket. While these units would not protect from synthetic aperture, Red targeting computers relied mostly on thermal and visual signatures (and heavily modified OpenCV). Head ISR adjusted the GhostHoods on each of the members, draping them over the bodies of KIA.
ISR instructed each member of the team to remove their Israeli-made Fobrotex “GhostHoods.” These were essentially near and long range infrared camouflage ghillie suits, designed to conceal from enemy UAVs. The entire lightweight suit could fit into a small pocket. While these units would not protect from synthetic aperture, Red targeting computers relied mostly on thermal and visual signatures (and heavily modified OpenCV). Head ISR adjusted the GhostHoods on each of the members, draping them over the bodies of KIA.
 With a plan in place, the women moved out of the office building, and into a back exit behind the office building (or at least what was left of the building). The Singaporean sky was dark, rubble and burned vehicles littered the streets. The husk of a Boston Dynamics robot lay melted and contorted.
With a plan in place, the women moved out of the office building, and into a back exit behind the office building (or at least what was left of the building). The Singaporean sky was dark, rubble and burned vehicles littered the streets. The husk of a Boston Dynamics robot lay melted and contorted.
Lightning flickered in the distant dry summer heat.
 The single woman left with night vision looked up and shrieked. Aqsa squinted to see a perfectly distributed mesh of drones, slowly moving overhead. These were tagged with red LEDs, designed to induce fear in the enemy. Allied drones move pseudo randomly, this looked like a perfect beehive of aerial dominance. Aqsa had never seen something more nightmare inducing. She had seen a meme of something similar just a few days before. The first thing she thought was They are superior, then shook off the thought. It was a relic of subconscious programming, internet memes designed to hack her OODA loop.
The single woman left with night vision looked up and shrieked. Aqsa squinted to see a perfectly distributed mesh of drones, slowly moving overhead. These were tagged with red LEDs, designed to induce fear in the enemy. Allied drones move pseudo randomly, this looked like a perfect beehive of aerial dominance. Aqsa had never seen something more nightmare inducing. She had seen a meme of something similar just a few days before. The first thing she thought was They are superior, then shook off the thought. It was a relic of subconscious programming, internet memes designed to hack her OODA loop.
Aqsa swore out loud. The Allied targeting mesh was obliterated.
“Relax ladies,” ISR whispered over the MANET, “Red Coherent Change is garbage, and with these suits we will be very hard to detect.” The Suits were designed with a camouflage pattern designed to trick computer vision systems. “Just move slow, we are close to our target!”
The output power of their MANET was reduced to below 1 watt, bringing their IP based conversations far below the noise floor of enemy sensors.
 A deserted city park lay ahead, and a perimeter was set up. The city was crawling with UAUs, every member of the unit was scared. This wasn’t mechanized warfare, it was autonomous unmanned warfare. Bringing a human to a UAU fight is worse than fighting a machine gun position with a butter knife.
A deserted city park lay ahead, and a perimeter was set up. The city was crawling with UAUs, every member of the unit was scared. This wasn’t mechanized warfare, it was autonomous unmanned warfare. Bringing a human to a UAU fight is worse than fighting a machine gun position with a butter knife.
Comms unfolded a small, portable microwave SATCOM antenna, and aimed it below a gap between two buildings. Incredible thunderclouds rolled above. The Enemy targeting mesh remained unmoving, the thunderclouds rolling through and blurring the floating spots of red. Aqsa removed a SAR (Synthetic Aperture Radar) smoke grenade from her pouch marked “KA Band,” and adjusted the timer.
 A crescent moon smiled above them, almost perfectly vertical, being observed from equatorial Singapore.
A crescent moon smiled above them, almost perfectly vertical, being observed from equatorial Singapore.
“What on Earth are we aiming at?” A team member asked.
Comms retorted back, “It’s not on Earth, we are aiming for the Moon,” she smiled, the Harris SDR established a microwave data link at full power. Aqsa pulled the pin on the SAR grenade.
A message decrypted across Aqsa’s wrist screen
 SURFACE VESSELS, TARGET MESH DESTROYED. 7TH FLEET WIPED OUT. UUV MAKING WAY TO YOUR POSITION INDIA FOR EXFIL UNIFORM ZULU. ETA 72 HOURS GODSPEED
SURFACE VESSELS, TARGET MESH DESTROYED. 7TH FLEET WIPED OUT. UUV MAKING WAY TO YOUR POSITION INDIA FOR EXFIL UNIFORM ZULU. ETA 72 HOURS GODSPEED
Aqsa looked up to the heavens, and prayed. They were to head by underwater, autonomous vehicle deep into the jungles of Indonesia…
If you enjoyed this post, check out the following related content:
Realer than Real: Useful Fiction with P.W. Singer and August Cole, and associated podcast
Dense Urban Hackathon – Virtual Innovation, Dense Urban Environments (DUE): Now through 2050, A Chinese Perspective on Future Urban Unmanned Operations, and TRADOC Pamphlet 525-92-1, The Changing Character of Warfare: The Urban Operational Environment
Strategic Latency Unleashed! by Dr. Zachary S. Davis, Going on the Offensive in the Fight for the Future, and associated podcast
How does the Army – as part of the Joint force – Build and Employ Teams to Compete, Penetrate, Disintegrate, and Exploit our Adversaries in the Future?, The Convergence: The Future of Talent and Soldiers with MAJ Delaney Brown, CPT Jay Long, and 1LT Richard Kuzma, and associated podcast
New Skills Required to Compete & Win in the Future Operational Environment; Warfare in the Parallel Cambrian Age, by Chris O’Connor; Character of Warfare 2035; The Future of War is Cyber! by CPT Casey Igo and CPT Christian Turley; Military Implications of Smart Cities, by Alexander Braszko, Jr.; and Integrated Sensors: The Critical Element in Future Complex Environment Warfare, by Dr. Richard Nabors
Quantum Surprise on the Battlefield? by proclaimed Mad Scientist Elsa B. Kania
Space: Challenges and Opportunities and Star Wars 2050, by proclaimed Mad Scientist Marie Murphy
Top Attack: Lessons Learned from the Second Nagorno-Karabakh War with COL John Antal (USA-Ret.), its associated podcast, Nowhere to Hide: Information Exploitation and Sanitization, and War Laid Bare, by Matthew Ader
Alternate Futures 2050: A Collection of Fictional Wartime Vignettes, by LTC Steve Speece; Kryptós by proclaimed Mad Scientist CPT Katherine Hathaway; AN41, by proclaimed Mad Scientist BG Jasper Jeffers, and Takeaways from the Mad Scientist Science Fiction Writing Contest 2019
>>>> REMINDER 1: Army Mad Scientist Fall / Winter Writing Contest: Crowdsourcing is an effective tool  for harvesting ideas, thoughts, and concepts from a wide variety of interested individuals, helping to diversify thought and challenge conventional assumptions. Army Mad Scientist seeks to crowdsource the intellect of the Nation (You!) with our Fall / Winter Writing Contest’s two themes — Back to the Future and Divergence – check out the associated writing prompts in the contest flyer and announcement, then get busy crafting your submissions — entries will be accepted in two formats:
for harvesting ideas, thoughts, and concepts from a wide variety of interested individuals, helping to diversify thought and challenge conventional assumptions. Army Mad Scientist seeks to crowdsource the intellect of the Nation (You!) with our Fall / Winter Writing Contest’s two themes — Back to the Future and Divergence – check out the associated writing prompts in the contest flyer and announcement, then get busy crafting your submissions — entries will be accepted in two formats:
Written essay (no more than 1500 words, please!)
Tweet @ArmyMadSci, using either #MadSciBacktotheFuture or #MadSciDivergence
We will pick a winner from each of these two formats!
 Contest Winners will be proclaimed official Mad Scientists and be featured in the Mad Scientist Laboratory. Semi-finalists of merit will also be published!
Contest Winners will be proclaimed official Mad Scientists and be featured in the Mad Scientist Laboratory. Semi-finalists of merit will also be published!
DEADLINE: All entries are due NLT 11:59 pm Eastern on January 10, 2022!
Any questions? Don’t hesitate to reach out to us — send us an eMail at: madscitradoc@gmail.com
>>>> REMINDER 2: Army Mad Scientist is pleased to support the Army and its Army People Synchronization Conference (APSC) in January 2022. To that end, we’re sponsoring the associated writing contest in support of this critical endeavor prioritizing the Army Team (Soldiers, Department of the Army Civilians, their dependents, and Soldiers for Life).
[NOTE: This is not to be confused with the aforementioned and separate Army Mad Scientist Fall / Winter Writing Contest, described in Reminder 1, above.]
Check out this APSC writing contest’s details here.
We will feature the winning submission and author in a future Mad Scientist Laboratory blog post. Additionally, we will compile it, along with other submissions of merit, and provide copies to Senior Army Leadership attending the Army People Synchronization Conference.
So get cracking — craft a 500 word composition over the Holiday Season addressing one or more of the writing prompts listed in the contest details and submit it via email with “APSC” in the subject line NLT 1700 EDT on 03 January 2022, to: madscitradoc@gmail.com
About the Authors: The Radio Research Group is a collection of experts in wireless mesh networking, electronic warfare, privacy, blockchain and decentralized systems. The group focuses particularly on fifth generation warfare, and the convergence of new technologies as they define modern conflict.
Disclaimer: The views expressed in this blog post do not necessarily reflect those of the U.S. Department of Defense, Department of the Army, Army Futures Command (AFC), or U.S. Army Training and Doctrine Command (TRADOC).



 Today’s provocative post by guest blogger Capt Martin Crilly, British Army, expands upon this theme to explore the challenges facing us in transforming for “post-digital hyper-war” — where kinetic engagements between exquisite, industrial age platforms may be rendered irrelevant by “more subtle, intellectual, and nuanced
Today’s provocative post by guest blogger Capt Martin Crilly, British Army, expands upon this theme to explore the challenges facing us in transforming for “post-digital hyper-war” — where kinetic engagements between exquisite, industrial age platforms may be rendered irrelevant by “more subtle, intellectual, and nuanced
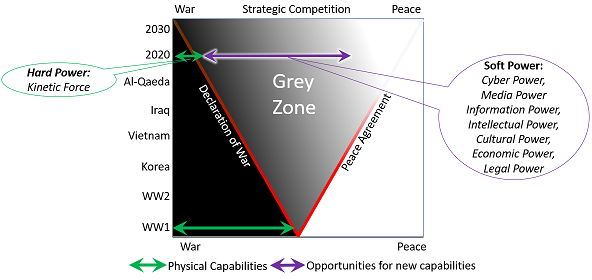

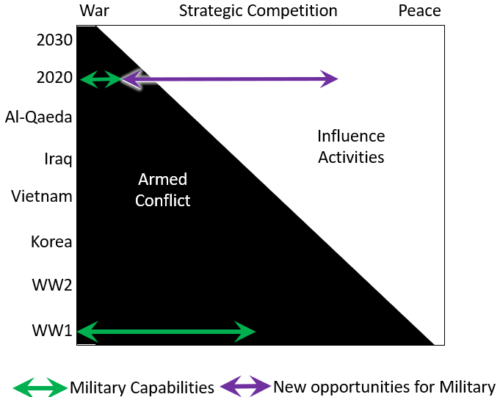
 transmission challenges with constant flux being the default. The human Multi-Domain Command and Control (MDC2) decider will soon be redundant, replaced and upgraded by a
transmission challenges with constant flux being the default. The human Multi-Domain Command and Control (MDC2) decider will soon be redundant, replaced and upgraded by a 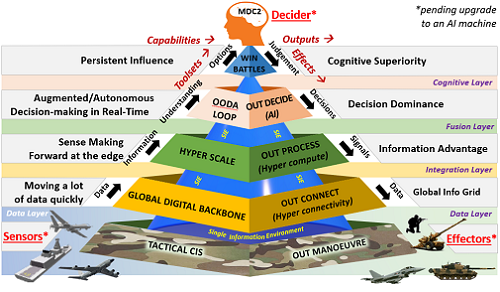
 Capt Martin Crilly is a British Army Reserve officer with 39 (Skinners) Signal Regiment in Bristol, England. His day job is as the Chief Architect & Engineering Authority for a large Defence Prime. His background is in contemporary ICT architecture, technology strategy, digital leadership with previous J2/J6 roles in BFC, ISS Ops Plans, GOSCC, DE&S Maritime and others. He has Masters in business, org design and is currently completing a Doctorate in InfoOps. Check out other similar articles by Capt Crilly in the
Capt Martin Crilly is a British Army Reserve officer with 39 (Skinners) Signal Regiment in Bristol, England. His day job is as the Chief Architect & Engineering Authority for a large Defence Prime. His background is in contemporary ICT architecture, technology strategy, digital leadership with previous J2/J6 roles in BFC, ISS Ops Plans, GOSCC, DE&S Maritime and others. He has Masters in business, org design and is currently completing a Doctorate in InfoOps. Check out other similar articles by Capt Crilly in the 
 Over the past two decades, China has transformed its People’s Liberation Army (PLA) through a holistic approach — modernizing its weaponry, force structure, and approaches to warfare, to include operations in the cyber and space domains, while improving its professional military education. Although Russia remains a near-peer threat, China has ascended to become the United States’ lone
Over the past two decades, China has transformed its People’s Liberation Army (PLA) through a holistic approach — modernizing its weaponry, force structure, and approaches to warfare, to include operations in the cyber and space domains, while improving its professional military education. Although Russia remains a near-peer threat, China has ascended to become the United States’ lone approach to competition, crisis, and conflict, enables it to challenge the United States across all domains and the Diplomatic, Information, Military, and Economic spheres.
approach to competition, crisis, and conflict, enables it to challenge the United States across all domains and the Diplomatic, Information, Military, and Economic spheres.





 Beginning in 2004, China’s PLA undertook a major
Beginning in 2004, China’s PLA undertook a major China has completed extensive research and development in
China has completed extensive research and development in  China will also leverage its AI proficiency in “
China will also leverage its AI proficiency in “


 targeted by our adversaries. The advent of the Internet of Things (IoT) and the proliferation of autonomy means a plethora of ever-smaller wireless internet and cellular antennae, paired with smaller and more prolific sensors, are embedded across public and industrial infrastructure. This web of networked sensors has, per Chris O’Connor in his superlative post
targeted by our adversaries. The advent of the Internet of Things (IoT) and the proliferation of autonomy means a plethora of ever-smaller wireless internet and cellular antennae, paired with smaller and more prolific sensors, are embedded across public and industrial infrastructure. This web of networked sensors has, per Chris O’Connor in his superlative post  Russia and China present a hemispheric threat to the U.S., having invested heavily in
Russia and China present a hemispheric threat to the U.S., having invested heavily in  — controlling electrical grids, water and sewage supply and treatment facilities, mass transit and rail, traffic controls, telecom and IT networks and systems, and more — lack appropriate cybersecurity protocols and defense capabilities to fend off threats from extraction tools, arbitrary code attacks (RCE), and
— controlling electrical grids, water and sewage supply and treatment facilities, mass transit and rail, traffic controls, telecom and IT networks and systems, and more — lack appropriate cybersecurity protocols and defense capabilities to fend off threats from extraction tools, arbitrary code attacks (RCE), and  advanced, automated systems (e.g., NOLAlytics in New Orleans, Metro21 Project in Pittsburgh) require increased connectivity and data storage capacity and capabilities – often relying on cloud services – which provides an opening for
advanced, automated systems (e.g., NOLAlytics in New Orleans, Metro21 Project in Pittsburgh) require increased connectivity and data storage capacity and capabilities – often relying on cloud services – which provides an opening for  Hospitals and medical centers are especially vulnerable to ransomware and cyber-attacks that compromise sensitive patient data, critical life support systems, and operating capabilities.
Hospitals and medical centers are especially vulnerable to ransomware and cyber-attacks that compromise sensitive patient data, critical life support systems, and operating capabilities. attack on Ukraine spilled beyond its target to inflict massive economic damage worldwide, crippling international shipping giant Maersk and causing an estimated $10 billion in economic damage. Russia had launched similar attacks previously — against Estonia in 2007 and Ukraine in 2015.
attack on Ukraine spilled beyond its target to inflict massive economic damage worldwide, crippling international shipping giant Maersk and causing an estimated $10 billion in economic damage. Russia had launched similar attacks previously — against Estonia in 2007 and Ukraine in 2015.
 While
While  China continues to build up a substantial
China continues to build up a substantial  According to an
According to an 
 Attacks on or sabotage of
Attacks on or sabotage of technology, exploiting our inherent biases and
technology, exploiting our inherent biases and 
 The Chief of Staff for the Army placed “People First” among the Army’s priorities.
The Chief of Staff for the Army placed “People First” among the Army’s priorities. If the Army’s human dimension meets the mission but does not also meet the needs of people, then the Army is not successful. This requires the broader People approach integrating holistic health and fitness, cohesive teams, removing unnecessary systematic barriers to individual success, and providing resources for Soldiers to meet their maximum potential. In doing so, we live up to our Army’s and Nation’s values, while ensuring mission success.
If the Army’s human dimension meets the mission but does not also meet the needs of people, then the Army is not successful. This requires the broader People approach integrating holistic health and fitness, cohesive teams, removing unnecessary systematic barriers to individual success, and providing resources for Soldiers to meet their maximum potential. In doing so, we live up to our Army’s and Nation’s values, while ensuring mission success. What does it mean to put People first in the 2035 time frame? How do advances in technology and society provide more opportunities and challenges?
What does it mean to put People first in the 2035 time frame? How do advances in technology and society provide more opportunities and challenges? Army Mad Scientist will feature the winning submission and author in a future Mad Scientist Laboratory blog post. Additionally, we will compile it, along with other submissions of merit, and provide copies to Senior Army Leadership attending the Army People Synchronization Conference in January 2022!
Army Mad Scientist will feature the winning submission and author in a future Mad Scientist Laboratory blog post. Additionally, we will compile it, along with other submissions of merit, and provide copies to Senior Army Leadership attending the Army People Synchronization Conference in January 2022!