[Editor’s Note: Mad Science Laboratory is pleased to excerpt below the Executive Summary from a DoD Biotechnologies for Health and Human Performance Council (BHPC) study group report entitled, Cyborg Soldier 2050: Human/Machine Fusion and the Implications for the Future of the DOD. This report, authored by Peter Emanuel, Scott Walper, Diane DiEuliis, Natalie Klein, James B. Petro, and James Giordano (proclaimed Mad Scientist); and published by the U.S. Army Combat Capabilities Development Command Chemical Biological Center (CCDC CBC), culminates a year-long assessment to forecast and evaluate the military implications of machines that are physically integrated with the human body to augment and enhance human performance over the next 30 years. This report summarizes this assessment and findings; identifies four potential military-use cases for new technologies in this area; and makes seven recommendations on how the U.S. should proceed regarding human/machine enhancement technologies. Enjoy!]
 A DoD BHPC study group surveyed a wide range of current and emerging technologies relevant to assisting and augmenting human performance in many domains. The team used this information to develop a series of vignettes as case studies for discussion and analysis including feasibility; military application; and ethical, legal, and social implication (ELSI) considerations.
A DoD BHPC study group surveyed a wide range of current and emerging technologies relevant to assisting and augmenting human performance in many domains. The team used this information to develop a series of vignettes as case studies for discussion and analysis including feasibility; military application; and ethical, legal, and social implication (ELSI) considerations.
Ultimately, the team selected four vignettes as being technically feasible by 2050 or earlier. The following vignettes are relevant to military needs and offer capabilities beyond current military systems:
-
 ocular enhancements to imaging, sight, and situational awareness;
ocular enhancements to imaging, sight, and situational awareness;- restoration and programmed muscular control through an optogenetic bodysuit
sensor web; - auditory enhancement for communication and protection; and
- direct neural enhancement of the human brain for two-way data transfer.
Although each of these technologies will offer the potential to incrementally enhance performance beyond the normal human baseline, the BHPC study group analysis suggested that the development of direct neural enhancements of the human brain for two-way data transfer would create a revolutionary advancement in future military capabilities. This technology is predicted to facilitate read/write capability between humans and machines and between humans through brain-to- brain interactions. These interactions would allow warfighters direct communication with unmanned and autonomous systems, as well as with other humans, to optimize command and control systems and operations. The potential for direct data exchange between human neural networks and microelectronic systems could revolutionize tactical warfighter communications, speed the transfer of knowledge throughout the chain of command, and ultimately dispel the “fog” of war. Direct neural enhancement of the human brain through neuro-silica interfaces could improve target acquisition and engagement and accelerate defensive and offensive systems.
brain interactions. These interactions would allow warfighters direct communication with unmanned and autonomous systems, as well as with other humans, to optimize command and control systems and operations. The potential for direct data exchange between human neural networks and microelectronic systems could revolutionize tactical warfighter communications, speed the transfer of knowledge throughout the chain of command, and ultimately dispel the “fog” of war. Direct neural enhancement of the human brain through neuro-silica interfaces could improve target acquisition and engagement and accelerate defensive and offensive systems.
Although the control of military hardware, enhanced situational awareness, and faster data assimilation afforded by direct neural control would fundamentally alter the battlefield by the year 2050, the other three cyborg technologies are also likely to be adopted in some form by warfighters and civil society. The BHPC study group predicted that human/machine enhancement technologies will  become widely available before the year 2050 and will steadily mature, largely driven by civilian demand and a robust bio-economy that is at its earliest stages of development in today’s global market. The global healthcare market will
become widely available before the year 2050 and will steadily mature, largely driven by civilian demand and a robust bio-economy that is at its earliest stages of development in today’s global market. The global healthcare market will
fuel human/machine enhancement technologies primarily to augment the loss of functionality from injury or disease, and defense applications will likely not drive the market in its later stages. The BHPC study group anticipated that the gradual introduction of beneficial restorative cyborg technologies will, to an extent, acclimatize the population to their use.
The BHPC study group projected that introduction of augmented human beings into the general population, DOD active duty personnel, and near-peer competitors will accelerate in the years following 2050 and will lead to imbalances, inequalities, and inequities in established legal, security, and ethical frameworks. Each of these technologies will afford some level of performance improvement to end users, which will widen the performance gap between enhanced and unenhanced individuals and teams. The BHPC study group analyzed case studies and posed a series of questions to drive its assessment of the impact to DOD programs, policies, and operations. The following are the resulting recommendations (not listed in order of priority):
1. DOD personnel must conduct global assessments of societal awareness and perceptions of human/machine enhancement technologies. A generalized perception exists in the United States that our adversaries are more likely to adopt technologies that U.S. populations are reluctant or unwilling to field  because of ethical concerns. However, the attitudes of our adversaries toward these technologies have never been verified. Societal apprehension following the introduction of new technologies can lead to unanticipated political barriers and slow domestic adoption, irrespective of value or realistic risk. Assessment of global attitudes will predict where it may be difficult to introduce new technologies because of sociopolitical barriers to adoption and when adversarial adoption of offset technologies may likely be more readily accepted.
because of ethical concerns. However, the attitudes of our adversaries toward these technologies have never been verified. Societal apprehension following the introduction of new technologies can lead to unanticipated political barriers and slow domestic adoption, irrespective of value or realistic risk. Assessment of global attitudes will predict where it may be difficult to introduce new technologies because of sociopolitical barriers to adoption and when adversarial adoption of offset technologies may likely be more readily accepted.
2. U.S. leadership should use existing and newly developed forums (e.g., NATO) to discuss impacts to interoperability with allied partners as we
approach the year 2050. 
This will help develop policies and practices that will maximize interoperability of forces. The rapid development pace of cyborg technologies has implications for interoperability of military forces. The DOD requirement to maintain interoperability with allied partners within NATO and other global alliance frameworks warrants the undertaking of efforts to align cyborg assets with existing allied partnership doctrine.
3. DOD should invest in the development of dynamic legal, security, and ethical frameworks under its control that anticipate emerging technologies.  The current legal, security, and ethical frameworks are insufficient because of the speed at which these technologies are developing in the United States and other nations around the world (allied and adversarial). Therefore, the DOD should support the development of forward-leaning policies (internal and external) that protect individual privacy, sustain security, and manage personal and organizational risk, while maximizing defined benefits to the United States and its allies and assets. Because operationalization of technology for national security is at the core of the DOD mission, these frameworks should be structured to be agile and responsive to new technologies developed within the United States or elsewhere.
The current legal, security, and ethical frameworks are insufficient because of the speed at which these technologies are developing in the United States and other nations around the world (allied and adversarial). Therefore, the DOD should support the development of forward-leaning policies (internal and external) that protect individual privacy, sustain security, and manage personal and organizational risk, while maximizing defined benefits to the United States and its allies and assets. Because operationalization of technology for national security is at the core of the DOD mission, these frameworks should be structured to be agile and responsive to new technologies developed within the United States or elsewhere.
4. Efforts should be undertaken to reverse negative cultural narratives of enhancement technologies. Across popular social and open-source media, literature, and film, the use of machines to enhance the physical condition of the human species has received a distorted and dystopian narrative in the name of  entertainment. A more realistic and balanced (if not more positive) narrative, along with transparency in the government’s approach to technology adoption, will serve to better educate the public, mitigate societal apprehensions, and remove barriers to productive adoption of these new technologies.* A more informed public will also help illuminate valid social concerns, such as those surrounding privacy, so that DOD personnel can develop mitigation strategies, whenever possible. Although not intrinsically a DOD mission, defense leadership should understand that negative public and social perceptions will need to be overcome, if these technologies are to be fielded.
entertainment. A more realistic and balanced (if not more positive) narrative, along with transparency in the government’s approach to technology adoption, will serve to better educate the public, mitigate societal apprehensions, and remove barriers to productive adoption of these new technologies.* A more informed public will also help illuminate valid social concerns, such as those surrounding privacy, so that DOD personnel can develop mitigation strategies, whenever possible. Although not intrinsically a DOD mission, defense leadership should understand that negative public and social perceptions will need to be overcome, if these technologies are to be fielded.

5. DOD personnel should conduct tabletop wargames and targeted threat assessments to determine the doctrine and tactics of allied and adversarial forces. Wargames are an established mechanism to gauge the impact of asymmetric technologies on tactics, techniques, and procedures. Tabletop exercises exploring varied scenarios of the integration and use of human/machine technologies by the United States or its adversaries will predict offset advantages, identify NATO and other allied organizational interoperability friction points, and inform senior military strategists and science and technology investors. DOD personnel should support these efforts using targeted intelligence assessments of this emerging field.
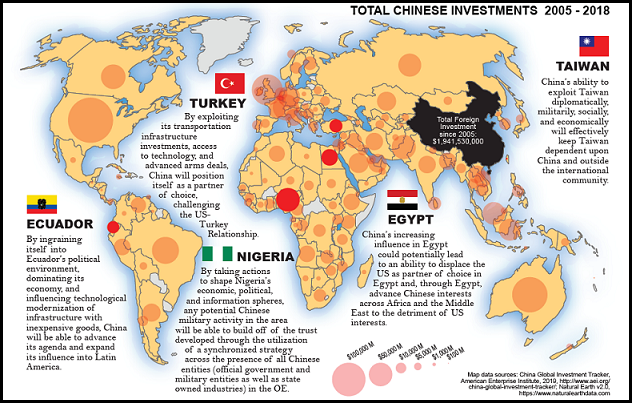
 6. The U.S. Government should support efforts to establish a whole-of-nation approach to human/machine enhancement technologies versus a whole-of-government approach. Federal and commercial investments in these areas are uncoordinated and are being outpaced by Chinese research and development efforts, which could result in a loss of U.S. dominance in human/machine enhancement technologies within the projected timeframe of this study. Near-peer dominance in the commercial sector will place U.S. interests in the defense sector at a disadvantage and could lead to an offset disadvantage in the realm of human/machine enhancement by the year 2050. A national effort to sustain U.S. dominance in cyborg technologies is in the best interests of the DOD and the nation.
6. The U.S. Government should support efforts to establish a whole-of-nation approach to human/machine enhancement technologies versus a whole-of-government approach. Federal and commercial investments in these areas are uncoordinated and are being outpaced by Chinese research and development efforts, which could result in a loss of U.S. dominance in human/machine enhancement technologies within the projected timeframe of this study. Near-peer dominance in the commercial sector will place U.S. interests in the defense sector at a disadvantage and could lead to an offset disadvantage in the realm of human/machine enhancement by the year 2050. A national effort to sustain U.S. dominance in cyborg technologies is in the best interests of the DOD and the nation.
 7. The DOD should support foundational research to validate human/ machine fusion technologies before fielding them and to track the long-term safety and impact on individuals and groups. The benefits afforded by human/machine fusions will be significant and will have positive quality-of-life impacts on humankind through the restoration of any functionality lost due to illness or injury. The military community will also see capability opportunities that will impact operations and training. As these technologies evolve, it is vital that the scientific and engineering communities move cautiously to maximize their potential and focus on the safety of our society. Commensurate investments in these areas will work to mitigate the misuse or unintended consequences of these technologies.
7. The DOD should support foundational research to validate human/ machine fusion technologies before fielding them and to track the long-term safety and impact on individuals and groups. The benefits afforded by human/machine fusions will be significant and will have positive quality-of-life impacts on humankind through the restoration of any functionality lost due to illness or injury. The military community will also see capability opportunities that will impact operations and training. As these technologies evolve, it is vital that the scientific and engineering communities move cautiously to maximize their potential and focus on the safety of our society. Commensurate investments in these areas will work to mitigate the misuse or unintended consequences of these technologies.

If you enjoyed this post, please see:
Cyborg Soldier 2050: Human/Machine Fusion and the Implications for the Future of the DOD complete report here.
… read the following related MadSci Lab blog posts:
-
- Linking Brains to Machines, and Use of Neurotechnology to the Cultural and Ethical Perspectives of the Current Global Stage, by Mr. Joseph DeFranco and Dr. James Giordano.
-
- Connected Warfare by COL James K. Greer (USA-Ret.)
… watch Dr. Alexander Kott‘s presentation The Network is the Robot, presented at the Mad Scientist Robotics, Artificial Intelligence, & Autonomy: Visioning Multi Domain Battle in 2030-2050 Conference, at the Georgia Tech Research Institute, 8-9 March 2017, in Atlanta, Georgia.
… and see Hank Greely‘s presentation on Future Legal and Ethical Implications of Bio Technology from the Mad Scientist Bio Convergence and Soldier 2050 Conference, at SRI International, 8-9 March 2018 in Menlo Park, California.
Disclaimer: The findings in this report are not an official policy or position of the Department of the Army, the National Defense University, the Department of Defense, or the U.S. Government.
* Wurzman R.; Yaden D.; Giordano J. Neuroscience Fiction as Eidola: Social Reflection and Neuroethical Obligations in Depictions of Neuroscience in Film. Camb Q Health Care Ethics-Neuroethics Now 2017, 26 (2), 292-312.



 the requisite new Knowledge, Skills, and Behaviors (KSBs) that our Soldiers and leaders will need to compete and win, and then program and implement the associated policy changes, improvements to training facilities, development of leader programs, and the integration of required equipment into the Multi-Domain force.]
the requisite new Knowledge, Skills, and Behaviors (KSBs) that our Soldiers and leaders will need to compete and win, and then program and implement the associated policy changes, improvements to training facilities, development of leader programs, and the integration of required equipment into the Multi-Domain force.] The
The  capabilities with hybrid strategies to expand the battlefield across all domains and create hemispheric threats challenging us from home stations to the Close Area. They seek to achieve national objectives through competition short of conflict and synthesize emerging technologies with military doctrine and operations to deploy capabilities that create
capabilities with hybrid strategies to expand the battlefield across all domains and create hemispheric threats challenging us from home stations to the Close Area. They seek to achieve national objectives through competition short of conflict and synthesize emerging technologies with military doctrine and operations to deploy capabilities that create  The
The  will empower potential foes, enabling them to achieve effects at a fraction of the cost of conventional weapons, without risking armed conflict.
will empower potential foes, enabling them to achieve effects at a fraction of the cost of conventional weapons, without risking armed conflict.
 The Army’s recent experience building a
The Army’s recent experience building a  The Army’s
The Army’s already are, or soon will be very common – narrow AI, app development and general programming, and smart devices – will yield a variety of intrinsic skills that recruits will have prior to entering the Army. Just like we no longer train Soldiers on how to use a computer, games like
already are, or soon will be very common – narrow AI, app development and general programming, and smart devices – will yield a variety of intrinsic skills that recruits will have prior to entering the Army. Just like we no longer train Soldiers on how to use a computer, games like





 Ethnic Russian minorities’ agitation against their respective governments in Estonia, Lithuania, and Latvia spike. Simultaneously, the Russian Government ratchets up tensions, with inflammatory statements of support for these ethnic Russian minorities in the Baltic States; coordinated movements and exercises by Russian ground, naval, and air forces adjacent to the region; and clandestine support to ethnic Russians in these States. The Russian Government started a covert campaign to shape people’s views about the threats against the Russian diaspora. More than 200,000 twitter accounts send 3.6 million tweets trending #protectRussianseverywhere. This sprawling Russian disinformation campaign is focused on building internal support for the Russian President and a possible military action. The U.S. and NATO respond…
Ethnic Russian minorities’ agitation against their respective governments in Estonia, Lithuania, and Latvia spike. Simultaneously, the Russian Government ratchets up tensions, with inflammatory statements of support for these ethnic Russian minorities in the Baltic States; coordinated movements and exercises by Russian ground, naval, and air forces adjacent to the region; and clandestine support to ethnic Russians in these States. The Russian Government started a covert campaign to shape people’s views about the threats against the Russian diaspora. More than 200,000 twitter accounts send 3.6 million tweets trending #protectRussianseverywhere. This sprawling Russian disinformation campaign is focused on building internal support for the Russian President and a possible military action. The U.S. and NATO respond… The 2nd Cav Regt is placed on alert; as it prepares to roll out of garrison for Poland, several videos surface across social media, purportedly showing the sexual assault of several underage German nationals by U.S. personnel. These disturbingly graphic
The 2nd Cav Regt is placed on alert; as it prepares to roll out of garrison for Poland, several videos surface across social media, purportedly showing the sexual assault of several underage German nationals by U.S. personnel. These disturbingly graphic  the Regiment. German political and legal authorities call for an investigation and host nation protests erupt outside the gates of Rose Barracks, Vilseck, disrupting the unit’s deployment.
the Regiment. German political and legal authorities call for an investigation and host nation protests erupt outside the gates of Rose Barracks, Vilseck, disrupting the unit’s deployment. Social media accounts are hacked/hijacked, with false threats by dependents to execute mass/school shootings, accusations of sexual abuse, hate speech posts by Leaders about their minority troops, and revelations of adulterous affairs between unit spouses.
Social media accounts are hacked/hijacked, with false threats by dependents to execute mass/school shootings, accusations of sexual abuse, hate speech posts by Leaders about their minority troops, and revelations of adulterous affairs between unit spouses. Russia’s GRU (Military Intelligence) employs AI Generative Adversarial Networks (GANs) to create fake persona injects that mimic select U.S. Active Army, ARNG, and USAR commanders making disparaging statements about their confidence in our allies’ forces, the legitimacy of the mission, and their faith in our political leadership. Sowing these injects across unit social media accounts, Russian Information Warfare specialists seed doubt and erode trust in the chain of command amongst a percentage of susceptible Soldiers, creating further friction in deployment preparations.
Russia’s GRU (Military Intelligence) employs AI Generative Adversarial Networks (GANs) to create fake persona injects that mimic select U.S. Active Army, ARNG, and USAR commanders making disparaging statements about their confidence in our allies’ forces, the legitimacy of the mission, and their faith in our political leadership. Sowing these injects across unit social media accounts, Russian Information Warfare specialists seed doubt and erode trust in the chain of command amongst a percentage of susceptible Soldiers, creating further friction in deployment preparations. As these units load at railheads or begin their road march towards their respective ports of embarkation,
As these units load at railheads or begin their road march towards their respective ports of embarkation,  navigation systems to cause sealift asset collisions and groundings at key maritime chokepoints. The fly-by-wire avionics are hacked on a departing C-17, causing a crash with the loss of all 134 Soldiers onboard. All C-17s are grounded, pending an investigation.
navigation systems to cause sealift asset collisions and groundings at key maritime chokepoints. The fly-by-wire avionics are hacked on a departing C-17, causing a crash with the loss of all 134 Soldiers onboard. All C-17s are grounded, pending an investigation. the alliance for the Multi-Domain Common Operating Picture. Spoofing of these systems leads to accidental air defense engagements, resulting in Blue-on-Blue fratricide or the downing of a commercial airliner, with additional civilian deaths on the ground from spent ordnance, providing more opportunities for Russian Information Operations to spread acrimony within the alliance and create dissent in public opinion back home.
the alliance for the Multi-Domain Common Operating Picture. Spoofing of these systems leads to accidental air defense engagements, resulting in Blue-on-Blue fratricide or the downing of a commercial airliner, with additional civilian deaths on the ground from spent ordnance, providing more opportunities for Russian Information Operations to spread acrimony within the alliance and create dissent in public opinion back home. across the net via bots, these instances further stoke anti-Baltic / anti-U.S. opinion amongst Russian-sympathetic and non-aligned populations alike.
across the net via bots, these instances further stoke anti-Baltic / anti-U.S. opinion amongst Russian-sympathetic and non-aligned populations alike. The release of deepfake videos showing Baltic security forces massacring ethnic Russians creates further division and causes some NATO partners to hesitate, question, and withhold their support, as required under Article 5. The alliance is rent asunder — Checkmate!
The release of deepfake videos showing Baltic security forces massacring ethnic Russians creates further division and causes some NATO partners to hesitate, question, and withhold their support, as required under Article 5. The alliance is rent asunder — Checkmate!
 The revolution in connected devices and virtual power projection will increase the potential for adversaries to target our installations. Hyper-connectivity increases the
The revolution in connected devices and virtual power projection will increase the potential for adversaries to target our installations. Hyper-connectivity increases the  The
The
 Passive sensing, especially when combined with artificial intelligence and big-data techniques may routinely outperform active sensors, leading to a counter-reconnaissance fight between autonomous sensors and countermeasures – “a robot-on-robot affair.” These capabilities will be augmented by increasingly sophisticated civilian capabilities, where commercial
Passive sensing, especially when combined with artificial intelligence and big-data techniques may routinely outperform active sensors, leading to a counter-reconnaissance fight between autonomous sensors and countermeasures – “a robot-on-robot affair.” These capabilities will be augmented by increasingly sophisticated civilian capabilities, where commercial  imagery services, a robust and mature Internet of Things, and near unlimited processing power generate a battlespace that is more transparent than ever before. This
imagery services, a robust and mature Internet of Things, and near unlimited processing power generate a battlespace that is more transparent than ever before. This The proliferation of intelligent munitions will enable strikers to engage targets at greater distances, collaborate in teams to seek out and destroy designated targets, and defeat armored and other hardened targets, as well as defiladed and entrenched targets.
The proliferation of intelligent munitions will enable strikers to engage targets at greater distances, collaborate in teams to seek out and destroy designated targets, and defeat armored and other hardened targets, as well as defiladed and entrenched targets. Swarms of small, cheap, scalable, and disposable unmanned systems will be used both offensively and defensively, creating
Swarms of small, cheap, scalable, and disposable unmanned systems will be used both offensively and defensively, creating

 extreme weather impacting installations, increased resource scarcity and food insecurity, climate migration increasing the number of refugees and internally displaced peoples, and the Arctic as a
extreme weather impacting installations, increased resource scarcity and food insecurity, climate migration increasing the number of refugees and internally displaced peoples, and the Arctic as a  Quantum Computing: The expansion of
Quantum Computing: The expansion of Power: Proliferation of electric/battery powered vehicles, laser charging,
Power: Proliferation of electric/battery powered vehicles, laser charging,  Information Environment: Instantaneous recall, sensor-saturated environment, unmanned asset intelligence collection, algorithmic processing of high volumes of information, and
Information Environment: Instantaneous recall, sensor-saturated environment, unmanned asset intelligence collection, algorithmic processing of high volumes of information, and