[Editor’s Note: Today’s post is excerpted from last month’s edition (October 2020) of the OE Watch, which in turn analyzes two articles from Jiefangjun Bao (the People’s Liberation Army [PLA] Daily), published this past August and September.
 The first article complements our on-going series of Mad Scientist Robotics and Autonomy Virtual Events and explores Chinese unmanned systems concepts and technologies and potential strategies for employing them to achieve combat superiority on the future battlefield.
The first article complements our on-going series of Mad Scientist Robotics and Autonomy Virtual Events and explores Chinese unmanned systems concepts and technologies and potential strategies for employing them to achieve combat superiority on the future battlefield.
The second article examines how the PLA could achieve cyber and electronic dominance, employing the electromagnetic spectrum to deceive, lull, and feint its adversaries.
Taken together, these articles provide valuable insights into how China’s defense establishment is thinking about countering the U.S. Army’s current force, the Multi-Domain Operations (MDO)-Capable Force in 2028, and the MDO-Ready Force in 2035 — Read on!]
1. China: “New Concepts” in Unmanned Combat
OE Watch Commentary: Evolving concepts in unmanned combat and new technologies have prompted two Chinese military strategists to explore different potential strategies that might be used in unmanned combat operations. In the article excerpt (below), published in Jiefangjun Bao, they describe ways China might achieve superiority through unmanned operations on the future battlefield.
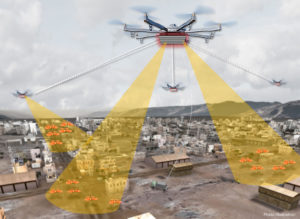
The authors offer a brief snapshot of swarming operations by pointing out that such operations are supported by network information systems. The advantages of swarming operations are in intelligence, decision-making, coordination, and sheer numbers. According to the authors, each unit (drone) is assigned a specific role. For example, some drones will be fitted for various modes of search or surveillance. Others might be assigned an attack function. The units work together through networked operations to carry out their respective missions. The authors explain that through these unique applications, swarms can carry out “omnidirectional defense penetration, distributed killing, and group defense.” They write that in “omnidirectional defense penetration, massive numbers of drones can carry out simultaneous penetration.” It can be both multidirectional and three-dimensional. In “distributed killing,” each platform has its own unique function and role: reconnaissance and detection, electronic interference, network attack, or strike.

These drones will then work together to collectively pursue a single high-value target or a group of targets in a specific area. In pursuing these targets, according to the authors, a swarm will be able to carry out multi-domain, multi-dimensional attacks from multiple directions. Finally, the authors explain that in carrying out group defense, a swarm can build a smart, self-adaptive defensive system to create a protective “bubble” around a main assault force or important targets. Through each drone’s respective functions and their interaction with the other units, they can then, for example, rapidly intercept targets. They can also help provide defense and counter enemy drone swarms.

In the next section of the article, the authors lay out a strategy that is somewhat analogous to the game of Chess. The operations, which they refer to as “mother ship-launched operations,” are large-scale, flexible operations in which large sea- or air-based, manned or unmanned combat platforms transport the drones to a specific location. After launching the drones, the mother ships can provide comprehensive background support, such as launch, retrieval, and command and control. These operations can take place on land, in the air, or at sea.

According to the authors, mother ship-launched operations are advantageous because they can operate at long-range while also engaging in close up combat. Mother ship-launched operations are like “using a ‘rook’ to carry a ‘pawn’ to mobilize for combat, with the ‘rook’s’ easy maneuverability improving the ‘pawn’s mobilization speed and operational flexibility.” Mother ship-launched operations are also described as more versatile. They can more efficiently perform emergency response and intervention, their operations can deliver “sustained suppression and attacks,” and they can coordinate operations in multiple locations.
The authors also discuss the benefits of increasing interoperability between manned combat platforms and unmanned platforms. In more traditional operations the battlefield might be controlled through a control center located at the rear. However, they explain that by increasing the interoperability between manned and unmanned platforms, control is spread throughout the battlefield to achieve a “more direct exchange of battlefield information, operational support, and action coordination.”
It is worth noting that while the authors go in-depth in their discussion of unmanned combat operations, they do not once mention artificial intelligence (AI), which is an area of great interest in China. End OE Watch Commentary (Hurst)
Source: Zhao Xiangang and Zhang Tieqiang, “新概念牵引无人作战新方向 (New Concept Leads to New Directions in Unmanned Combat),” Jiefangjun Bao, 1 September 2020, http://www.81.cn/tz/2020-09/01/content_9894213.htm
New Concept Leads to New Directions in Unmanned Combat
The cluster effect of swarm operations enables a wholeness in combat operations that cannot be achieved by a single platform. Swarm operations have the following advantages. The first [advantage] is an advantage in intelligence… The second [advantage] is an advantage in decision making…The third [advantage] is an advantage in coordination… The fourth [advantage] is an advantage in numbers. … Against a target, a swarm can execute a multidirectional, saturated combined attack that may be continuous or simultaneous, achieving the effect of the “small but numerous” defeating the “big but few.”
A swarm is the aggregate of a large number of intelligent unmanned platforms with different functions, with a unique application method that is not possessed by any single weapon system. First, a swarm can carry out omnidirectional defense penetration.… Next, a swarm can carry out  distributed killing… Third, a swarm can carry out group defense… A swarm not only can “intercept many [targets] with few [drones],” it can also “intercept many [targets] with many [drones],” with a wide range of interception and a high success rate. This constitutes an important application method in the future for coordinating the execution of air defense and anti-missile operations, defending important targets at the endpoint, and countering enemy drone swarm attacks.
distributed killing… Third, a swarm can carry out group defense… A swarm not only can “intercept many [targets] with few [drones],” it can also “intercept many [targets] with many [drones],” with a wide range of interception and a high success rate. This constitutes an important application method in the future for coordinating the execution of air defense and anti-missile operations, defending important targets at the endpoint, and countering enemy drone swarm attacks.
Mother ship-launched operations involve the use of large, sea- or air-based, manned or unmanned combat platforms as transport carriers to provide support for the mobilization, projection, and retrieval of, command and control over, and comprehensive support for, various types of unmanned systems on land, at sea, and in the air. Such operations enable the long-range mobilization, multi-domain deployment, and coordinated use of unmanned systems, particularly small- or micro-sized unmanned systems, thereby giving full play to such systems’ overall combat effectiveness.
The following advantages exist with unmanned platforms relying on a mother ship to carry out mobile operations and support services, as opposed to relying on the rear to provide command and control and support services. The first [advantage] is an advantage in mobilization… The second [advantage] is the advantage of clusters.… The third [advantage] is an advantage in [the diversity of] missions…
Mother ship-launched operations represent the organic combination of the advantages of a mother ship and of unmanned platforms, leading to more versatile application methods. First, mother ship-launched operations can perform emergency response and intervention…Second, mother ship-launched operations can deliver sustained suppression and attacks… Third, mother ship-launched operations can execute coordinated operations at multiple locations…With dispersed unmanned platforms taking actions simultaneously at multiple locations, it [the use of mother ships] also results in dispersal of the enemy’s forces and a decrease in the enemy’s defensive capabilities.
By increasing the interoperability of manned combat platforms and unmanned combat platforms, manned/unmanned coordinated operations achieve an even more direct exchange of battlefield information, operational support, and action coordination, accomplishing unified organization and integrated combat between manned and unmanned platforms, and fully, exploiting the complementary advantages of manned and unmanned combat forces.
2. China: Seizing Cyber and Electronic Dominance on the Battlefield
OE Watch Commentary: The Chinese recognize that electronic and cyber warfare complement each other and they are interested in the role that the electromagnetic spectrum plays for both. This has prompted three Chinese military strategists to carefully examine ways to achieve cyber and electronic dominance on the battlefield. In the following excerpted article, published in Jiefangjun Bao, the authors explain that in order to achieve cyber and electronic dominance on the battlefield, it is important to focus on influencing or breaking the enemy psychology and perception system. This can be done by employing electronic deception to “conceal the real by displaying the fake,” to “employ feint cooperation to give out a false impression to lure the enemy,” and to “appear as the enemy least expects in order to secure victory by surprise moves.”

The authors envision future informatized warfare as being complex with multiple enemy targets. They write that it is impossible for cyber and electronic forces to cover all the bases and attack on all fronts. Therefore, cyber and electronic energy should be selectively harnessed and controlled to dominate or attack prioritized targets. One of the measures to accomplish this, they write, is through “flexible electromagnetic maneuver.” This is where every platform not only collects data on the enemy’s signals and informs the network, but they also dial up and down their own emissions to deceive the adversary. Another measure is “vast area suppression,” in which enemy units are suppressed to prevent them from taking action. The authors then explain that a combination of cyber and electronic energy can strike enemy core points, destroy enemy nodes, break enemy system of systems, and effectively support the main mission of the combined arms troops.

The authors make a surprisingly simplistic argument that the main way to seize cyber and electronic dominance on the battlefield is by resorting to electronic warfare and cyber warfare themselves. Electronic warfare, they say, should be used to “pool energy for external harassment.” Patterns of “electromagnetic separation, electromagnetic obstruction, and electromagnetic destructions” might be used to completely or partially incapacitate the enemy’s command system. For cyber warfare, which pools information for “internal attack,” the authors recommend implanting viruses, logic bombs, and malicious software into the enemy’s internal battlefield information network. They can also be combined with firepower to enhance target-specific strikes and to paralyze the enemy’s mission.
The authors conclude that it is impossible to attack all areas. Therefore, the optimal targets to strike must be carefully chosen to subdue the enemy. In selecting targets, the priority must be to attack the enemy’s core combat system of systems. Forceful cyber and electronic attacks must be launched straight into the enemy’s command center to destroy it. Finally, they explain that everything should be done to weaken or destroy the enemy’s combat system of systems from the top down. Important targets, they note, include information nodes, communication hubs, and key networks. End OE Watch Commentary (Hurst)
Source: Liu Guojun et al, “如何有效夺取战场网电制权 (How to Effectively Seize Cyber and Electronic Dominance on the Battlefield),” Jiefangjun Bao, 4 August 2020, http://www.81.cn/jfjbmap/content/2020-08/04/content_267666.htm
How to Effectively Seize Cyber and Electronic Dominance on the Battlefield
In recent years, with the rapid advancement of information technology, the roles of the electromagnetic field and cyberspace have become more prominent. Operations aiming to seize cyber and electronic  dominance on the battlefield by means of electronic warfare and cyber warfare have especially become the focus of the battle between two opposing forces. In future operations, there should be more focus on electronic and cyber space, explore the winning mechanisms and approaches to seize cyber and electronic dominance on the battlefield, scientifically harness and give play to the advantages of the cyber and electronic forces on the battlefield, ensure the establishment of information advantages in the main direction, important areas, and key moments on the battlefield, and create favorable conditions to firmly grasp the initiative on the battlefield.
dominance on the battlefield by means of electronic warfare and cyber warfare have especially become the focus of the battle between two opposing forces. In future operations, there should be more focus on electronic and cyber space, explore the winning mechanisms and approaches to seize cyber and electronic dominance on the battlefield, scientifically harness and give play to the advantages of the cyber and electronic forces on the battlefield, ensure the establishment of information advantages in the main direction, important areas, and key moments on the battlefield, and create favorable conditions to firmly grasp the initiative on the battlefield.
… To seize cyber and electronic dominance on the battlefield is to focus on influencing or breaking the enemy psychological and perception system. Taking into consideration the features of the cyber and electronic space — ease of concealment and strong penetrability and following the operation rule of “strength stemming from the mind,” efforts should be made to fully tap into the arena of employing cyber and electronic strategies and try all means to lull the enemy’s alertness and crush the enemy’s mind, thus resulting in misinformation, misjudgment, and improper decision-making for the enemy.
Employ electronic deception to conceal the real by displaying the fake…
Employ feint cooperation to give out a false impression to lure the enemy…
Appear as the enemy least expects it to secure victory by surprise moves…
In future informatized warfare, there will be multiple enemy targets, together with the enemy consummate system of systems during operations. It is impossible and unnecessary for the cyber and electronic forces to cover all bases and attack on all fronts. Efforts should be made to give full play to factors such as flexible electromagnetic maneuver, vast area of suppression, and controllable cyber and electronic energy, and dynamically combine the cyber and electronic energy on the battlefield based on the actual needs of the battlefield in different phases and time segments, so as to strike the enemy core points, destroy the enemy nodes, break the enemy system of systems, and effectively support the main mission of the combined arms troops.

The main ways to seize cyber and electronic dominance on the battlefield are electronic warfare and cyber warfare. In future operations, it is important to technically and tactically integrate the employment of electronic warfare and cyber warfare to allow both means of attack to give play to their respective advantages in coordinated operations, so as to achieve the best results.
…The organic integration of cyber and electronic operations and firepower strikes not only can play up the combat mechanism of soft-hard integration and the synergy of effectiveness to achieve the organic combination of “decapitating and blinding” and “physically destroying and damaging,” but also can achieve the concentrated release of combat effectiveness, so as to establish the dominant advantage in system-of-systems confrontations and contribute to the acceleration of combat development.
Focus on crucial points to subdue the enemy and select optimal targets to strike. It is a must to give the priority to the attack on the core part of the enemy combat system of systems, launch forceful cyber and electronic attack straight on the enemy command center to destroy it, and try all means to weaken or disintegrate the enemy combat system of systems from top down; to give the priority to the attack on the enemy important battlefield pillars, such as information nodes, communication hubs, and key networks, and achieve the chain effect of “one slight move affects the whole situation”; and to firmly pinpoint the deficiencies of the enemy combat system of systems, try to tackle the weaknesses first, and create conditions for the launch of a preemptive cyber and electronic attack on the enemy and the favorable combat development.
If you enjoyed this post, check out the following:
 OE Watch, October 2020 issue, by the TRADOC G-2’s Foreign Military Studies Office (FMSO), featuring the two aforementioned articles, along with a host of other items of interest on the OE.
OE Watch, October 2020 issue, by the TRADOC G-2’s Foreign Military Studies Office (FMSO), featuring the two aforementioned articles, along with a host of other items of interest on the OE.
Content from the three previous webinars in our Mad Scientist Robotics and Autonomy Series of Virtual Events
China: Our Emergent Pacing Threat
Competition in 2035: Anticipating Chinese Exploitation of Operational Environments
“Intelligentization” and a Chinese Vision of Future War
The PLA: Close Combat in the Information Age and the “Blade of Victory
Jomini’s Revenge: Mass Strikes Back! by proclaimed Mad Scientist Zachery Tyson Brown
How Big of a Deal are Drone Swarms? by proclaimed Mad Scientist Zachary Kallenborn



