[Editor’s Note: Mad Scientist Laboratory is pleased to publish the following post by returning guest blogger and proclaimed Mad Scientist Ms. Marie Murphy, addressing how advances in various technologies have the potential to upset the international order and empower individuals and non-state actors. Read on to learn who will be the winners and losers in this technological upheaval!]
 Access to new and advanced technologies has the potential to upset the current power dynamic of the world. From the proliferation of smartphones to commercially available software and hardware, individuals and states that were previously discounted as threats now have the potential to launch sophisticated attacks against powerful international players. Power will no longer remain in the upper echelons of society, where it is primarily held by national governments, multinational corporations, and national news services. These groups are losing their information dominance as individuals, local authorities, and other organizations now have the ability to access and distribute unfiltered information at their fingertips.1
Access to new and advanced technologies has the potential to upset the current power dynamic of the world. From the proliferation of smartphones to commercially available software and hardware, individuals and states that were previously discounted as threats now have the potential to launch sophisticated attacks against powerful international players. Power will no longer remain in the upper echelons of society, where it is primarily held by national governments, multinational corporations, and national news services. These groups are losing their information dominance as individuals, local authorities, and other organizations now have the ability to access and distribute unfiltered information at their fingertips.1
 A historical example of technology altering the balance of power are cassette tapes. Ayatollah Khomeini used cassette tape recordings to deliver sermons and direct the Iranian Revolution when exiled in Paris, while the United States observed the use of cassette tapes by the USSR in the spreading of communist propaganda.2 A new technology in the hands of empowered individuals and states allowed for events to transpire that otherwise would not have been possible with the same speed and effectiveness. Adaptation of technology created new agency for actors to direct movements from thousands of miles away, forever shaping the course of history.
A historical example of technology altering the balance of power are cassette tapes. Ayatollah Khomeini used cassette tape recordings to deliver sermons and direct the Iranian Revolution when exiled in Paris, while the United States observed the use of cassette tapes by the USSR in the spreading of communist propaganda.2 A new technology in the hands of empowered individuals and states allowed for events to transpire that otherwise would not have been possible with the same speed and effectiveness. Adaptation of technology created new agency for actors to direct movements from thousands of miles away, forever shaping the course of history.  A more contemporary example is the role of smartphones and social media in the Arab Spring. These new disruptive technologies enabled the organizing of protests and the broadcasting of videos in real time, eclipsing traditional journalism’s ability to report.3
A more contemporary example is the role of smartphones and social media in the Arab Spring. These new disruptive technologies enabled the organizing of protests and the broadcasting of videos in real time, eclipsing traditional journalism’s ability to report.3
Near-term Analysis:
 Technologically sophisticated international actors, such as the United States and the European Union, will maintain the capacity to manage the growth and use of technology within their own borders without adversely affecting governance. However, the increased availability of these technologies may strain civil/government relations in both developing countries and authoritarian systems.4 Technologies such as smartphones and the ability to instantly transmit data may force governments to be accountable for their actions, especially if their abuses of power are recorded and distributed globally by personal devices. At the same time however, “smart” devices may also be used by governments as instruments of social control, repression, and misinformation.
Technologically sophisticated international actors, such as the United States and the European Union, will maintain the capacity to manage the growth and use of technology within their own borders without adversely affecting governance. However, the increased availability of these technologies may strain civil/government relations in both developing countries and authoritarian systems.4 Technologies such as smartphones and the ability to instantly transmit data may force governments to be accountable for their actions, especially if their abuses of power are recorded and distributed globally by personal devices. At the same time however, “smart” devices may also be used by governments as instruments of social control, repression, and misinformation.
 Technology also affords non-state actors new methods for recruiting and executing operations. Technology-enabled platforms have allowed these groups to network near instantaneously across borders and around the world in a manner that would have been impossible prior to the advent of the digital age.5 A well-known example is the use of social media platforms by terrorist groups such as al-Qaeda and ISIS for propaganda and recruitment. These groups and others, such as Hezbollah and the political opposition in Venezuela, have deployed drones for both reconnaissance and as lethal weapons.6 The availability of these information age technologies has enabled these groups to garner more power and control than similar organizations could have done in the past, posing a real threat to major international actors.
Technology also affords non-state actors new methods for recruiting and executing operations. Technology-enabled platforms have allowed these groups to network near instantaneously across borders and around the world in a manner that would have been impossible prior to the advent of the digital age.5 A well-known example is the use of social media platforms by terrorist groups such as al-Qaeda and ISIS for propaganda and recruitment. These groups and others, such as Hezbollah and the political opposition in Venezuela, have deployed drones for both reconnaissance and as lethal weapons.6 The availability of these information age technologies has enabled these groups to garner more power and control than similar organizations could have done in the past, posing a real threat to major international actors.
Distant Future Analysis:
 There is an extremely high chance of future political disruption stemming from technological advancement. There are some who predict a non-polar power balance emerging. In this scenario, the world is dominated by dozens of technologically capable actors with various capabilities. “Hyperconnected,” developed states such as Sweden, Finland, and Israel may become greater international players and brokers of technologically backed global power. “Partially-connected” nations, today’s developing world, will face multiple challenges and could possibly take advantage of new opportunities due to the proliferation of technology. Technologically empowered individuals, groups, or neighboring states may have the ability to question or threaten the legitimacy of an otherwise weak government. However, in these “partially-connected” states, technology will serve to break down social barriers to equalize social discourse among all strata of society. Other predictions suggest the dissolution of national boundaries and the creation of an “interconnected state” comprised of different national laws without borders in a virtual space.7
There is an extremely high chance of future political disruption stemming from technological advancement. There are some who predict a non-polar power balance emerging. In this scenario, the world is dominated by dozens of technologically capable actors with various capabilities. “Hyperconnected,” developed states such as Sweden, Finland, and Israel may become greater international players and brokers of technologically backed global power. “Partially-connected” nations, today’s developing world, will face multiple challenges and could possibly take advantage of new opportunities due to the proliferation of technology. Technologically empowered individuals, groups, or neighboring states may have the ability to question or threaten the legitimacy of an otherwise weak government. However, in these “partially-connected” states, technology will serve to break down social barriers to equalize social discourse among all strata of society. Other predictions suggest the dissolution of national boundaries and the creation of an “interconnected state” comprised of different national laws without borders in a virtual space.7
 Democracy itself is evolving due to technological innovation. Increasing concerns about the roles of privacy, big data, internet security, and artificial intelligence in the digital age raise the following questions: how much does technology influence and control the lives of people in democratic countries, and what effect does this have on politics? Algorithms control the advertisements on the internet based on users’ search history, the collection and sale of personal data, and “fake news” which affects the opinions of millions.8 While these technologies provide convenience in the daily lives of internet-connected citizens, such as recommending items for purchase on Amazon and other platforms, they also lead to an erosion of public trust, a pillar upon which democracy is founded. Democracies must remain vigilant regarding how emerging technologies influence and affect their people and how governments use technology to interact with its citizens.
Democracy itself is evolving due to technological innovation. Increasing concerns about the roles of privacy, big data, internet security, and artificial intelligence in the digital age raise the following questions: how much does technology influence and control the lives of people in democratic countries, and what effect does this have on politics? Algorithms control the advertisements on the internet based on users’ search history, the collection and sale of personal data, and “fake news” which affects the opinions of millions.8 While these technologies provide convenience in the daily lives of internet-connected citizens, such as recommending items for purchase on Amazon and other platforms, they also lead to an erosion of public trust, a pillar upon which democracy is founded. Democracies must remain vigilant regarding how emerging technologies influence and affect their people and how governments use technology to interact with its citizens.
 The changing geopolitical dynamics of the world is inextricably linked with economic power, and increasing economic power is positively correlated with technological advancement. Power is becoming more diffused as Brazil, Russia, India, China, and South Africa (i.e., the BRICS states), the Philippines, Mexico, Turkey, and others develop stronger economies. States with rising economic power may begin to shun traditional global political and economic institutions in favor of regional institutions and bilateral agreements.9 There will be many more emerging markets competing for market share,10 driving up competition and forcing greater innovation and integration to remain relevant.
The changing geopolitical dynamics of the world is inextricably linked with economic power, and increasing economic power is positively correlated with technological advancement. Power is becoming more diffused as Brazil, Russia, India, China, and South Africa (i.e., the BRICS states), the Philippines, Mexico, Turkey, and others develop stronger economies. States with rising economic power may begin to shun traditional global political and economic institutions in favor of regional institutions and bilateral agreements.9 There will be many more emerging markets competing for market share,10 driving up competition and forcing greater innovation and integration to remain relevant.
 One of the major factors of the changing economic landscape is the growth of robotics use. Today these technologies are exclusive to world economic leaders but are likely to proliferate as more technological advancements make them cost-effective for a wider range of industries and companies. The adaptation of artificial intelligence will also dictate the future success of businesses in developed and emerging economies. It is important for governments to consider “retraining programs” for those workers laid off by roboticization and AI domination of their career fields.11 Economically dominant countries of the future will be driven by technology and hold the majority of political power in the political arena. These states will harness these technologies and use them to increase their productivity while training their workforce to participate in a technologically aided market.
One of the major factors of the changing economic landscape is the growth of robotics use. Today these technologies are exclusive to world economic leaders but are likely to proliferate as more technological advancements make them cost-effective for a wider range of industries and companies. The adaptation of artificial intelligence will also dictate the future success of businesses in developed and emerging economies. It is important for governments to consider “retraining programs” for those workers laid off by roboticization and AI domination of their career fields.11 Economically dominant countries of the future will be driven by technology and hold the majority of political power in the political arena. These states will harness these technologies and use them to increase their productivity while training their workforce to participate in a technologically aided market.
The Winners and Losers of the Future:
Winners:
- Countries with stable governments and emerging economies which are able to adapt to the rapid pace of technological innovation without severe political disruption.
- Current international powers which invest in the development and application of advanced technologies.
Losers:
- Countries with fragile governments which can be overpowered by citizens, neighbors, or non-state actors armed with technology and authoritarian regimes who use technology as a tool of repression.
- Traditional international powers which put themselves at risk of losing political and financial leverage if they only work to maintain the status quo. Those systems that do not adapt will struggle to remain relevant in a world dominated by a greater number of powers who fall into the “winners” category.
Conclusion
Modern power players in the world will have to adapt to the changing role of technology, particularly the influence of technology-empowered individuals. Technology will change how democracies and other political systems operate both domestically and on the world stage. The major international players of today will also have to accept that rising economic powers will gain more influence in the global market as they are more technologically enabled. As power becomes more diluted when states gain equalizing technology, the hegemony of the current powers that lead international institutions will begin to lose relevancy if they do not adapt.
If you enjoyed this post, please also see:
… and Ms. Murphy‘s previous posts:
- The Final Frontier: Directed Energy Applications in Outer Space
- Star Wars 2050
- Virtual Nations: An Emerging Supranational Cyber Trend
… and crank up Bob Marley and the Wailers‘ Get Up, Stand Up!
Marie Murphy is a junior at The College of William and Mary in Virginia, studying International Relations and Arabic. She is a regular contributor to the Mad Scientist Laboratory; interned at Headquarters, U.S. Army Training and Doctrine Command (TRADOC) with the Mad Scientist Initiative during the Summer of 2018; and is currently a Research Fellow for William and Mary’s Project on International Peace and Security.
1 Laudicina, Paul A, and Erik R Peterson. “Divergence, Disruption, and Innovation: Global Trends 2015–2025.” Strategy, A T Kearney, www.middle-east.atkearney.com/strategy/featured-article/-/asset_publisher/KwarGm4gaWhz/content/global-trends-2015-2025-divergence-disruption-and-innovation/10192?inheritRedirect=false&redirect=http://www.middle-east.atkearney.com/strategy/featured-article?p_p_id=101_INSTANCE_KwarGm4gaWhz&p_p_lifecycle=0&p_p_state=normal&p_p_mode=view&p_p_col_id=column-2&p_p_col_count=1.
2 Schmidt, Eric, and Jared Cohen. “The Digital Disruption.” Foreign Affairs, Foreign Affairs Magazine, 27 Oct. 2010, www.foreignaffairs.com/articles/2010-10-16/digital-disruption.
3 Duffy, Matt J. “Smartphones in the Arab Spring.” Academia.edu – Share Research, 2011, www.academia.edu/1911044/Smartphones_in_the_Arab_Spring
4 China is a unique case here because it’s a major developer of technology and counter-technology systems which block the use of certain devices, applications, or programs within their borders. But Chinese people do find loopholes and other points of access in the system, defying the government.
5 Schmidt, Eric, and Jared Cohen. “The Digital Disruption.” www.foreignaffairs.com/articles/2010-10-16/digital-disruption.
6 “Drone Terrorism Is Now a Reality, and We Need a Plan to Counter the Threat.” International Security: Fragility, Violence and Conflict, World Economic Forum, 20 Aug. 2018, www.weforum.org/agenda/2018/08/drone-terrorism-is-now-a-reality-and-we-need-a-plan-to-counter-the-threat.
7 Schmidt, Eric, and Jared Cohen. “The Digital Disruption.” www.foreignaffairs.com/articles/2010-10-16/digital-disruption.
8 Unver, Hamid Akin. “Artificial Intelligence, Authoritarianism and the Future of Political Systems.” SSRN, EDAM Research Reports, 2018, 26 Feb. 2019, https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3331635.
9 Laudicina, Paul A, and Erik R Peterson. “Divergence, Disruption, and Innovation: Global Trends 2015–2025.”
10 Stowell, Joshua. The Emerging Seven Countries Will Hold Increasing Levels of Global Economic Power by 2050. Global Security Review, 26 Apr. 2018, www.globalsecurityreview.com/will-global-economic-order-2050-look-like/.
11 Laudicina, Paul A, and Erik R Peterson. “Divergence, Disruption, and Innovation: Global Trends 2015–2025.”





 Given what is sure to be a contentious and polarizing congressional debate, the Defense Intelligence Agency’s Challenges to Security in Space provides a useful unclassified reference outlining our near-peer adversaries’ (China and Russia) space strategy, doctrine, and intent; key space and counterspace organizations; and space and counterspace capabilities. These latter capabilities are further broken out into: space launch capabilities; human spaceflight and space exploration; Intelligence, Surveillance, and Reconnaissance (ISR); navigation and communications; and counterspace.
Given what is sure to be a contentious and polarizing congressional debate, the Defense Intelligence Agency’s Challenges to Security in Space provides a useful unclassified reference outlining our near-peer adversaries’ (China and Russia) space strategy, doctrine, and intent; key space and counterspace organizations; and space and counterspace capabilities. These latter capabilities are further broken out into: space launch capabilities; human spaceflight and space exploration; Intelligence, Surveillance, and Reconnaissance (ISR); navigation and communications; and counterspace.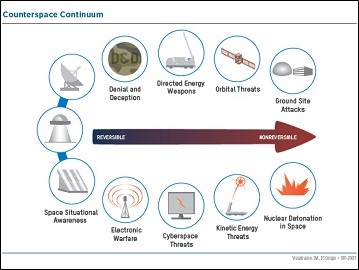 A number of useful appendices are also included, addressing the implications of debris and orbital collisions; counterspace threats illustrating the associated capabilities on a continuum from reversible (e.g., Electronic Warfare and Denial and Deception) to irreversible (e.g., Ground Site Attacks and Nuclear Detonation in Space); and a useful list defining space acronyms.
A number of useful appendices are also included, addressing the implications of debris and orbital collisions; counterspace threats illustrating the associated capabilities on a continuum from reversible (e.g., Electronic Warfare and Denial and Deception) to irreversible (e.g., Ground Site Attacks and Nuclear Detonation in Space); and a useful list defining space acronyms. One of the major barriers to quantum computing is a rather unexpected one: in order for superconduction to occur, it must be very cold. Superconduction is an electrical current that moves “entirely without resistance” and, as of now, with standard materials superconduction is only possible at -200oC. In quantum computing there are massive amounts of particles moving in interdependent trajectories, and precisely calculating all of them is impossible. Researchers at TU Wien (Technische Universität Wien – Vienna University of Technology) were able to add on to an existing equation that allows for the approximate calculation of these particles in solid matter, not just a vacuum. This new formula may make it easier to develop different superconducting materials and potentially identify materials that could conduct at room temperature.
One of the major barriers to quantum computing is a rather unexpected one: in order for superconduction to occur, it must be very cold. Superconduction is an electrical current that moves “entirely without resistance” and, as of now, with standard materials superconduction is only possible at -200oC. In quantum computing there are massive amounts of particles moving in interdependent trajectories, and precisely calculating all of them is impossible. Researchers at TU Wien (Technische Universität Wien – Vienna University of Technology) were able to add on to an existing equation that allows for the approximate calculation of these particles in solid matter, not just a vacuum. This new formula may make it easier to develop different superconducting materials and potentially identify materials that could conduct at room temperature.

 Moral A.I. would require home assistants to “decide whether to report their owners for breaking the law,” or to remain silent. “This would let them weigh whether to report illegal activity to the police, effectively putting millions of people under constant surveillance.” Stakeholders “need to be identified and have a say, including when machines shouldn’t be able to listen in. Right now only the manufacturer decides.” At present, neither stakeholders nor consumers are in charge of their own information and companies use our personal information freely, without commensurate compensation.
Moral A.I. would require home assistants to “decide whether to report their owners for breaking the law,” or to remain silent. “This would let them weigh whether to report illegal activity to the police, effectively putting millions of people under constant surveillance.” Stakeholders “need to be identified and have a say, including when machines shouldn’t be able to listen in. Right now only the manufacturer decides.” At present, neither stakeholders nor consumers are in charge of their own information and companies use our personal information freely, without commensurate compensation. If developed, brought to market, and installed (presumably willingly) in our homes (or public spaces), is Moral A.I. a human problem?
If developed, brought to market, and installed (presumably willingly) in our homes (or public spaces), is Moral A.I. a human problem? Signaling System 7 (SS7) is a series of cellular telephone protocols first built in 1975 that allows for telephonic communication around the globe. Within this set of protocols is a massive security vulnerability that has been public knowledge for over a decade. The vulnerability allows a nefarious actor to, among other things, track user location, dodge encryption, and record conversations. What’s more, this can be done while looking like ordinary carrier chatter and, in some cases, can be used to gain access to bank accounts through 2-factor authentication and effectively drain them.
Signaling System 7 (SS7) is a series of cellular telephone protocols first built in 1975 that allows for telephonic communication around the globe. Within this set of protocols is a massive security vulnerability that has been public knowledge for over a decade. The vulnerability allows a nefarious actor to, among other things, track user location, dodge encryption, and record conversations. What’s more, this can be done while looking like ordinary carrier chatter and, in some cases, can be used to gain access to bank accounts through 2-factor authentication and effectively drain them. the soldiers themselves through text messages, social media, or cell phone calls. The SS7 vulnerability could make these campaigns more successful or easier to execute and allow them to penetrate farther into the personal lives of soldiers than ever before.
the soldiers themselves through text messages, social media, or cell phone calls. The SS7 vulnerability could make these campaigns more successful or easier to execute and allow them to penetrate farther into the personal lives of soldiers than ever before.

 A recent example highlighting the inherent and unpredictable vulnerabilities presented by these emerging technologies is the incident involving personal fitness devices that
A recent example highlighting the inherent and unpredictable vulnerabilities presented by these emerging technologies is the incident involving personal fitness devices that In the previous example, the culprit was a smart watch or fitness tracking device that is a companion piece to the smart phone. Removing or prohibiting these devices is less detrimental to the overall morale, spirit, and will power of our Soldiers than removing their cell phones — their primary means of voice, data, and social media connectivity — oftentimes their sole link with their family back home. Adversaries have already employed tactics designed to exploit vulnerabilities arising from Soldier cellphone use. In the Ukraine, a popular
In the previous example, the culprit was a smart watch or fitness tracking device that is a companion piece to the smart phone. Removing or prohibiting these devices is less detrimental to the overall morale, spirit, and will power of our Soldiers than removing their cell phones — their primary means of voice, data, and social media connectivity — oftentimes their sole link with their family back home. Adversaries have already employed tactics designed to exploit vulnerabilities arising from Soldier cellphone use. In the Ukraine, a popular



 On January 29th, 2019, Daniel Coats, the United States Director of National Intelligence, reported to the Senate Select Committee on Intelligence about emerging threats to national security.
On January 29th, 2019, Daniel Coats, the United States Director of National Intelligence, reported to the Senate Select Committee on Intelligence about emerging threats to national security. Russian activities and collaborative efforts
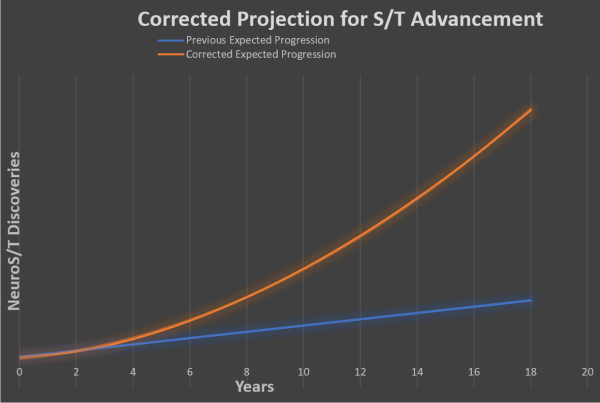
Russian activities and collaborative efforts China’s expanding efforts in bio S/T research and innovation is significant as it can, and is intended to alter the international geopolitical landscape.
China’s expanding efforts in bio S/T research and innovation is significant as it can, and is intended to alter the international geopolitical landscape.
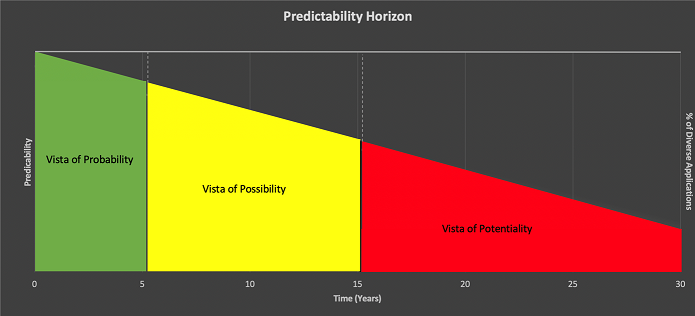

 The U.S. defense industry routinely analyzes emerging and potentially
The U.S. defense industry routinely analyzes emerging and potentially  According to Paul Scharre‘s preface to Elsa Kania‘s paper on
According to Paul Scharre‘s preface to Elsa Kania‘s paper on unintentionally follows the
unintentionally follows the


 For example, quantum computation uses the quantum analog of a bit, called a quantum bit, existing in multiple states due to
For example, quantum computation uses the quantum analog of a bit, called a quantum bit, existing in multiple states due to This post sees QAI as a different element of the taxonomy and not a subset of classical AI. “Quantum physics is based on information theory and probability theory” according to Andreas Wichert, author of
This post sees QAI as a different element of the taxonomy and not a subset of classical AI. “Quantum physics is based on information theory and probability theory” according to Andreas Wichert, author of  amount of information where N=6 because the possible alternatives are six. Instead of “N” (number of alternatives), scientists measure information in terms of quantity deemed “S” after Shannon. Rovelli also states information is finite in nature based on quantum mechanical properties. New or “relevant” information cancels out “irrelevant” information in a physical system, therefore systems can always obtain new information from other systems. *This point is important for later.
amount of information where N=6 because the possible alternatives are six. Instead of “N” (number of alternatives), scientists measure information in terms of quantity deemed “S” after Shannon. Rovelli also states information is finite in nature based on quantum mechanical properties. New or “relevant” information cancels out “irrelevant” information in a physical system, therefore systems can always obtain new information from other systems. *This point is important for later.
 This specific interpretation is based on Hugh Everett’s relative state or many-worlds interpretation (MWI) and information
This specific interpretation is based on Hugh Everett’s relative state or many-worlds interpretation (MWI) and information • Relevant information cancels out irrelevant information in a physical system, therefore systems can always obtain new information from other systems
• Relevant information cancels out irrelevant information in a physical system, therefore systems can always obtain new information from other systems One interpretation of AI is
One interpretation of AI is vice versa (alternate histories and futures). Physicist David Deutsch, a proponent of the MWI, believes MWI will be testable through
vice versa (alternate histories and futures). Physicist David Deutsch, a proponent of the MWI, believes MWI will be testable through