[Editor’s Note: During this unprecedented period of enforced isolation and telework, Mad Scientist solicited your input on how the current COVID-19 Global Pandemic could shape the Operational Environment (OE) and change the character of warfare. During the coming weeks … Read the rest
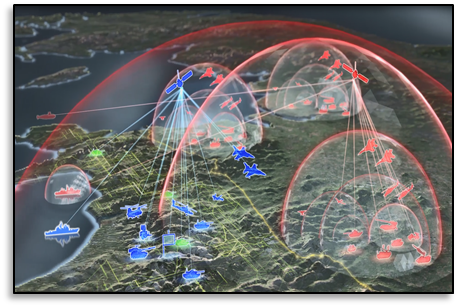
197. The Arctic: An Emergent Zone of Great Power Competition
[Editor’s Note: Mad Scientist Laboratory is pleased to present in today’s post two articles excerpted from last month’s OE Watch addressing BNU-1, China’s first observation satellite providing coverage of the Arctic and Antarctic regions, and their high latitude… Read the rest
192. New Skills Required to Compete & Win in the Future Operational Environment
[Editor’s Note: The U.S. Army Training and Doctrine Command (TRADOC) recruits, trains, educates, develops, and builds the Army, driving constant improvement and change to ensure that the Army can successfully compete and deter, fight, and decisively win on any … Read the rest
172. Splinternets
[Editor’s Note: Mad Scientist Laboratory welcomes returning guest blogger and proclaimed Mad Scientist Mr. Howard R. Simkin with his submission to our Mad Scientist Crowdsourcing topic from earlier this summer on The Operational Environment: What Will Change and What … Read the rest
131. Omega
[Editor’s Note: Story Telling is a powerful tool that allows us to envision how innovative and potentially disruptive technologies could be employed and operationalized in the Future Operational Environment. In today’s guest blog post, proclaimed Mad Scientist Mr. August … Read the rest