[Editor’s Note: The Army’s Mad Scientist Laboratory is pleased to feature the first in a series of posts excerpting findings from Team Axis Insight 2035‘s Project Deterrence Final Report. This Integrated Research Project documents the findings from the group’s United States Army War College (USAWC) Strategic Research Requirement portion of the Master of Strategic Studies degree program that occurred over the academic year (from November 2024 to April 2025).
Team Axis Insight 2035 consisted of COL Byron N. Cadiz, COL T. Marc Skinner, LTC Robert W. Mayhue, LTC Lori L. Perkins, and LTC Shun Y. Yu — all U.S. Army Officers and now proclaimed Army Mad Scientists! Team Axis Insight 2035‘s Project Deterrence Final Report documents their collective response to the following question posed by Ian Sullivan, Deputy Chief of Staff, G-2, U.S. Army Training and Doctrine Command:
How are China, Russia, Iran, and North Korea likely to respond to U.S.-led deterrence efforts by 2035?
Team Axis Insight 2035‘s Key Findings are:
 “By 2035, it is almost certain that China, Russia, Iran, and North Korea will respond to US deterrence with entanglement, disruptive technology, and persistent coercion. The global landscape is rapidly transforming, characterized by increasing complexity and challenges to U.S. influence. This seismic shift is marked by two key findings, the first encompassed in three threat vectors: 1) an entangled future of situational cooperation and transactional interdependence among China, Russia, Iran, and North Korea which amplifies deterrence challenges; 2) disruptive technology by which the U.S. advantages are severely threatened or lost to adversarial emerging technologies; and 3) persistent coercion consisting of the expansion and exploitation of gray zone activities in which aggression below the level of armed conflict bypasses traditional deterrence. Collectively, these developments forecast that U.S. deterrence is at risk of becoming strategically irrelevant without integrated, adaptive responses across all instruments of power. The second key finding is that China is not just the pacing challenge, but the true threat: all roads go through China. Russia, Iran, and North Korea will continue to pose primarily regional challenges. While China is highly unlikely (16-30%)* to exert direct control of Russia, Iran, or North Korea, its regional investments will provide China with considerable leverage to provoke or mitigate destabilizing actions to promote and protect its interests.”
“By 2035, it is almost certain that China, Russia, Iran, and North Korea will respond to US deterrence with entanglement, disruptive technology, and persistent coercion. The global landscape is rapidly transforming, characterized by increasing complexity and challenges to U.S. influence. This seismic shift is marked by two key findings, the first encompassed in three threat vectors: 1) an entangled future of situational cooperation and transactional interdependence among China, Russia, Iran, and North Korea which amplifies deterrence challenges; 2) disruptive technology by which the U.S. advantages are severely threatened or lost to adversarial emerging technologies; and 3) persistent coercion consisting of the expansion and exploitation of gray zone activities in which aggression below the level of armed conflict bypasses traditional deterrence. Collectively, these developments forecast that U.S. deterrence is at risk of becoming strategically irrelevant without integrated, adaptive responses across all instruments of power. The second key finding is that China is not just the pacing challenge, but the true threat: all roads go through China. Russia, Iran, and North Korea will continue to pose primarily regional challenges. While China is highly unlikely (16-30%)* to exert direct control of Russia, Iran, or North Korea, its regional investments will provide China with considerable leverage to provoke or mitigate destabilizing actions to promote and protect its interests.”
Today’s post excerpts Team Axis Insight 2035‘s finding regarding “an entangled future of situational cooperation and transactional inter-dependence among China, Russia, Iran, and North Korea which amplifies deterrence challenges” — Enjoy!]
Threat Vector #1: Entangled Future
 Despite shared opposition to the U.S.-led global order, China, Russia, Iran, and North Korea are highly unlikely* to formalize an alliance by 2035 due to longstanding historical animosities and conflicting geopolitical priorities. Instead, the relationships among these actors are almost certain (86-99%)* to intensify, presenting significant challenges to established global norms and the influence of the United States. Characterized as situational, opportunistic, and largely bilateral, their partnerships are highly likely* to become more complex as they become entangled through economic realignments, supply chain dependencies, and technological cooperation.
Despite shared opposition to the U.S.-led global order, China, Russia, Iran, and North Korea are highly unlikely* to formalize an alliance by 2035 due to longstanding historical animosities and conflicting geopolitical priorities. Instead, the relationships among these actors are almost certain (86-99%)* to intensify, presenting significant challenges to established global norms and the influence of the United States. Characterized as situational, opportunistic, and largely bilateral, their partnerships are highly likely* to become more complex as they become entangled through economic realignments, supply chain dependencies, and technological cooperation.
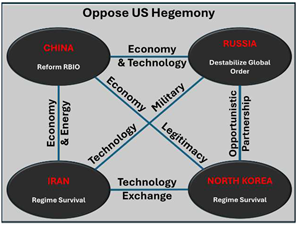
Self-generated from Analytic Reports Supporting Key Findings
As their relationships deepen, the resulting increase in strategic and tactical coordination among these nations will likely (56-70%)* create uncertainty across multiple domains, reducing the effectiveness of traditional U.S. deterrence measures. Current U.S. deterrence approaches rely on forward presence, technology export controls, economic sanctions or incentives, and military alliances and partnerships, such as NATO, AUKUS, and the Quad. Our adversaries and competitors seek to exploit the gaps and seams in U.S. deterrence activities. The synergistic effect of revisionist states’ asymmetric tactics, amplified by China’s institutional and economic leverage, threatens to normalize illiberal practices while eroding the credibility of U.S.-backed enforcement mechanisms. This convergence poses a distributed, persistent threat to U.S. influence, marked by institutional fragmentation, economic decoupling, and the strategic erosion of the foundations of the existing international order.
China
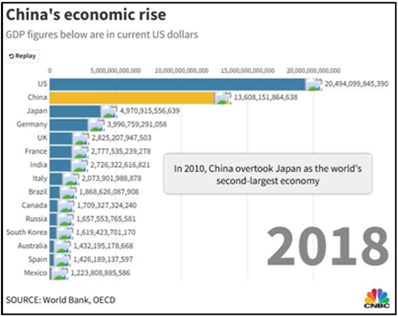
As the economic powerhouse of the quartet, China’s approach to reshaping the international order is highly likely* to favor entangled inter-dependence, leveraging economic, technological, and institutional dependencies to exert influence without direct confrontation. The Belt and Road Initiative, including the Digital Silk Road, serves as a key mechanism for expanding Chinese influence through physical and digital infrastructure, energy grids, and financial systems. China’s dominance in critical supply chains, including rare earth minerals, pharmaceuticals, and semiconductors and its growing influence in international standard-setting bodies will likely* enable it to apply subtle yet firm pressure on states dependent on its technologies and markets to achieve Chinese interests. By 2035, the entanglement of U.S. adversaries is unlikely (31-45%)* to overthrow the U.S.-led order but is highly likely* reconfigure it into a hybrid system where liberal norms coexist with Chinese-centric rules.
China’s strategy does not operate in isolation. It is increasingly intertwined with the actions of Russia, Iran, and North Korea. These relationships, driven by necessity rather than shared ideology, are almost certain to intensify as a direct response to U.S.-led deterrence and containment efforts. By 2035, these will almost certainly evolve into more integrated multi-domain operations with enhanced artificial intelligence, space, and cyber capabilities with a sharp focus on technological denial regimes. For its benefit, China supports Russia in exchange for long-term guaranteed access to oil and gas resources to support its industrial base while undergoing conversions to clean energy. Similarly, China uses Iran for access to oil and gas at preferential  prices while diversifying energy suppliers to reduce vulnerability. North Korea benefits China by acting as a geographic buffer between China and U.S.-allied South Korea, preventing U.S. military presence along the Chinese border.
prices while diversifying energy suppliers to reduce vulnerability. North Korea benefits China by acting as a geographic buffer between China and U.S.-allied South Korea, preventing U.S. military presence along the Chinese border.
Russia
Russia, heavily sanctioned and seeking to undermine U.S. influence, is likely* to continue its assertive behavior in Europe, though war with North Atlantic Treaty Organization (NATO) countries will remain unlikely.* Russia’s reliance on China for economic support and its exchange of military materiel with North Korea underscore a growing alignment against the West. Russia’s development of advanced military technologies aims to erode U.S. military superiority, while its financial decoupling from the dollar, through the expansion of the System for Transfer of Financial Messages and integration with China’s Cross-Border Interbank Payment Systems, will likely* diminish the effectiveness of U.S.-led economic sanctions. China serves as Russia’s economic lifeline, providing industrial goods, 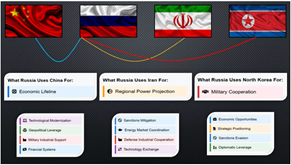 consumer products, and dual-use technology while under Western sanctions. Russia uses Iran for regional power projection into the Middle East to counter US influence, facilitating military cooperation in exchange for potential basing options.
consumer products, and dual-use technology while under Western sanctions. Russia uses Iran for regional power projection into the Middle East to counter US influence, facilitating military cooperation in exchange for potential basing options.
Iran

Iran, motivated by regime survival, is highly likely* to continue its aggressive development of drone warfare capabilities and conduct cyberattacks against critical U.S. infrastructure. Its willingness to export drone technology highlights its pursuit of indirect conflict as a means of projecting power. Iran’s increasing reliance on China for oil exports amid sanctions is highly likely* to grant Beijing significant leverage over Tehran’s foreign policy decisions. In exchange for regional access, Iran benefits from Russia’s military technology including advanced air defense systems, combat aircraft, and naval vessels, as well as technical assistance for civilian nuclear facilities as a diplomatic cover for possible nuclear weapons development.  Though geographically separated, Iran will foster deepened relations with North Korea to benefit from their ballistic missile technology and expertise, particularly as it applies to their nuclear program and possible technology transfers.
Though geographically separated, Iran will foster deepened relations with North Korea to benefit from their ballistic missile technology and expertise, particularly as it applies to their nuclear program and possible technology transfers.
North Korea

North Korea, despite its limited capabilities, is highly likely* to provocatively leverage its military capacity to ensure regime survival. To prevent uncontrolled escalation and destabilization in the region, China will almost certainly continue to serve as a critical trade partner to North Korea, ensuring its economic solvency. Russia will likely* repay North Korea’s troop and munitions support through transfers of sophisticated weapons technologies for its nuclear, missile, and submarine programs, to include training and technical assistance for further weapons development. The deepening Russia-North Korea relationship will likely* weaken the United Nations’ Security Council’s enforcement mechanisms, further undermining global nonproliferation norms. In exchange for its assistance with Iran’s missile and nuclear program, North Korea is highly likely* to seek support in drone technology and production techniques. 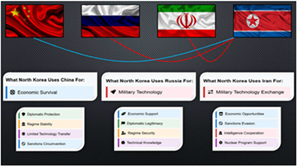 The converging strategies of these actors will generate a synergistic effect across multiple domains, challenging the U.S.-led international order through disruptive technologies and persistent coercion.
The converging strategies of these actors will generate a synergistic effect across multiple domains, challenging the U.S.-led international order through disruptive technologies and persistent coercion.
If you enjoyed this post, check out Axis Insight 2035‘s comprehensive Project Deterrence Final Report here.
Review the TRADOC Pamphlet 525-92, The Operational Environment 2024-2034: Large-Scale Combat Operations
Explore the TRADOC G-2‘s Operational Environment Enterprise web page, brimming with authoritative information on the Operational Environment and how our adversaries fight, including:
Our China Landing Zone, full of information regarding our pacing challenge, including ATP 7-100.3, Chinese Tactics, How China Fights in Large-Scale Combat Operations, BiteSize China weekly topics, and the People’s Liberation Army Ground Forces Quick Reference Guide.
Our Russia Landing Zone, including the BiteSize Russia weekly topics. If you have a CAC, you’ll be especially interested in reviewing our weekly RUS-UKR Conflict Running Estimates and associated Narratives, capturing what we learned about the contemporary Russian way of war in Ukraine over the past two years and the ramifications for U.S. Army modernization across DOTMLPF-P.
Our Iran Landing Zone, including the Iran Quick Reference Guide and the Iran Passive Defense Manual (both require a CAC to access).
Our North Korea Landing Zone, including Resources for Studying North Korea, Instruments of Chinese Military Influence in North Korea, and Instruments of Russian Military Influence in North Korea.
Our Running Estimates SharePoint site (also requires a CAC to access) — documenting what we’re learning about the evolving OE. Contains our monthly OE Running Estimates, associated Narratives, and the quarterly OE Assessment TRADOC Intelligence Posts (TIPs).
Then review the following related Mad Scientist Laboratory content from several previous TRADOC G-2 sponsored USAWC projects:
Team Sullivan’s Travels‘ Future Dynamics of Warfare: Everyone is a Player, Everything is a Target and their associated Final Report.
Team Techno-Warfare Group‘s What Skill Sets Will Leaders Need for Warfare in 2035? and their Techno Sentient Warfare in 2035 Final Report.
>>>>REMINDER — Only Two Days Left!!! Learn how you can submit your entry(ies) to our Great Power Competition & Conflict writing contest by clicking here to review the contest rules. We look forward to your participation and reading your thoughtful submissions! (S: Midnight, May 30, 2025).
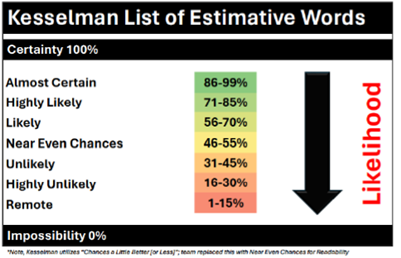
* Kesselman List of Estimative Words:
Disclaimer: The views expressed in this blog post do not necessarily reflect those of the U.S. Department of Defense, Department of the Army, Army Futures Command (AFC), or Training and Doctrine Command (TRADOC).



 Charlotte Feit-Leichman’s urgent and incisive analysis —
Charlotte Feit-Leichman’s urgent and incisive analysis —  innovation has
innovation has  China’s success in this space underscores the necessity of rapid, integrated technological adaptation if the U.S. is to maintain any equivalence of tactical military capability, and any realistic consideration of strategic parity.
China’s success in this space underscores the necessity of rapid, integrated technological adaptation if the U.S. is to maintain any equivalence of tactical military capability, and any realistic consideration of strategic parity. must be done with unwavering commitment to ethical responsibility, human oversight, and strategic foresight. Feit-Leichman rightly warns of the dangers posed by automated decision-making processes in nuclear command, amplifying the risk of error. We agree and add that given the current trends in automation she describes, a prime responsibility is to ensure that these systems complement, rather than replace, human judgment.
must be done with unwavering commitment to ethical responsibility, human oversight, and strategic foresight. Feit-Leichman rightly warns of the dangers posed by automated decision-making processes in nuclear command, amplifying the risk of error. We agree and add that given the current trends in automation she describes, a prime responsibility is to ensure that these systems complement, rather than replace, human judgment. AI and autonomous systems reshape the battlefield, the military should revise training models to emphasize human-machine collaboration in decision-making under conditions of variable uncertainty.
AI and autonomous systems reshape the battlefield, the military should revise training models to emphasize human-machine collaboration in decision-making under conditions of variable uncertainty. modernization; rather, it is a strategic mandate for overmatch, deterrence, and survival in the face of accelerating threat trajectories. Toward these ends the U.S. military must anticipate, adapt, and accelerate technological achievement to outpace peer and near-peer adversaries across Land, Air, Sea, Space, Cyber, and Cognitive Domains. [N.B., while the U.S. recognizes and plans for warfighting in the first five of these domains, it is important to note: 1) we don’t recognize cognitive as a separate warfighting domain, while 2) China recognizes both the Cognitive and Electromagnetic Spectrum Domains, in addition to the first five listed here.]
modernization; rather, it is a strategic mandate for overmatch, deterrence, and survival in the face of accelerating threat trajectories. Toward these ends the U.S. military must anticipate, adapt, and accelerate technological achievement to outpace peer and near-peer adversaries across Land, Air, Sea, Space, Cyber, and Cognitive Domains. [N.B., while the U.S. recognizes and plans for warfighting in the first five of these domains, it is important to note: 1) we don’t recognize cognitive as a separate warfighting domain, while 2) China recognizes both the Cognitive and Electromagnetic Spectrum Domains, in addition to the first five listed here.] 1. Innovation cannot be confined to peripheral initiatives, wargaming labs, or specialized units. It must be institutionalized and integrated within every aspect of force design, command architecture, acquisition pipelines, and professional military education.
1. Innovation cannot be confined to peripheral initiatives, wargaming labs, or specialized units. It must be institutionalized and integrated within every aspect of force design, command architecture, acquisition pipelines, and professional military education. institutions. The future of warfighting demands a paradigm shift, supported by systems-level vulnerability audits and anticipatory assessments. These processes must identify where adversaries may target and exploit seams in U.S. (technical, doctrinal and operational) capability and engage efforts to close these gaps through disruptive strategies.
institutions. The future of warfighting demands a paradigm shift, supported by systems-level vulnerability audits and anticipatory assessments. These processes must identify where adversaries may target and exploit seams in U.S. (technical, doctrinal and operational) capability and engage efforts to close these gaps through disruptive strategies.



 A year earlier, he and his intelligence team formed several seemingly legitimate American businesses whose task was to find publicly available information about upcoming requirements for bolts so they could underbid American companies and potentially gain access to critical technologies. These small business startups are now PLA insider threats targeting and exploiting the Department of Defense’s publicly available contract information and bidding on contracts, delivering the bolts on time and under budget. The bolts pass initial quality control tests, but are subtly flawed, using inferior materials that degrade over time. The PLA’s small businesses are virtual companies masquerading as American companies, incorporated in American cities and recruiting unknowing Americans to gather data necessary to supply the defective bolts to the U.S. Army. These virtual companies post online job opportunities with good pay and remote work, which is advantageous to the operation and enticing to potential recruits.
A year earlier, he and his intelligence team formed several seemingly legitimate American businesses whose task was to find publicly available information about upcoming requirements for bolts so they could underbid American companies and potentially gain access to critical technologies. These small business startups are now PLA insider threats targeting and exploiting the Department of Defense’s publicly available contract information and bidding on contracts, delivering the bolts on time and under budget. The bolts pass initial quality control tests, but are subtly flawed, using inferior materials that degrade over time. The PLA’s small businesses are virtual companies masquerading as American companies, incorporated in American cities and recruiting unknowing Americans to gather data necessary to supply the defective bolts to the U.S. Army. These virtual companies post online job opportunities with good pay and remote work, which is advantageous to the operation and enticing to potential recruits.
 bolts are already in DoD’s inventory and supply system, threatening readiness and posing a grave danger to U.S. forces –– the small business has been paid by the Defense Finance Accounting Service (DFAS), closed up shop, and disappeared. Jane’s searches were subtle enough to avoid notice –– the Army never suspected an insider threat had penetrated its supply chain.
bolts are already in DoD’s inventory and supply system, threatening readiness and posing a grave danger to U.S. forces –– the small business has been paid by the Defense Finance Accounting Service (DFAS), closed up shop, and disappeared. Jane’s searches were subtle enough to avoid notice –– the Army never suspected an insider threat had penetrated its supply chain. This readily available information, while intended to promote transparency and competition, could also be exploited. It’s plausible that foreign intelligence agencies have infiltrated numerous small businesses by embedding seemingly innocuous, low-level contractor employees. Their mission could be to gather and analyze publicly available procurement data, focusing on Army purchasing activities worldwide. By scrutinizing details such as who is buying what, from whom, when, where, and in what quantities, these operatives could identify patterns and deduce the underlying reasons for specific procurement activities. This underscores the inherent tension between transparency in government contracting and the need to protect information that, while public, could be leveraged by adversaries.
This readily available information, while intended to promote transparency and competition, could also be exploited. It’s plausible that foreign intelligence agencies have infiltrated numerous small businesses by embedding seemingly innocuous, low-level contractor employees. Their mission could be to gather and analyze publicly available procurement data, focusing on Army purchasing activities worldwide. By scrutinizing details such as who is buying what, from whom, when, where, and in what quantities, these operatives could identify patterns and deduce the underlying reasons for specific procurement activities. This underscores the inherent tension between transparency in government contracting and the need to protect information that, while public, could be leveraged by adversaries. The future of warfare depends on secure and resilient supply chains. By addressing these vulnerabilities head-on, the U.S. military can safeguard our Soldier’s readiness and protect our national security.
The future of warfare depends on secure and resilient supply chains. By addressing these vulnerabilities head-on, the U.S. military can safeguard our Soldier’s readiness and protect our national security.
 The publication describes China’s military philosophy, details the structure of the PLA and its Joint Theater Commands, and examines the PLA’s approach to operations across all domains, its critical capabilities, and specifically addresses the role of ground forces in Large-Scale Combat Operations. It concludes with two ground force-focused vignettes: an island seizure operation and an island defense. This paper offers the U.S. Army and Joint force an effective starting point for visualizing the potential fight in the Indo-Pacific.
The publication describes China’s military philosophy, details the structure of the PLA and its Joint Theater Commands, and examines the PLA’s approach to operations across all domains, its critical capabilities, and specifically addresses the role of ground forces in Large-Scale Combat Operations. It concludes with two ground force-focused vignettes: an island seizure operation and an island defense. This paper offers the U.S. Army and Joint force an effective starting point for visualizing the potential fight in the Indo-Pacific. As the Deputy Chief of Staff, G-2 for the U.S. Army’s Training and Doctrine Command (TRADOC), I am pleased to introduce this timely paper, How China Fights in Large-Scale Combat Operations. This will be the first of a series of papers focusing on our key potential adversaries—China, Russia, Iran, and North Korea—and we chose to start with the most capable and formidable of the four. In an article I wrote for
As the Deputy Chief of Staff, G-2 for the U.S. Army’s Training and Doctrine Command (TRADOC), I am pleased to introduce this timely paper, How China Fights in Large-Scale Combat Operations. This will be the first of a series of papers focusing on our key potential adversaries—China, Russia, Iran, and North Korea—and we chose to start with the most capable and formidable of the four. In an article I wrote for This document builds upon two seminal TRADOC G-2 publications. The first is
This document builds upon two seminal TRADOC G-2 publications. The first is  characteristics of future PLA operations. This new paper sheds light on how the Chinese Communist Party views its security environment and how this perception shapes the PLA’s approach to warfighting, particularly its emphasis on “active defense” and “systems confrontation.” The insights presented here are not merely academic; they are essential for informing our training methodologies and force development initiatives.
characteristics of future PLA operations. This new paper sheds light on how the Chinese Communist Party views its security environment and how this perception shapes the PLA’s approach to warfighting, particularly its emphasis on “active defense” and “systems confrontation.” The insights presented here are not merely academic; they are essential for informing our training methodologies and force development initiatives. This paper will be disseminated across the Army, the Joint Force, the Intelligence Community, and to our allies and partners to promote a deeper understanding of Chinese military thought and operational practices. It will drive curriculum development at our schools and centers, inform professional military education, support the writing of Army doctrine, and enhance the realism and relevance of U.S. Army training scenarios at Combat Training Centers. By incorporating the PLA’s operational doctrine, tactics, and technological capabilities
This paper will be disseminated across the Army, the Joint Force, the Intelligence Community, and to our allies and partners to promote a deeper understanding of Chinese military thought and operational practices. It will drive curriculum development at our schools and centers, inform professional military education, support the writing of Army doctrine, and enhance the realism and relevance of U.S. Army training scenarios at Combat Training Centers. By incorporating the PLA’s operational doctrine, tactics, and technological capabilities into our opposing force representation, we can also better prepare our Soldiers and leaders for the challenges they would face in a potential conflict in the Indo-Pacific theater. It will help us fulfill our primary mission, which is to know our potential adversaries, and to ensure that our key customers do too.
into our opposing force representation, we can also better prepare our Soldiers and leaders for the challenges they would face in a potential conflict in the Indo-Pacific theater. It will help us fulfill our primary mission, which is to know our potential adversaries, and to ensure that our key customers do too. How China Fights in Large-Scale Combat Operations provides a detailed assessment of China’s military strategy, operational concepts, and the anticipated characteristics of the PLA ground forces employed in conflict. As China is designated as the United States’ pacing threat, the U.S. Army must understand how China fights at the operational level to ensure readiness for potential conflicts in the Indo-Pacific theater. This document builds upon foundational material presented in
How China Fights in Large-Scale Combat Operations provides a detailed assessment of China’s military strategy, operational concepts, and the anticipated characteristics of the PLA ground forces employed in conflict. As China is designated as the United States’ pacing threat, the U.S. Army must understand how China fights at the operational level to ensure readiness for potential conflicts in the Indo-Pacific theater. This document builds upon foundational material presented in 
 Anticipating foreign intervention in the Pacific theater, China has developed a comprehensive joint counter-intervention complex aimed at deterring, delaying, and defeating enemy forces before they can arrive in theater at full strength. This campaign involves information operations to disrupt enemy decision-making processes, air and sea dominance efforts to control critical theaters, and joint firepower strikes targeting deployment routes and logistics hubs. PLA ground forces will play an integral role in these campaigns through amphibious assaults, airborne maneuvers, strategic defenses, and counterattacks—all fully integrated into joint operations.
Anticipating foreign intervention in the Pacific theater, China has developed a comprehensive joint counter-intervention complex aimed at deterring, delaying, and defeating enemy forces before they can arrive in theater at full strength. This campaign involves information operations to disrupt enemy decision-making processes, air and sea dominance efforts to control critical theaters, and joint firepower strikes targeting deployment routes and logistics hubs. PLA ground forces will play an integral role in these campaigns through amphibious assaults, airborne maneuvers, strategic defenses, and counterattacks—all fully integrated into joint operations. Ground forces, which are often underestimated in discussions about Pacific conflicts dominated by air and naval operations, play a critical role in countering China’s strategies. The PLA’s reliance on ground forces for amphibious assaults, airborne operations, and strategic counterattacks demonstrates their integral role in achieving operational objectives. Similarly, U.S. ground forces are essential for securing key terrain, enabling joint operations, and disrupting adversary systems in contested environments. As the Indo-Pacific theater presents unique challenges due to its geography and the multidomain nature of modern warfare, the U.S. Army must ensure its ground forces are prepared to operate effectively alongside other components of the Joint Force. This preparation is vital not only for deterring aggression but also for ensuring victory in any potential conflict with China.
Ground forces, which are often underestimated in discussions about Pacific conflicts dominated by air and naval operations, play a critical role in countering China’s strategies. The PLA’s reliance on ground forces for amphibious assaults, airborne operations, and strategic counterattacks demonstrates their integral role in achieving operational objectives. Similarly, U.S. ground forces are essential for securing key terrain, enabling joint operations, and disrupting adversary systems in contested environments. As the Indo-Pacific theater presents unique challenges due to its geography and the multidomain nature of modern warfare, the U.S. Army must ensure its ground forces are prepared to operate effectively alongside other components of the Joint Force. This preparation is vital not only for deterring aggression but also for ensuring victory in any potential conflict with China.
 Russia’s convergence of artificial intelligence (AI) and autonomous systems could signal an increase in the risk of tactical nuclear weapons being used on the battlefield. AI weapons systems use computer algorithms to attack a target without the manual control of a human operator.
Russia’s convergence of artificial intelligence (AI) and autonomous systems could signal an increase in the risk of tactical nuclear weapons being used on the battlefield. AI weapons systems use computer algorithms to attack a target without the manual control of a human operator. the future.
the future.


 The decision-making process involved in launching a nuclear attack can be explained through the OODA loop model, consisting of observe, orient, decide, and act.
The decision-making process involved in launching a nuclear attack can be explained through the OODA loop model, consisting of observe, orient, decide, and act. Automation bias is when humans become conditioned to the repeated success of algorithms causing cognitive offloading and complete trust in the machine — even when a non-biased human might recognize that the machine is reporting incorrect information.
Automation bias is when humans become conditioned to the repeated success of algorithms causing cognitive offloading and complete trust in the machine — even when a non-biased human might recognize that the machine is reporting incorrect information. and arm Soldiers with the requisite gear for operating in a nuclear contaminated environment.
and arm Soldiers with the requisite gear for operating in a nuclear contaminated environment.