[Editor’s Note: Storytelling is one of Army Mad Scientist’s most effective tools in exploring the broad range of possibilities within the Operational Environment. Employing creative fictional writing and narrative building helps us to explore how concepts, technologies, and other capabilities could be employed and operationalized.
Army Mad Scientist welcomes returning blogger Dr. Rob Smith with today’s fictional intelligence (FICINT) submission, exploring how our pacing challenge — China — could achieve the reunification of Taiwan. Through the masterful and innovative harnessing of disparate, liminal disruptions — including generating a fake “natural” disaster with our Russian and North Korean adversaries and exploiting the ensuing humanitarian crisis; launching disruptive cyber-attacks; executing influence operations via mis- and disinformation, deceptive narratives, and flash mobs; and exploiting the twin distractions of an Iranian-generated international crisis in the Persian Gulf and a kinetic strike masked as an accident near INDO-PACOM Headquarters in Hawaii — China is able to achieve President Xi Jinping’s objective of reunification.
The on-going war in Ukraine has already seen North Korea, China, and Iran provide materiel support to Russia. HAMAS, Hezbollah, and the Houthis have launched strikes against Israel, while the Houthis recently launched strikes against U.S. targets in the Middle East and commercial shipping in the Red Sea. Collaboration between our adversaries to achieve their objectives is becoming a reality. As Dr. Russell Glenn so eloquently described in a previous post, our adversaries will strive to achieve their nefarious objectives through “sub-threshold maneuver” — Read on to explore Dr. Rob Smith‘s audacious example of one such possibility!]
Act 1: Faking a Natural Disaster to Create a Data Blockade
China’s persistent “United Front” campaign attempts to influence Taiwan’s stance on reunification. Notable figures, ranging from grassroots leaders to celebrities, have been targeted to advocate for reunification. Moreover, allegations of Chinese interference in Taiwan’s media landscape further complicate the democratic island’s efforts to defend its core values and shield its citizenry from external influences. Despite employing a well-calibrated blend of soft power tactics directed at Taiwan, China has fallen short of securing an unequivocal pro-China consensus. There is a need to execute “plan B.”
Cut to 2025 — China executes yet another simulated blockade of Taiwan during a military exercise. North Korea has begun participating in drills with Russia and China, typically in a limited capacity. The skies and seas surrounding Taiwan brim with tension. Russian Tu-95 bombers and Chinese H-6K bombers conduct joint patrols over the Sea of Japan and the East China Sea. Chinese ships repeatedly cross into Taiwanese territory along the median. The DoD Replicator program recognized the need to stop incursions and has given Taiwan advanced drones to monitor and shadow intrusions into its airspace and maritime territories. Replicator empowers Taiwan’s Air Force and Navy with autonomous drones, enhancing their vigilance.
Seemingly unrelated, Iran suddenly blockades the Strait of Hormuz, disrupting oil supply routes and sending global economies into turmoil. With the U.S. quite distracted by Iran, North Korea deploys a Haeil-2 drone, armed with Russia’s Poseidon nuclear torpedo technology, to simulate an earthquake and invoke a subsequent tsunami. The massive tsunami is aimed precisely at Taiwan to avoid damaging the semiconductor companies while causing maximum government dysfunction as enabled by China’s massive computational hydrodynamics capabilities. The world perceives the tsunami as a tragic outcome of an earthquake, despite U.S. scientists and the intelligence community stating with high confidence that the tsunami is manmade. The Chinese disinformation machine unleashes meticulous and confusing stories and narratives that flood news outlets and chatrooms. Chinese propagandists pump out the “U.S. weather control goes awry in the Taiwan Strait trying to keep water-hungry semiconductor production up.”

The tsunami is devastating and serves as the perfect smokescreen. The optimization of Taiwan’s natural resources for semiconductor production at the expense of domestic agriculture and precarious water supplies, relying on imports, exacerbates the crisis. Taiwan finds itself isolated and vulnerable. Despite international pressure, Elon Musk refuses to activate Starlink, citing extensive business interests in China, not to mention being worried about staying neutral to assure the future flow of GPUs for his businesses.
Seizing this “opportunity,” China swiftly offers humanitarian aid to Taiwan. The tsunami “event” cuts most of the submarine fibers, and Chinese fishing vessels serendipitously damage the remaining fibers with their anchors. Claiming worries about Western influence and opportunism, China implements a blockade for air and maritime traffic in and out of Taiwan. China also jams all military and commercial Satellite uplink/downlinks in the South China Sea to implement a full data blockade. Taiwan’s government has no way of talking to the outside world, and due to the tsunami, struggles to message its own populace inside the country.
Meanwhile, in Hawaii, a container ship in port explodes. Local news reports this as an accident with an illegal fireworks container, causing power outages across part of the island, including at INDOPACOM headquarters. This seems plausible because in 2022, nearly 13,500 pounds of illegal fireworks were discovered in Honolulu harbor. Fireworks smuggling in Hawaii is just an example of how poor container inspection is even in the U.S. The crisis in Taiwan, Iran, ongoing conflict in Russia, and now a domestic issue in Hawaii combine to leave U.S. responses distracted.
Act 2: The Flash Mob
China has long ago realized that an amphibious invasion is the worst way to reunify Taiwan. They have messaged this for years just to get the United States and its allies to spend heavily on a kinetic fight so that there are limited resources to counter gray zone and information operations. Meanwhile, China has promoted tourism, business, exchanges, and positive messaging to Taiwan. The message heard is “two shores and one dear family” along with “blood is thicker than water.”

The Chinese “Flash Mob” operation builds upon the little green men idea from Ukraine. The concept of a “flash mob” was originally popularized for spontaneous dance troupes to materialize in public spaces and then disperse. Similarly, China simply activates individuals who are already in Taiwan to come together seemingly in a spontaneous way to sow discord in Taiwan, take government offices by force, seize the semiconductor companies, and then disperse. China’s advanced mass surveillance AI technology helps them draw from the 339,000 Chinese spouses residing in Taiwan. After COVID travel restrictions, Taiwan expects approximately 20,000 Chinese tourists at any given time. There are also many frantic Taiwan persons in China with families back home who can easily be coerced during the crisis. It is exceptionally challenging for observers to see the Flash Mob as it happens amidst the seemingly spontaneous mob cells performing random actions. China’s AI allows them to micro-target individuals and groups within Taiwan who have been “influenceable,” ensuring tailored messages reach receptive ears. This manipulation of society on an unprecedented scale is perfected by the Chinese learning from Cambridge Analytica’s influence during the 2016 U.S.
elections.
Providing weapons to the mob and Chinese Special Forces on the ground is easy. China provides a massive arsenal, smuggled into Taiwan in unassuming shipping containers that are already sitting in stockpiles across Taiwan. The cache of weapons is meant to arm the flash mob and escalate the unrest. Weibo makes it easy to provide information on how to create makeshift
barricades which spring up across the streets, and Molotov cocktails become a weapon of choice.
As the chaos intensifies, China’s hackers launch cyberattacks on Taiwan’s communication infrastructure, turning the online realm into a rout of narratives. The world struggles to decipher fact from fiction. Social media platforms are inundated with misleading information and manipulated images, making it nearly impossible to discern the true intentions of the protests.
Thousands take to the streets in Taiwan, their demands amplified through social media channels. Yet, beneath the facade of unity, chaos brews, as China’s covert agents infiltrate the protests, sowing discord and manipulating events to create confusion. China leaves nothing to chance. If the flash mob falters or the ruse fails, China has hidden YJ-18C containerized missiles all over Taiwan that could eliminate any resistance. As a final measure, China even smuggles an Electromagnetic Pulse (EMP) device onto Taiwan that could detonate with the sole intent of destroying all electronics. Taiwan’s defense forces are unaware of the danger until it is too late, and any outside landing force is sufficiently confused.
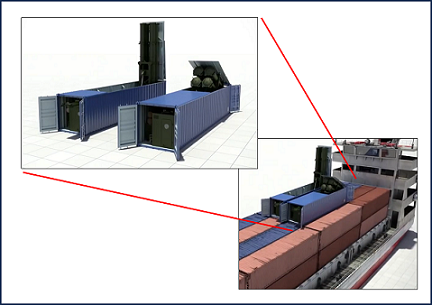
Intelligence reports emerge of 6,000 Chinese Special Forces members already within Taiwan’s borders, prepared to support the flash mob. As Taiwan’s legitimate defenders grapple with the aftermath of the tsunami, they face the challenge of identifying and neutralizing these Special Forces and the members of the massive Flash Mob without causing harm to innocent Taiwanese. The Chinese Special Forces, in combination with the mob, easily infiltrate and secure TSMC, MediaTek, ASE Technology Holdings, United Microelectronics Corp. (UMC), Novatek Microelectronics (a subsidiary of UMC), and Realtek Semiconductor. Large numbers of the employees have already either been Chinese infiltrators or have been coerced to swing their
alliance to the PRC via physical, psychological, or other means. China has no problem operating the equipment and attempting to reverse engineer machines.
Act 3: A Faux Election
As the world’s attention remains divided between the faux natural disaster and the flash mob in Taiwan, the intricate web of deception continues to unravel. In the midst of chaos and a humanitarian crisis, China’s formidable propaganda machine springs into action, painting a vivid picture of Taiwan’s internal strife and the ineptitude of its government in handling the tsunami. Leveraging advanced generative AI advertising platforms, they create tailored messages, creating bespoke propaganda using China’s massive but older GPU cloud. The AI can cheaply test messages on people until results are achieve. The deep fake celebrities and AI-generated advertising appeal to each citizen’s personal biases and inclinations. They also use AI conversations in chatrooms; China’s operatives, embedded within Taiwan’s political landscape, quietly work to influence key figures and parties. They manipulate local politicians, leveraging both carrots and sticks to ensure compliance with their agenda. Some politicians, enticed by the promise of power and wealth, are willing collaborators, while others are coerced through threats
to their families or exposure of compromising information.
Drawing inspiration from Vladimir Putin’s playbook, China engineers an “election” with a predetermined outcome: reunification. With no credible international watchdog to verify the election’s legitimacy due to communication jams, world powers find themselves in a diplomatic quagmire. The election itself is a meticulously orchestrated affair. China’s chosen candidates, disguised as staunch supporters of reunification, enter the race. With the support of their covert backers, they embark on campaigns that appear passionate and genuine to the casual observer. Campaign rallies draw large crowds, their enthusiasm carefully manufactured. Meanwhile, Taiwan’s legitimate political leaders find themselves in a precarious position. Opponents have been silenced or discredited by China’s covert apparatus, leaving a void in leadership. Those who dare to resist face threats to their safety or the safety of their loved ones, forcing them into reluctant compliance or silence. On election day, the world watches China-filtered content as Taiwan goes to the polls. China’s operatives, embedded within the electoral process, ensure that the chosen candidates secure victory. The faux election appears legitimate on the surface, with voters casting their ballots and candidates delivering impassioned speeches.
Epilogue
Following the invasion of Taiwan, China successfully acquires Taiwan’s semiconductor technology, leading to a dramatic shift in the global balance of power in tech industries overnight. China immediately stockpiles GPUs and releases only a limited quantity to the rest of the world to prevent an economic collapse. It heavily rewards those such as Starlink who have refused to help Taiwan. Since China now has the largest servers in the world, it is in a position to best capitalize on the benefits.
Cheap working-age labor fueled the economic engine that has driven China’s rise in the past, but due to the one-child policy drying up the cheap labor, the question has been “Will China Grow Old Before It Gets Rich?” Now as a massive hyperscaler, China focuses on AI-driven elder care through a growing army of care-bots. Shanghai thrives as a hub of both chatter and care-bots, marking a new age of AI-human cooperation. Factories and engineering work become dominated by AI-powered capabilities and robots to keep China’s manufacturing base humming. Advances in quantum computing follow suit, transforming China into a technological powerhouse.
China’s newfound advantage is not easy to maintain. While China is able to reverse engineer some of the semiconductor production equipment, the Dutch company ASML remains the only firm in the world capable of making the highly-complex machines that are needed to manufacture the most advanced chips. ASML and companies allied to the United States refuse to collaborate with China. This allows India, quietly building its capabilities and massive highly educated workforce, to attract foreign investments and global partnerships, positioning itself as a formidable player in semiconductor manufacturing. Urban centers like Bangalore and Hyderabad emerge as hubs of innovation. Indo-Western partnerships, with giants like Micron Technology, bolster India’s rise.
 The U.S.-Indian alliance, counterbalancing China and autocratic alliances with North Korea, Russia, and Iran, shifts Pacific security dynamics. As alliances form and technology races ahead, a multipolar world emerges, challenging the positions of established powers and reshaping global relations. However, the Pacific security landscape remains complex, with smaller nations like Vietnam, Cambodia, and the Philippines gravitating towards China, partly due to lingering doubts about American reliability, particularly after the non-intervention in Hong Kong. As alliances and rivalries play out in the data cable wars, the future sees technology shaping international relations and values, giving rise to a complex equilibrium.
The U.S.-Indian alliance, counterbalancing China and autocratic alliances with North Korea, Russia, and Iran, shifts Pacific security dynamics. As alliances form and technology races ahead, a multipolar world emerges, challenging the positions of established powers and reshaping global relations. However, the Pacific security landscape remains complex, with smaller nations like Vietnam, Cambodia, and the Philippines gravitating towards China, partly due to lingering doubts about American reliability, particularly after the non-intervention in Hong Kong. As alliances and rivalries play out in the data cable wars, the future sees technology shaping international relations and values, giving rise to a complex equilibrium.
If you enjoyed this post, stay tuned to the Mad Scientist Laboratory for Flash-Mob Warfare: Whispers in the Digital Sandstorm (Part 2)…
… in the meantime, check out the following related content:
The TRADOC G-2‘s Operational Environment Enterprise public facing page, with a plethora of content about our pacing challenge at the China Landing Zone, including ATP 7-100.3, Chinese Tactics, BiteSize China weekly topics, People’s Liberation Army Ground Forces Quick Reference Guide, and our thirty-plus snapshots captured to date addressing what China is learning about the Operational Environment from Russia’s war against Ukraine (note that a DoD Common Access Card [CAC] is required to access this last link).
The Most Consequential Adversaries and associated podcast, with GEN Charles A. Flynn
Volatility in the Pacific: China, Resilience, and the Human Dimension and associated podcast, with General Robert Brown (USA-Ret.)
How China Fights and associated podcast
China and Russia: Achieving Decision Dominance and Information Advantage, and “No Option is Excluded” — Using Wargaming to Envision a Chinese Assault on Taiwan by Ian Sullivan
China: Building Regional Hegemony and China 2049: The Flight of a Particle Board Dragon, the comprehensive report from which this post was excerpted
Competition and Conflict in the Next Decade
Disrupting the “Chinese Dream” – Eight Insights on how to win the Competition with China
The U.S. Joint Force’s Defeat before Conflict, by CPT Anjanay Kumar
Sub-threshold Maneuver and the Flanking of U.S. National Security, by Dr. Russell Glenn
Global Entanglement and Multi-Reality Warfare and associated podcast, with COL Stefan Banach (USA-Ret.)
Hybrid Threats and Liminal Warfare and associated podcast, with Dr. David Kilcullen
Weaponized Information: What We’ve Learned So Far…, Insights from the Mad Scientist Weaponized Information Series of Virtual Events, and all of this series’ associated content and videos [access via a non-DoD network]
Insights from Ukraine on the Operational Environment and the Changing Character of Warfare
About the Author: Dr. Robert E. Smith is the Army Futures Command International Science Advisor to U.S. Army Pacific Command. Previously he worked in the Ground Vehicles Systems Center doing research centered early synthetic prototyping and extracting tactics from gaming data. His career includes experience at Ford Motor Co., Whirlpool Corp., and General Dynamics Land Systems. He holds a Ph.D. in Mechanical Engineering from Michigan Technological University with a focus on AI and Machine Learning.
Disclaimer: The views expressed in this blog post do not necessarily reflect those of the U.S. Department of Defense, Department of the Army, Army Futures Command (AFC), or Training and Doctrine Command (TRADOC).



