[Editor’s Note: The Army’s Mad Scientist Laboratory is pleased to feature the first in a series of posts from the United States Army War College (USAWC) Team Sullivan’s Travels‘ Future Dynamics of Warfare: Everyone is a Player, Everything is a Target Final Report. This report documents the findings from their group Strategic Research Requirement that occurred over the academic year (from October 2023 to April 2024).
 Team Sullivan’s Travels consisted of LTC Joseph “Joe” Bell (USA, Aviation), COL John Cooper (USA, Human Resources), LTC Kristine “Kris” Hinds (USAR, Logistics), LtCol Erik Keim (USMC, Communications), and LTC Michael “Neal” Miller (USAR, Logistics), with Dr. Kathleen Moore as their USAWC Faculty Advisor. Multiple methodologies were used to determine its key findings — including a review of scholarly publications, open-source reporting, and nominal group technique — in response to the following strategic question posed by Ian Sullivan, Deputy Chief of Staff Intelligence, TRADOC G-2:
Team Sullivan’s Travels consisted of LTC Joseph “Joe” Bell (USA, Aviation), COL John Cooper (USA, Human Resources), LTC Kristine “Kris” Hinds (USAR, Logistics), LtCol Erik Keim (USMC, Communications), and LTC Michael “Neal” Miller (USAR, Logistics), with Dr. Kathleen Moore as their USAWC Faculty Advisor. Multiple methodologies were used to determine its key findings — including a review of scholarly publications, open-source reporting, and nominal group technique — in response to the following strategic question posed by Ian Sullivan, Deputy Chief of Staff Intelligence, TRADOC G-2:
How will innovations from contemporary conflicts likely shape the future dynamics of warfare, and what does it mean for Large Scale Combat Operations (LSCO) and pacing threats by 2035?
Today’s post excerpts the aforementioned Final Report’s Executive Summary; future Mad Scientist Laboratory blog posts and The Convergence podcasts will feature sections from the report highlighting findings by individual members from Team Sullivan’s Travels — Read on!]
Key Findings
How will innovations from contemporary conflicts likely shape the future dynamics of warfare, and what does it mean for Large Scale Combat Operations (LSCO) and pacing threats by 2035?
-
-
- What are likely potential changes to future warfighting functions?
-
-
-
- What are the likely impacts on future regional alliances, partnerships, and relationships?
-
Summarized Conclusion
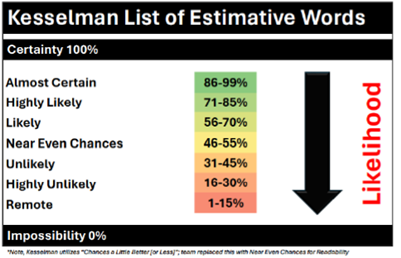
It is highly likely (71-86% — Note: The Kesselman List of Estimative Words legend may be found at the conclusion of this blog post, above the disclaimer statement) that innovations from recent conflicts will more fully integrate diverse actors into future conflict due to increased entry points enabled by Unprecedented Visibility, Rapid Technology Implementation, Lower Barriers to Entry, and Vulnerable Homelands. Despite the traditional role of militaries during the conflict, the ubiquity of technology and the treatment of Conflict as a Sandbox (i.e., testing bed) increases the rapid implementation of materiel and non-materiel applications by any party.
1. Unprecedented Visibility
Advancements in intelligence, surveillance, and reconnaissance (ISR), including inexpensive and rapid equipment production and accessibility of space and communications, are highly likely (71-85%) to create an environment of unprecedented visibility, making operations increasingly challenging.
Primary innovations influencing this outcome:
-
-
 Adaptive Integration (Blending, not Hiding). Hiding is the static act of concealing one’s presence. Blending is a proactive and dynamic process that involves assimilating into the environment to take advantage of its inherent patterns, behaviors, and characteristics. This requires altering visual, digital, or electromagnetic signatures.
Adaptive Integration (Blending, not Hiding). Hiding is the static act of concealing one’s presence. Blending is a proactive and dynamic process that involves assimilating into the environment to take advantage of its inherent patterns, behaviors, and characteristics. This requires altering visual, digital, or electromagnetic signatures.
-
-
-
- Hybrid Warfare. The cost-effectiveness, anonymity, reach, and capacity to directly engage with a target population through digital platforms in a connected world increases the number of actors actively engaging in disinformation and propaganda campaigns, manipulating social media, radicalizing individuals online, and directly recruiting and mobilizing for grey zone conflicts.
-
In Ukraine, local companies produce approximately three thousand drones daily for deployment against Russian forces. The $27 billion global commercial drone market sustains this effort, ensuring a near-constant supply for both sides of any future conflict. To counter this, both countries resorted to countermeasures, including anti-air missiles; Counter Rocket, Artillery, and Mortar (C-RAM) systems; networked acoustic sensors, and a variety of Electronic Warfare (EW) suites.

Over the last decade, companies like SpaceX revolutionized space accessibility through the rapid increase in space launches. This resulted in decreased costs of launching payloads into space and a surge in commercial satellite launches, increasing civilian access to satellite imagery and the ability to task satellites, giving anyone an unprecedented ability to influence conflict.

In communications, military-specific radio transmissions are easily detected, located, jammed, and intercepted. Ukrainians adopted digital camouflage to counter this, blending their transmissions with civilian communications. They exploited Russian vulnerabilities using agile software-defined radio systems for their EW efforts. The U.S. Marine Corps is testing a method that involves shifting transmissions from easily detected radio frequencies to nearly undetectable laser beams, increasing the digital bandwidth for further technological advances.
In Ukraine, the role of civilians in the intelligence apparatus grew significantly, with nearly everyone carrying a device capable of capturing and transmitting images or video. Oryx’s reporting of Russian equipment losses highlights the potential of crowdsourcing in the future.
2. Rapid, Technology Enhanced Warfare
It is highly likely (71-85%) that the rapid implementation and enhanced technological capabilities may increase the employment of information warfare, precision targeting, and tactical maneuver execution.
Primary innovations influencing this outcome:
-
-
- Artificial Intelligence: Generative and predictive artificial intelligence accelerate and guide tactical and operational decision-making. This increases visibility and targetability across all domains for various actors.
-
-
-
- Autonomous Systems: Human-in-the-loop, human-on-the-loop, and human-out-of-the-loop systems enhance the coordination and effectiveness of multi-domains, capabilities, and access points for all participants. The availability of autonomous systems provides a low-cost entry into conflict.
-
AI allows for rapid employment of information warfare by increasing the speed and potential influence sphere for information. At the onset of the Russian invasion of Ukraine, Russia used AI-guided technology to implore Ukrainians to surrender via a deep-fake video of President Zelensky. This demonstrates an AI-enabled tactic that can influence narratives rapidly.

Israel uses two AI systems, Lavender and Gospel, for precision targeting. Together, these systems enabled Israel to go from identifying 50 targets annually to over 100 daily, thus shortening kill chains.

In the Ukraine-Russia war, both sides deployed millions of Unmanned Aerial Vehicles (UAVs) equipped with AI-powered capabilities for surveillance, reconnaissance, and direct attacks. These drones can autonomously navigate complex environments, identify targets, and assess damage after attacks. The demand for these capabilities is only growing. Drones have many applications in military operations and commercial uses. In the military, they are employed for ISR and targeted strikes. Their prevalence in the commercial sector provides increased availability of commercial off-the-shelf items and increased research and development on this technology.
3. Lower Barriers to Entry and Blurred Lines of Conflict
Private sector, non-state actors, and individual citizens are highly likely (71-85%) to play pivotal roles in conflict and pre-conflict dynamics by leveraging commercially available technologies to conduct operations, gather intelligence, and influence public opinion. This allows broader conflict participation and agenda-driven actors to develop innovative technologies rapidly.
Primary innovations influencing this outcome:
-
-
- Fifth Generation Warfare: This loosely defined term describes contemporary conflicts in which tactics like social media influence operations, and cyberattacks play a more prominent role in warfare.
-
-
-
- Sixth Domain (Private Sector Involvement): Described by the Atlantic Council as the “sphere of activities” of the private sector in warfare. Private sector expertise, reach, and economic strength enable them to participate through cybersecurity, information, logistics, technology, infrastructure, and financial innovations and warfare.
-
 Access to affordable technology, connectivity, and anonymity allows average citizens to indirectly participate in cyberattacks, crowdsource information, analyze data from battlefield environments, share intelligence, engage in disinformation campaigns, and disseminate or encounter state-sponsored propaganda. With the rise of “digital dopamine,” discussed by Dr. Anna Lembke, author of Dopamine Nation, digital media increases the accessibility to receive and influence content. This, coupled with the rise of digital nodes, allows hackers to conduct offensive cyber-attacks or influence a narrative. At the corporate level, companies like Twitter, Facebook, and Google can police content or steer search results to portray a narrative deemed acceptable by that company.
Access to affordable technology, connectivity, and anonymity allows average citizens to indirectly participate in cyberattacks, crowdsource information, analyze data from battlefield environments, share intelligence, engage in disinformation campaigns, and disseminate or encounter state-sponsored propaganda. With the rise of “digital dopamine,” discussed by Dr. Anna Lembke, author of Dopamine Nation, digital media increases the accessibility to receive and influence content. This, coupled with the rise of digital nodes, allows hackers to conduct offensive cyber-attacks or influence a narrative. At the corporate level, companies like Twitter, Facebook, and Google can police content or steer search results to portray a narrative deemed acceptable by that company.
In Ukraine, the private sector actively leverages cyber, space, and AI to support its chosen side. American tech companies Palo Alto and Microsoft contributed to safeguarding data and protecting Ukrainian networks by setting up firewalls, protecting critical infrastructure, and safeguarding Ukrainian data by migrating the data to foreign servers. Companies offered help based on their own interests, not due to government mandates, and this influenced the course of the war between Ukraine and Russia.

Challenges can arise as companies provide “goodwill” support since they wield the power to turn that support off as they deem fit. SpaceX, for example, provided Starlink to the Ukrainians but later denied the service, preventing a Ukrainian drone from attacking a Russian naval fleet.
4. Vulnerable Homelands
Kinetic and non-kinetic attacks are highly likely (71-85%) to disrupt critical infrastructure and destabilize security in a homeland environment during a future conflict. Vulnerable homelands complicate the security paradigm due to the increased accessibility of targets, the information sphere, and the ability for anyone to impact them.
Primary innovations influencing this outcome:
-
-
- Water Warfare: Emerging concerns over scarcity in new regions, expanded economic utilization of water, and innovations in artificial intelligence (Internet of Things [IoT]) and autonomous systems broadened capabilities and access to impact water systems.
-
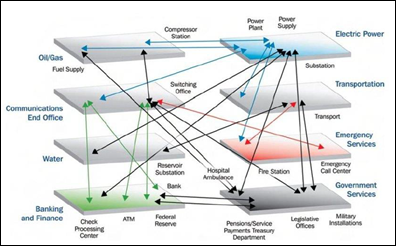
Essential services depend on Information and Communication Technology (ICT), enabling networked programs and processes through the IoT. The rapid growth of the IoT increased the number of entry points for adversaries to find and exploit vulnerabilities. Physical objects now have digital sensors, making everything a potential cyber target. These vulnerabilities transform civilian spaces into conflict zones, where the distinction between combatants and non-combatants blurs.
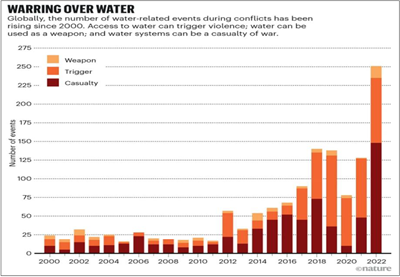
Cyberattacks have obstructed access to telecommunications and internet services, limited access to money, interrupted access to news, and disrupted or denied access to electricity, heating, and water. A hacker in Oldsmar, Florida, targeted the water supply and remotely altered the amount of sodium hydroxide in the water. Employees detected and thwarted a potentially deadly attack.
The use of conventional weapons in combination with these cyber operations amplifies the risks to the civilian population. Russia has focused on inflicting  damage to the civilian population through a combination of cyber and kinetic attacks – for example, by targeting energy infrastructure during winter. The hacking of Ukraine’s largest private energy company, DTEK, demonstrates the deliberate targeting of critical civilian infrastructure essential to populations.
damage to the civilian population through a combination of cyber and kinetic attacks – for example, by targeting energy infrastructure during winter. The hacking of Ukraine’s largest private energy company, DTEK, demonstrates the deliberate targeting of critical civilian infrastructure essential to populations.
The increased access within the information sphere creates a more vulnerable homeland. The spread of disinformation and propaganda undermines trust in institutions through information manipulation. The compromise of data, either hacked or leaked, leads to vast volumes of data on organizations and individuals published online with unknown long-term implications.
5. Conflict as a Sandbox
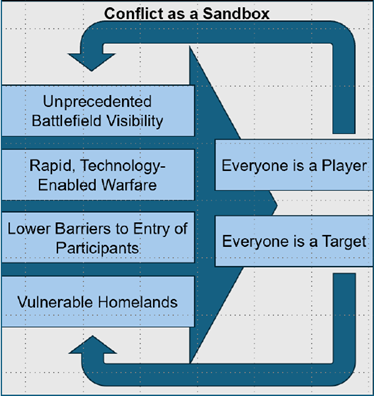 The future dynamics of warfare are highly likely (71-85%) to be shaped by the concept of “conflict as a sandbox.” This environment allows for the minimally restrictive application (testing) of new or immature strategies, concepts, and capabilities by militaries, the private sector, or citizens, thus impacting the trajectory of any conflict.
The future dynamics of warfare are highly likely (71-85%) to be shaped by the concept of “conflict as a sandbox.” This environment allows for the minimally restrictive application (testing) of new or immature strategies, concepts, and capabilities by militaries, the private sector, or citizens, thus impacting the trajectory of any conflict.
Conflict as a sandbox offers indirect participation into conflict, without direct escalation, and offers a testbed environment for countries and businesses to participate, often without loss of life or “boots on the ground.” This truly creates a future where everything is visible, everything is targetable, everyone is available, and everyone is accessible.
If you enjoyed today’s post, check out the Team Sullivan’s Travels‘ Future Dynamics of Warfare: Everyone is a Player, Everything is a Target Final Report in its entirety here.
Review our series of blog posts exploring what we’re learning about the Operational Environment:
Unmanned Capabilities in Today’s Battlespace
The Operational Environment’s Increased Lethality
WMD Threat: Now and in the Future
The Hard Part of Fighting a War: Contested Logistics
Revolutionizing 21st Century Warfighting: UAVs and C-UAS
Explore the TRADOC G-2‘s Operational Environment Enterprise web page, brimming with information on the Operational Environment (OE) and how our adversaries fight, including:
Our China Landing Zone, full of information regarding our pacing challenge, including ATP 7-100.3, Chinese Tactics, BiteSize China weekly topics, People’s Liberation Army Ground Forces Quick Reference Guide, and our thirty-plus snapshots captured to date addressing what China is learning about the Operational Environment from Russia’s war against Ukraine (note that a DoD Common Access Card [CAC] is required to access this last link).
Our Russia Landing Zone, including the BiteSize Russia weekly topics. If you have a CAC, you’ll be especially interested in reviewing our weekly RUS-UKR Conflict Running Estimates and associated Narratives, capturing what we learned about the contemporary Russian way of war in Ukraine over the past two years and the ramifications for U.S. Army modernization across DOTMLPF-P.
Our Running Estimates SharePoint site (also requires a CAC to access), containing our monthly OE Running Estimates, associated Narratives, and the 2QFY24 OE Assessment TRADOC Information Paper (TIP).
See the following related Mad Scientist Laboratory posts:
War Laid Bare and What the Joint Force can learn from K-Pop “Stans”, by Matthew Ader
LET’S TWEET, GRANDMA – Weaponizing the Social to Create Information Security, by CDR Sean M. Sullivan
Fundamental Questions Affecting Army Modernization
Democratized Intelligence, by Kate Kilgore
Space: Challenges and Opportunities
Integrating Artificial Intelligence into Military Operations, by Dr. James Mancillas
Takeaways Learned about the Future of the AI Battlefield and associated information paper
Rise of Artificial Intelligence: Implications to the Fielded Force, by John W. Mabes III
Insights from the Robotics and Autonomy Series of Virtual Events, as well as all of the associated webinar content (presenter biographies, slide decks, and notes) and associated videos
Russia-Ukraine Conflict: Sign Post to the Future (Part 1), by Kate Kilgore
Insights from Ukraine on the Operational Environment and the Changing Character of Warfare
Weaponized Information: What We’ve Learned So Far…, Insights from the Mad Scientist Weaponized Information Series of Virtual Events, and all of this series’ associated content and videos
In the Crosshairs: U.S. Homeland Infrastructure Threats
Water: A Fluid Challenge for the Future, by proclaimed Mad Scientist Caroline Duckworth
>>>>ONLY ONE WEEK LEFT! Army Mad Scientist wants to crowdsource your thoughts on asymmetric warfare — check out our Operational Environment Wicked Problems Writing Contest.
All entries must address the following topic:
How have innovations in asymmetric warfare impacted modern large scale and other combat operations, and what further evolutions could take place, both within the next 10 years and on towards mid-century?
We are accepting three types of submissions:
-
-
- 1500-word Non-Fiction Essay
-
-
-
- 1500-word Fictional Intelligence (FICINT) Story
-
-
-
- Hybrid 1500-word submission incorporating a short FICINT vignette, with a Non-Fiction Essay expounding on the threat capabilities described in the vignette
-
 Anyone can participate (Soldiers, Government Civilians, and all global citizens) — Multiple submissions are encouraged!
Anyone can participate (Soldiers, Government Civilians, and all global citizens) — Multiple submissions are encouraged!
All entries are due NLT 11:59 pm Eastern on May 16, 2024 at: madscitradoc@gmail.com
Click here for additional information on this contest — we look forward to your participation!
Disclaimer: The views expressed in this blog post do not necessarily reflect those of the U.S. Department of Defense, Department of the Army, Army Futures Command (AFC), or Training and Doctrine Command (TRADOC).



