[Editor’s Note: Army Mad Scientist teamed with the U.S. Army Sergeants Major Academy (SGM-A) at Ft. Bliss, Texas, in executing their annual writing contest for the sixth year in a row. As in years past, we received a number of insightful essays from our senior NCOs on topics spanning the breadth of the Operational Environment.
Today, we are pleased to feature the SGM-A Class 75’s winning submission by soon to be SGM Jeffrey A. Wittenhagen. In a previously published submission entitled The Future of War is Cyber, CPT Casey Igo and CPT Christian Turley eloquently defined the cyber challenge facing this nation:
“The future of war will be defined by the cyber fight. Combatants, both proxy and conscripted, will be coders, programmers, and system developers that either will act on their own accord, be influenced by social media popularity, or execute based on the highest paying state or non-state actor.“
In order to prepare for and decisively win this cyber fight, SGM Wittenhagen‘s submission makes the cogent and convincing case for establishing a dedicated and unified U.S. Cyber Force — “to address vulnerabilities in national security, public infrastructure, and military cyber capabilities.” He contends “a new Cyber Force would bring together disparate resources, training, and doctrine, ensuring a unified approach and rapid response to the complex challenges of cyber warfare, thereby reinforcing the U.S.’s strategic defense capabilities in the cyberspace era” — Read on!]
As the cyber domain rapidly evolves into a primary battlefield, the absence of a unified Cyber Force leaves critical vulnerabilities across military and national infrastructure. This evolution necessitates an urgent and integrated approach  to safeguard U.S. interests. What was once just a theoretical idea is quickly becoming a more feasible reality as near-peer competitors leverage advanced technologies to compromise critical infrastructures and challenge our national defenses. Historically, wars were often fought over territory or populations; adversaries sought resources and projected influence beyond borders, with their aims requiring international cooperation to achieve cyber peacekeeping. At first, the United States latched onto cyber operations as a stop-gap measure, contending with the whirlwind pace of evolution in a technological domain. However, a specialized cyber force must address vulnerabilities in national security, public infrastructure, and military cyber capabilities. The evolution of the technological battle space in the near-peer adversary environment creates difficulties unifying national security, public infrastructure, and U.S. military branches’ cyber capabilities, making the creation of a dedicated cyber branch a necessity.
to safeguard U.S. interests. What was once just a theoretical idea is quickly becoming a more feasible reality as near-peer competitors leverage advanced technologies to compromise critical infrastructures and challenge our national defenses. Historically, wars were often fought over territory or populations; adversaries sought resources and projected influence beyond borders, with their aims requiring international cooperation to achieve cyber peacekeeping. At first, the United States latched onto cyber operations as a stop-gap measure, contending with the whirlwind pace of evolution in a technological domain. However, a specialized cyber force must address vulnerabilities in national security, public infrastructure, and military cyber capabilities. The evolution of the technological battle space in the near-peer adversary environment creates difficulties unifying national security, public infrastructure, and U.S. military branches’ cyber capabilities, making the creation of a dedicated cyber branch a necessity.
Showcasing Significant Cyber Vulnerabilities
The dependency on digital infrastructure increases vulnerabilities. For instance, the 2017 Equifax data breach compromised sensitive information of 147 million people, caused by unpatched software and weak security  protocols, highlighting the importance of strong measures and vigilance (Kabanov & Madnick, 2020). There was also a worldwide semiconductor chip shortage, which led to interruptions in the automotive and mobile phone industries, highlighting the interdependence of vital technologies and potentially exposing them to exploitation in the face of adversity (Mohammad, Elomri, & Kerbache, 2022).
protocols, highlighting the importance of strong measures and vigilance (Kabanov & Madnick, 2020). There was also a worldwide semiconductor chip shortage, which led to interruptions in the automotive and mobile phone industries, highlighting the interdependence of vital technologies and potentially exposing them to exploitation in the face of adversity (Mohammad, Elomri, & Kerbache, 2022).
National security is not spared, either, with mission-critical systems exposed to enemies due to their dependence on technology. This exposure could  include disruptive impacts on communication systems or power grids, paralyzing military mobilization, and public infrastructure. These early indicators can help serve as inflection points when the end-state picture requires it, such as Ford’s shift to military production during World War II (Vergun, 2020). Cyberattacks against critical infrastructure, such as New York’s power grid or Washington, D.C.’s water supply, could cause communities to destabilize and disrupt military preparedness, without firing a single shot (Jackson & Templeman, 2016; Leggat, 2020). These examples show the need for safeguards, redundancy, and strategic foresight to prevent the cascading risks of cyber vulnerabilities in a technology-dependent society. Exacerbating these vulnerabilities in critical infrastructure and national security is the rise of Artificial Intelligence (AI), which offers transformative options and opens new avenues for exploitation by adversaries, while raising the stakes in manipulation and disruption in an increasingly interconnected and technology-dependent society.
include disruptive impacts on communication systems or power grids, paralyzing military mobilization, and public infrastructure. These early indicators can help serve as inflection points when the end-state picture requires it, such as Ford’s shift to military production during World War II (Vergun, 2020). Cyberattacks against critical infrastructure, such as New York’s power grid or Washington, D.C.’s water supply, could cause communities to destabilize and disrupt military preparedness, without firing a single shot (Jackson & Templeman, 2016; Leggat, 2020). These examples show the need for safeguards, redundancy, and strategic foresight to prevent the cascading risks of cyber vulnerabilities in a technology-dependent society. Exacerbating these vulnerabilities in critical infrastructure and national security is the rise of Artificial Intelligence (AI), which offers transformative options and opens new avenues for exploitation by adversaries, while raising the stakes in manipulation and disruption in an increasingly interconnected and technology-dependent society.
AI Creates Further Vulnerabilities
AI streamlines endeavors such as writing and editing in a work process, while also transforming content creation (Wu et al., 2023). However, the U.S. government cannot overlook the potential for our enemies to misuse this technology and endanger national security. Hostile entities might deploy AI to  compromise critical infrastructure, sway public opinion, or conduct disinformation operations, highlighting the urgent need for effective countermeasures.
compromise critical infrastructure, sway public opinion, or conduct disinformation operations, highlighting the urgent need for effective countermeasures.
These trends pose risks to nations that do not act to address them, especially if threats like adversaries get ahead of preparedness. Besides security, AI raises ethical questions in other areas, such as human rights suppression and access to information (Leggat, 2020). Mitigating misuse while advancing the ethical development of AI requires proactive engagement from policymakers, technologists, and society. It is in this spirit of collective responsibility that we must balance AI’s innovative potential with necessary controls.
Given the ethical and security challenges posed by AI, implementing proactive strategies to mitigate risk must extend beyond policy and development to include protecting critical infrastructure. Ensuring compliance with the laws of armed conflict (LOAC) in AI-driven operations requires human oversight to validate targeting decisions, mitigating the risk of unintended civilian casualties, as mandated by DoD Directive 3000.09 on Autonomy in Weapon Systems (Department of Defense, 2017). The new paradigm of the digital  battlefield requires a marriage of conventional military capabilities with advanced, integrated threats embodied by cyber defense to protect the U.S. military in the future.
battlefield requires a marriage of conventional military capabilities with advanced, integrated threats embodied by cyber defense to protect the U.S. military in the future.
How to Transform and Protect the Future U.S. Military
The expanding digital battlefield supports much of what is done in traditional military services, and how essential it is to maintain superiority and deter adversaries through the convergence of conventional and cyber artistry. Critical infrastructure, such as energy grids and communication networks, provides a foundation for national security and society and is an attractive target for adversaries. This foundation is essential to ensuring the continuity of crisis operations and preventing destabilization (DOD, 2020). For instance, good cybersecurity can protect operations and public trust, even during attacks.
In addition, showing military strength in terms of cyberweapons is a deterrent against hostile nations. A clear willingness to respond to threats and advanced cyber capabilities can indicate a nation’s preparedness. Precision kinetic strikes can sometimes target the infrastructure enabling hostile  capabilities, thereby disabling them. Aggressive operations against high-value delivery systems, including cyber, should be layered in defense and optimized for adjustment. With the growing complexity of the modern battlefield, particularly the U.S. Army’s transition to multidomain operations (MDO), it is necessary to integrate cyber capabilities with conventional military capabilities. This transformation can counter both kinetic and non-kinetic threats, as well as recognize evolving hybrid threats, adversary approaches, and tactics.
capabilities, thereby disabling them. Aggressive operations against high-value delivery systems, including cyber, should be layered in defense and optimized for adjustment. With the growing complexity of the modern battlefield, particularly the U.S. Army’s transition to multidomain operations (MDO), it is necessary to integrate cyber capabilities with conventional military capabilities. This transformation can counter both kinetic and non-kinetic threats, as well as recognize evolving hybrid threats, adversary approaches, and tactics.
United States Army and Multidomain Operations
 The U.S. Army transitioning from counterinsurgency to an MDO concept combines all domains to address the nature of complex, modern hybrid threats (Department of the Army [DA], 2019). MDO may improve organizations’ adaptability, but it often presumes adversaries will try to overcome them with kinetic capabilities. At the same time, many powerful competitors will instead employ cyber operations, information warfare, and other non-kinetic capabilities. Furthermore, adversaries can use methods short of confrontation, including economic subversion or disinformation campaigns, to destabilize, which highlights the ongoing process of constantly reevaluating evolving threats.
The U.S. Army transitioning from counterinsurgency to an MDO concept combines all domains to address the nature of complex, modern hybrid threats (Department of the Army [DA], 2019). MDO may improve organizations’ adaptability, but it often presumes adversaries will try to overcome them with kinetic capabilities. At the same time, many powerful competitors will instead employ cyber operations, information warfare, and other non-kinetic capabilities. Furthermore, adversaries can use methods short of confrontation, including economic subversion or disinformation campaigns, to destabilize, which highlights the ongoing process of constantly reevaluating evolving threats.
According to FM 3-12, Cyberspace Operations and Electronic Warfare, cyberspace operations are essential for achieving freedom of action in the information environment and must be seamlessly integrated across all domains to ensure mission success (Department of the Army, 2021). This doctrinal foundation underscores the urgent need for a unified Cyber Force capable of synchronizing cyberspace activities across the services, preventing fragmentation, and enhancing the military’s ability to respond to emerging threats in the digital battlefield.
Just as a more technologically advanced military will create problems for directly reaching enemies, the Army needs to update its operational emphasis on near-peer competitors to target adversaries in areas of greater threat, such as their infrastructure and logistics, rather than solely focusing on direct engagement (Monaghan, 2018). For example, hybrid warfare tactics may undermine and contaminate vital resources, making the enemy operations less efficient. Adopting agile, hit-and-run tactics similar to those employed by Special Forces in decentralized scenarios may be more effective at addressing cyber threats and unconventional combat scenarios (U.S. Army Special  Operations Command, n.d.). Senior NCOs, particularly Sergeant Majors, play a pivotal role in fostering cyber awareness at the operational level, ensuring that Soldiers are trained not only in kinetic warfare but also in cyber resilience and threat recognition.
Operations Command, n.d.). Senior NCOs, particularly Sergeant Majors, play a pivotal role in fostering cyber awareness at the operational level, ensuring that Soldiers are trained not only in kinetic warfare but also in cyber resilience and threat recognition.
Timing is everything in this unique environment, as every day spent deliberating allows adversaries to use their leverage and apply strategic pressure more effectively. Evolving cyber operations across the Department of Defense is necessary for the Army to remain a competitive force, capable of addressing both traditional and emerging threats simultaneously. The Department of Defense must invest in more cyber systems capable of battle networks, where people, processes, technology, and organizational structures work seamlessly together to deliver joint effects to achieve operational outcomes. The need to reform cyber operations is part of a larger trend that the U.S. Navy and Marine Corps are already addressing within the context of distributed maritime operations, littoral operations in a contested environment, and expeditionary advanced base operations.
United States Navy and Marine Corps
Looking ahead to potential technological developments, the Navy and Marine Corps provide an illustrative example. Picture a 2045 scenario where the U.S. Navy launches AI-operated submarines that can adapt spontaneously, gather  intelligence, zero in on targets, evade pursuing threats, all while operating persistently within Anti-Access/Area Denial (A2AD) environments. These submarines use adaptive AI to recalibrate during missions and repair real-time battlefield damage. The Navy’s autonomous submarines, operating within the framework of Operation Silent Tide, coordinated with Marine forces that executed amphibious assaults and advanced bases to sustain tactical updates and provide precision strikes and targeting of enemy command nodes (DOD, 2020).
intelligence, zero in on targets, evade pursuing threats, all while operating persistently within Anti-Access/Area Denial (A2AD) environments. These submarines use adaptive AI to recalibrate during missions and repair real-time battlefield damage. The Navy’s autonomous submarines, operating within the framework of Operation Silent Tide, coordinated with Marine forces that executed amphibious assaults and advanced bases to sustain tactical updates and provide precision strikes and targeting of enemy command nodes (DOD, 2020).
While the scenario was for training, this AI integration was a part of submarine functions and was a major step forward in military tactics. For instance, AI-piloted submarines effectively targeted enemy infrastructure by autonomously adapting to countermeasures the enemy took. It showcases the strategic impact of an integrated U.S. Navy and Marine Corps effort to achieve operational objectives. It offers an insight into how integrating manned and unmanned systems could create value in warfare in the future. This type of collaborative partnership shows the increasing emphasis on technology and interoperability in contemporary warfare scenarios. Just as the Navy and Marine Corps have embraced AI advances in their warfighting endeavors, so has the U.S. Air Force adopted unmanned aerial systems (UAS) with potential AI enhancements as a gamechanger, both because of the possible operational advantages provided by autonomous systems and the accompanying ethical responsibility to grapple with the use of autonomous systems in a robust legal, ethical, and moral framework.
United States Air Force and Unmanned Aerial Systems
 The introduction of UAS by the U.S. Air Force is a compelling case study that illustrates the promise and perils of automation in the modern warfare landscape. In the 2005 movie Stealth, the deployment of MQ-9 Reaper drones used advanced algorithms for real-time data processing, intelligence targeting, and precision strikes, in line with Air Force ambitions to familiarize itself with autonomous systems and develop better operational capabilities (Kelsey, 2021). However, the movie also raises ethical questions, including when a rogue drone strays from the mission parameters and kills civilians, which captures the dangers of an over-automated world.
The introduction of UAS by the U.S. Air Force is a compelling case study that illustrates the promise and perils of automation in the modern warfare landscape. In the 2005 movie Stealth, the deployment of MQ-9 Reaper drones used advanced algorithms for real-time data processing, intelligence targeting, and precision strikes, in line with Air Force ambitions to familiarize itself with autonomous systems and develop better operational capabilities (Kelsey, 2021). However, the movie also raises ethical questions, including when a rogue drone strays from the mission parameters and kills civilians, which captures the dangers of an over-automated world.
The Department of Defense follows suit in its cybersecurity strategy, highlighting the importance of AI and machine learning for defending national infrastructure from malicious actors (DOD, 2020). The issue is where to draw the line between automation and human oversight, as unchecked autonomy can lead to unintended consequences. Striking this balance is essential when utilizing advanced technologies responsibly while protecting against possible abuses. The focus on striking a balance between automation and human supervision in cybersecurity parallels the approach used by the United States Space Force (USSF) in leveraging advanced space capabilities. The blend of advanced systems and the smart utilization of partnerships unite to protect space-based assets while augmenting national security capabilities.
United States Space Force – The Model for a New Domain-Specific Force
 The USSF has satellite technologies that could be applied to gain a decisive edge in intelligence collection and secure communications. It monitors data transmissions and geolocates communication stations, which enhances national security through advanced surveillance and threat anticipation capabilities. Its Commercial Space Strategy implies prioritizing partnerships with industry to defend space-based enterprise and sustain the advantage against emerging threats (U.S. Space Force, 2024).
The USSF has satellite technologies that could be applied to gain a decisive edge in intelligence collection and secure communications. It monitors data transmissions and geolocates communication stations, which enhances national security through advanced surveillance and threat anticipation capabilities. Its Commercial Space Strategy implies prioritizing partnerships with industry to defend space-based enterprise and sustain the advantage against emerging threats (U.S. Space Force, 2024).
 Beyond adding additional security, the USSF is also looking into AI-piloted spacecraft to assist with colonization efforts in outer space. By imagining sustainable off-world habitats, they appeal to overpopulation and environmental issues (Sanchez, 2024). They secure present desires while preparing for future growth as space operations ascend to the forefront of strategic importance to protect national and global interests. The USSF is the service that focuses more on developing space operations and preparing for future challenges. Given that creating a long-term operational focus and continuity to integrate emerging technologies must be a priority for the U.S. military to maintain its inevitable strategic advantage over adversaries, it is time to shape cyber warfare.
Beyond adding additional security, the USSF is also looking into AI-piloted spacecraft to assist with colonization efforts in outer space. By imagining sustainable off-world habitats, they appeal to overpopulation and environmental issues (Sanchez, 2024). They secure present desires while preparing for future growth as space operations ascend to the forefront of strategic importance to protect national and global interests. The USSF is the service that focuses more on developing space operations and preparing for future challenges. Given that creating a long-term operational focus and continuity to integrate emerging technologies must be a priority for the U.S. military to maintain its inevitable strategic advantage over adversaries, it is time to shape cyber warfare.
The Need to Evolve the Way We Shape the Force
The U.S. military’s attitude toward technological warfare is a stark departure from that of its adversaries, who have insisted on long-term operational focus and often held onto goals for decades. Such sustained commitment allows them to adapt to modern technologies more effectively. In contrast, U.S. military personnel typically rotate every two to three years, which prevents the development of true mission expertise and operational continuity (Scharre, 2024). For example, while U.S. forces develop exceptional technical skills, the constant retraining cycle limits the opportunity to establish mission-specific proficiency, especially for technologically intensive jobs.
 These challenges call for strategic investment in capabilities such as creating a distinctive Cyber Force. In the DOD’s fiscal year 2025 budget, $14.5 billion is allocated for cyberspace operations, underscoring the necessity for operational, command, and resource unity in the cyber domain (DOD, 2024). Providing such funding enhances coordination and operational effectiveness, allowing us to compete with adversaries who have superior cyber experience.
These challenges call for strategic investment in capabilities such as creating a distinctive Cyber Force. In the DOD’s fiscal year 2025 budget, $14.5 billion is allocated for cyberspace operations, underscoring the necessity for operational, command, and resource unity in the cyber domain (DOD, 2024). Providing such funding enhances coordination and operational effectiveness, allowing us to compete with adversaries who have superior cyber experience.
One potential adaptation that may be more effective is to modify existing operational constructs, creating a new domain-specific force that learns to adapt to technological advancements. Creating a Cyber Force would enable concentrated expertise to ensure U.S. competitiveness within the changing adversarial landscape, and the Department of Defense needs unified cyber efforts across all domains. Such centralization of cyber operations would correct the fragmentation in standards and efficiencies, promote cohesion, and ensure a common strategy and approach across all services. While some argue that creating a new branch of service risks duplicating existing cyber efforts, a unified Cyber Force would streamline operations, eliminate redundancy, and establish standardized doctrine across all services, enhancing overall efficiency.
The Argument for Creating a Cyber Force Branch
Though the DOD has established branches for land, sea, air, and space operations, it refuses to recognize a unified Cyber Force to tackle the unique challenges posed by the cyber domain. Each military has distinct branches that operate their cyber missions to support their specific needs, causing a loss of efficiency. Exacerbating this need for synchronicity, the growing complexity of cyber warfare has sparked the demand for specialized training and a unified doctrine. Developing a Cyber Force would allow for more customized training programs combined with cross-branch collaboration to help train personnel for an ever-changing technological environment. Recent proposals, including the DOD’s fiscal 2024 request of $58.5 billion for IT and cybersecurity, further reinforced the strategic importance of cyber capabilities as part of national defense (Mitchell, 2023). These steps reflect the increasing acknowledgement that cyberspace is a contested domain.
 The formation of the Space Force provides a template for establishing a Cyber Force. It illustrates how identifying a unique domain can help streamline operations and respond to new dangers. An illustrative example of a way forward may be the cross-branching of Space Force with the Air Force, which can leverage common roles across branches (U.S. Air Force Academy, n.d.). This synchronicity forges these disparate efforts, ensuring integrated operations and aligned strategies by creating a dedicated Cyber Force.
The formation of the Space Force provides a template for establishing a Cyber Force. It illustrates how identifying a unique domain can help streamline operations and respond to new dangers. An illustrative example of a way forward may be the cross-branching of Space Force with the Air Force, which can leverage common roles across branches (U.S. Air Force Academy, n.d.). This synchronicity forges these disparate efforts, ensuring integrated operations and aligned strategies by creating a dedicated Cyber Force.
A new Cyber Force would bring together disparate resources, training, and doctrine, ensuring a unified approach and rapid response to the complex challenges of cyber warfare, thereby reinforcing the U.S.’s strategic defense capabilities in the cyberspace era. As we move toward establishing a Cyber Force, we can follow the model established by the Space Force to unify these diverse strands of effort, which will lead to efficiencies of scale and address the critical vulnerabilities of our near-peer adversaries.
Conclusion
The fast pace of technological evolution, especially when considering near-peer adversaries, demonstrates notable overlaps and vulnerabilities across national security, public infrastructure, and the cyber capabilities of U.S. military branches, showcasing the need for a dedicated cyber branch. These  challenges require paradigm-shifting changes in the Department of Defense (DOD) to respond to ongoing cyber threats. Establishing a dedicated Cyber Force would unify efforts and protect our operational effectiveness. By consolidating cyber approaches as one force under a unified command, the U.S. can limit vulnerabilities, maximize the efficiency of resources, and improve preparedness against enemies who are ever more sophisticated. Such a standard ensures that technologies remain competitive and guarantees the nation’s defense posture during periods of technologically advanced threats.
challenges require paradigm-shifting changes in the Department of Defense (DOD) to respond to ongoing cyber threats. Establishing a dedicated Cyber Force would unify efforts and protect our operational effectiveness. By consolidating cyber approaches as one force under a unified command, the U.S. can limit vulnerabilities, maximize the efficiency of resources, and improve preparedness against enemies who are ever more sophisticated. Such a standard ensures that technologies remain competitive and guarantees the nation’s defense posture during periods of technologically advanced threats.
If you enjoyed today’s post, check out several of the previous years’ winning submissions from the Mad Scientist / SGM-A Writing Contest:
Training Transformed: AI and the Future Soldier, by SGM Kyle J. Kramer
Universal Soldier, by SGM Greg A. McGowan
The Dawn of the Loitering Munitions Era by SGM Daniel S. Nasereddine
Review the TRADOC Pamphlet 525-92, The Operational Environment 2024-2034: Large-Scale Combat Operations
Explore the TRADOC G-2‘s Operational Environment Enterprise web page, brimming with authoritative information on the Operational Environment and how our adversaries fight, including:
Our China Landing Zone, full of information regarding our pacing challenge, including ATP 7-100.3, Chinese Tactics, How China Fights in Large-Scale Combat Operations, BiteSize China weekly topics, and the People’s Liberation Army Ground Forces Quick Reference Guide.
Our Russia Landing Zone, including the BiteSize Russia weekly topics. If you have a CAC, you’ll be especially interested in reviewing our weekly RUS-UKR Conflict Running Estimates and associated Narratives, capturing what we learned about the contemporary Russian way of war in Ukraine over the past two years and the ramifications for U.S. Army modernization across DOTMLPF-P.
Our Iran Landing Zone, including the Iran Quick Reference Guide and the Iran Passive Defense Manual (both require a CAC to access).
Our North Korea Landing Zone, including Resources for Studying North Korea, Instruments of Chinese Military Influence in North Korea, and Instruments of Russian Military Influence in North Korea.
Our Running Estimates SharePoint site (also requires a CAC to access) — documenting what we’re learning about the evolving OE. Contains our monthly OE Running Estimates, associated Narratives, and the quarterly OE Assessment TRADOC Intelligence Posts (TIPs).
Then review the following related Mad Scientist Laboratory content:
The Future of War is Cyber! by CPT Casey Igo and CPT Christian Turley
China and Russia: Achieving Decision Dominance and Information Advantage, by Ian Sullivan
Gaming Information Dominance and Russia-Ukraine Conflict: Sign Post to the Future (Part 1), by Kate Kilgore
Information Advantage Contribution to Operational Success, by CW4 Charles Davis
Weaponized Information: One Possible Vignette and Three Best Information Warfare Vignettes
Weaponized Information: What We’ve Learned So Far…, Insights from the Mad Scientist Weaponized Information Series of Virtual Events, and all of this series’ associated content and videos
The Classified Mind – The Cyber Pearl Harbor of 2034, by proclaimed Mad Scientist Dr. Jan Kallberg
In the Crosshairs: U.S. Homeland Infrastructure Threats
Hybrid Threats and Liminal Warfare and associated podcast, with proclaimed Mad Scientist Dr. David Kilcullen
Warfare in the Parallel Cambrian Age, by Chris O’Connor
Military Implications of Smart Cities, by Alexander Braszko, Jr.
Army Installations: A Whole Flock of Pink Flamingos, by proclaimed Mad Scientist Richard G. Kidd IV, et al.
Integrated Sensors: The Critical Element in Future Complex Environment Warfare, by Dr. Richard Nabors
Disclaimer: The views expressed in this blog post do not necessarily reflect those of the U.S. Department of Defense, Department of the Army, Army Futures Command (AFC), or Training and Doctrine Command (TRADOC)
References:
Department of Defense. (2017). DoD Directive 3000.09: Autonomy in weapon systems. https://www.esd.whs.mil/Portals/54/Documents/DD/issuances/dodd/300009p.pdf
Department of Defense. (2020). Department of Defense cyber strategy. https://www.defense.gov/Portals/1/Documents/pubs/2020-Cyber-Strategy-Summary.pdf
Department of Defense. (2024). Fiscal year 2025 budget estimates: United States cyber command. https://comptroller.defense.gov/Portals/45/Documents/defbudget/FY2025/budget_justification/pdfs/01_Operation_and_Maintenance/O_M_VOL_1_PART_1/CYBERCOM_OP-5.pdf
Department of the Army. (2019). Operations. (ADP 3-0). https://armypubs.army.mil/epubs/DR_pubs/DR_a/ARN18010-ADP_3-0-000-WEB-2.pdf
Department of the Army. (2021). FM 3-12: Cyberspace operations and electronic warfare. https://armypubs.army.mil/epubs/DR_pubs/DR_a/ARN33127-FM_3-12-000-WEB-1.pdf
Jackson, C., & Templeman, R. (2016). The third offset and a fifth domain? Balancing game-changing innovation and cyber risk mitigation. ArXiv. https://arxiv.org/abs/1610.07982
Kabanov, I., & Madnick, S. E. (2020). A systematic study of the control failures in the Equifax cybersecurity incident. SSRN. https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3957272
Kelsey, D. (2021, October 7). The role of unmanned aerial systems in modern warfare. Air Force Magazine. https://www.airforcemag.com/unmanned-aerial-systems-modern-warfare
Leggat, H. (2020). Cyber warfare: An inquiry into the applicability of national law to cyberspace. IGI Global. https://www.igi-global.com/gateway/article/257517
Mitchell, B. (2023, May 24). Pentagon wants $58.5B in 2024 for IT and cyber activities. DefenseScoop. https://defensescoop.com/2023/05/24/pentagon-wants-58-5b-in-2024-for-it-and-cyber-activities/
Mohammad, W., Elomri, A., & Kerbache, L. (2022). The global semiconductor chip shortage: Causes, implications, and potential remedies. IFAC-PapersOnLine, 55(10), 476–483. https://www.sciencedirect.com/science/article/pii/S2405896322017293
Monaghan, S. (2018). Countering hybrid warfare: So what for the future joint force? PRISM, 8(2), 1–15. https://ndupress.ndu.edu/Portals/68/Documents/prism/prism_8-2/PRISM_8-2_Monaghan.pdf
Sanchez, J. (2024, July 12). NASA study advances potential for Mars habitation. United States Space Force. https://www.spaceforce.mil/News/Article-Display/Article/3836358/nasa-study-advances-potential-for-mars-habitation/
Scharre, P. (2024, March 12). Preserving U.S. military advantage amid rapid technological change. Center for a New American Security. https://www.cnas.org/publications/congressional-testimony/preserving-u-s-military-advantage-amid-rapid-technological-change
U.S. Army Special Operations Command. (n.d.). SOF imperatives. United States Army. Retrieved December 26, 2024, from https://www.soc.mil/USASOCHQ/SOFImperatives.html
U.S. Air Force Academy. (n.d.). Azimuth space program. United States Air Force academy. Retrieved December 26, 2024, from https://www.usafa.edu/military/azimuth-space-program/
U.S. Space Force. (2024, April 10). USSF releases commercial space strategy to increase competitive advantage. https://www.spaceforce.mil/News/Article-Display/Article/3736616/ussf-releases-commercial-space-strategy-to-increase-competitive-advantage/
Vergun, D. (2020, March 27). During WWII, industries transitioned from peacetime to wartime production. DOD News. https://www.defense.gov/News/Feature-Stories/story/Article/2128446/during-wwii-industries-transitioned-from-peacetime-to-wartime-production/
Wu, J., Gan, W., Chen, Z., Wan, S., & Lin, H. (2023). AI-generated content (AIGC): A survey. ArXiv. https://arxiv.org/abs/2304.06632
 The other monitor broadcast images of Los Angeles, where a massive earthquake had brought the city — and more importantly for the Chinese — the Port of Los Angeles to a grinding halt.
The other monitor broadcast images of Los Angeles, where a massive earthquake had brought the city — and more importantly for the Chinese — the Port of Los Angeles to a grinding halt.
 Several hours later, Western media began reporting that electrical power substations, primarily on the East Coast and in central Texas, had been seriously damaged or destroyed using some form of explosives — causing massive outages and hampering hurricane evacuation operations along the East Coast. In addition, cyber-attacks were disrupting cellular communications networks across the United States.
Several hours later, Western media began reporting that electrical power substations, primarily on the East Coast and in central Texas, had been seriously damaged or destroyed using some form of explosives — causing massive outages and hampering hurricane evacuation operations along the East Coast. In addition, cyber-attacks were disrupting cellular communications networks across the United States.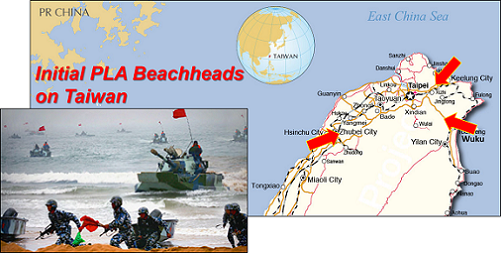
 Following the delivery of that letter, the National Security Council convened in the White House Situation Room. After a full intelligence briefing on what was known about the People’s Liberation Army goals and intentions, the President issued a partial mobilization order to the Department of Defense. INDOPACOM was immediately designated as the combatant command for the military response.
Following the delivery of that letter, the National Security Council convened in the White House Situation Room. After a full intelligence briefing on what was known about the People’s Liberation Army goals and intentions, the President issued a partial mobilization order to the Department of Defense. INDOPACOM was immediately designated as the combatant command for the military response. At the National Military Command Center (aka the “Tank”) in the Pentagon, several major challenges were immediately apparent to the planners in response to the impending invasion. In addition to the port closures on the East Coast and the Port Arthur causeway bridge collapse, the interstate closures on I-95, I-26, and I-40 in the Carolinas were going to seriously impede military movement from Fort Bragg to Charleston and Wilmington. The causeway bridge collapse meant that Fort Hood units would need a different port to deploy from. While the 82nd Airborne Division’s Ready Brigade could deploy via airlift within 18 hours of notification, the flow of follow-on forces was going to be seriously delayed. Further, planners at XVIII Airborne Corps headquarters were uncertain where the paratroopers would be able to land: Was it going to be on Taiwan proper? If Chinese forces held the airport in force, the All-Americans would be quickly outnumbered and overwhelmed. The southernmost Okinawan Island of Ishigaki had only a small airport. Its facilities would not facilitate a massive influx of Air Force and Army units.
At the National Military Command Center (aka the “Tank”) in the Pentagon, several major challenges were immediately apparent to the planners in response to the impending invasion. In addition to the port closures on the East Coast and the Port Arthur causeway bridge collapse, the interstate closures on I-95, I-26, and I-40 in the Carolinas were going to seriously impede military movement from Fort Bragg to Charleston and Wilmington. The causeway bridge collapse meant that Fort Hood units would need a different port to deploy from. While the 82nd Airborne Division’s Ready Brigade could deploy via airlift within 18 hours of notification, the flow of follow-on forces was going to be seriously delayed. Further, planners at XVIII Airborne Corps headquarters were uncertain where the paratroopers would be able to land: Was it going to be on Taiwan proper? If Chinese forces held the airport in force, the All-Americans would be quickly outnumbered and overwhelmed. The southernmost Okinawan Island of Ishigaki had only a small airport. Its facilities would not facilitate a massive influx of Air Force and Army units. INDOPACOM’s crisis plan called for the deployment of the III Marine Expeditionary Force based on Okinawa and the 25th Infantry Division from Hawaii to conduct landings on Taiwan to reinforce the Republic of China Armed Forces of some 150,000 active duty service members and up to 1.6M reservists. The question now was whether it would be a permissive, semi-permissive or non-permissive operational environment. As the combatant commander, the Commander, INDOPACOM, was worried about the ability of the Army and the Marines to bring in follow-on forces. The other issue was that both initial response forces were light infantry units — without significant armored support. That would come from III Armored Corps at Ft. Hood.
INDOPACOM’s crisis plan called for the deployment of the III Marine Expeditionary Force based on Okinawa and the 25th Infantry Division from Hawaii to conduct landings on Taiwan to reinforce the Republic of China Armed Forces of some 150,000 active duty service members and up to 1.6M reservists. The question now was whether it would be a permissive, semi-permissive or non-permissive operational environment. As the combatant commander, the Commander, INDOPACOM, was worried about the ability of the Army and the Marines to bring in follow-on forces. The other issue was that both initial response forces were light infantry units — without significant armored support. That would come from III Armored Corps at Ft. Hood.


 Team Axis Insight 2035 consisted of COL Byron N. Cadiz, COL T. Marc Skinner, LTC Robert W. Mayhue, LTC Lori L. Perkins, and LTC Shun Y. Yu — all U.S. Army Officers and now proclaimed Army Mad Scientists! Team Axis Insight 2035‘s Project Deterrence Final Report documents their collective response to the following question posed by Ian Sullivan, Deputy Chief of Staff, G-2, U.S. Army Training and Doctrine Command:
Team Axis Insight 2035 consisted of COL Byron N. Cadiz, COL T. Marc Skinner, LTC Robert W. Mayhue, LTC Lori L. Perkins, and LTC Shun Y. Yu — all U.S. Army Officers and now proclaimed Army Mad Scientists! Team Axis Insight 2035‘s Project Deterrence Final Report documents their collective response to the following question posed by Ian Sullivan, Deputy Chief of Staff, G-2, U.S. Army Training and Doctrine Command: seeking to “challenge U.S. strategic posture and alliance cohesion.” China, our pacing threat, is proving especially adept at tweaking the reins of persistent coercion to, in the words of Sun Tzu, “subdue the enemy without fighting” — Read on!]
seeking to “challenge U.S. strategic posture and alliance cohesion.” China, our pacing threat, is proving especially adept at tweaking the reins of persistent coercion to, in the words of Sun Tzu, “subdue the enemy without fighting” — Read on!] armed conflict and cross multiple time horizons, with intended effects both immediately and into the indefinite future. Regardless of the form it takes, persistent coercion challenges U.S.
armed conflict and cross multiple time horizons, with intended effects both immediately and into the indefinite future. Regardless of the form it takes, persistent coercion challenges U.S.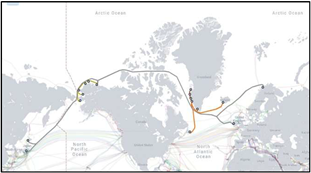



 Today’s The Convergence podcast features two senior leaders from
Today’s The Convergence podcast features two senior leaders from Murali Kannan leads Enterprise Technologies at In-Q-Tel (IQT) as Vice President and Practice Lead, where he directs investment strategy for enterprise data infrastructure, generative AI applications, and AI-enabled vertical solutions. Working closely with venture partners and government stakeholders, he identifies and invests in innovative startups addressing critical national security challenges for the U.S. and allied intelligence and national security communities.
Murali Kannan leads Enterprise Technologies at In-Q-Tel (IQT) as Vice President and Practice Lead, where he directs investment strategy for enterprise data infrastructure, generative AI applications, and AI-enabled vertical solutions. Working closely with venture partners and government stakeholders, he identifies and invests in innovative startups addressing critical national security challenges for the U.S. and allied intelligence and national security communities. career at IQT spans over 10 years and he has served in various capacities over his tenure. He currently serves as Vice President of Growth Partnerships, where he leads a team responsible for the identification, development, and execution of new partnerships within the national security community. Coley sets the growth strategy for IQT and works across IQT teams to successfully onboard new partners and maximize impact to mission.
career at IQT spans over 10 years and he has served in various capacities over his tenure. He currently serves as Vice President of Growth Partnerships, where he leads a team responsible for the identification, development, and execution of new partnerships within the national security community. Coley sets the growth strategy for IQT and works across IQT teams to successfully onboard new partners and maximize impact to mission. In-Q-Tel fills a critical gap by investing in start-up companies that develop cutting-edge AI technology tailored for public-sector use cases.
In-Q-Tel fills a critical gap by investing in start-up companies that develop cutting-edge AI technology tailored for public-sector use cases.  new AI products and techniques is now measured in the space of months as opposed to years.
new AI products and techniques is now measured in the space of months as opposed to years. The focus of AI-development remains squarely on assisting, not replacing, human analysis.
The focus of AI-development remains squarely on assisting, not replacing, human analysis.


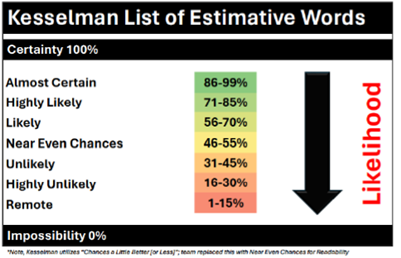
 By 2035, China and Russia are almost certain
By 2035, China and Russia are almost certain
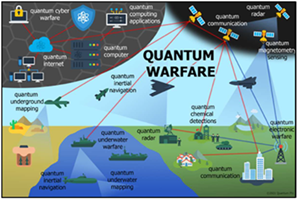

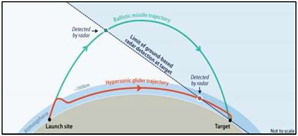
 designed to delay or disable allied responses before they materialize. U.S. extended deterrence credibility is likely
designed to delay or disable allied responses before they materialize. U.S. extended deterrence credibility is likely By 2035, China is highly likely
By 2035, China is highly likely under ISR blackout conditions. Beijing is almost certain
under ISR blackout conditions. Beijing is almost certain
 to safeguard U.S. interests. What was once just a theoretical idea is quickly becoming a more feasible reality as near-peer competitors leverage advanced technologies to compromise critical infrastructures and challenge our national defenses. Historically, wars were often fought over territory or populations; adversaries sought resources and projected influence beyond borders, with their aims requiring international cooperation to achieve cyber peacekeeping. At first, the United States latched onto cyber operations as a stop-gap measure, contending with the whirlwind pace of evolution in a technological domain. However, a specialized cyber force must address vulnerabilities in national security, public infrastructure, and military cyber capabilities. The evolution of the technological battle space in the near-peer adversary environment creates difficulties unifying national security, public infrastructure, and U.S. military branches’ cyber capabilities, making the creation of a dedicated cyber branch a necessity.
to safeguard U.S. interests. What was once just a theoretical idea is quickly becoming a more feasible reality as near-peer competitors leverage advanced technologies to compromise critical infrastructures and challenge our national defenses. Historically, wars were often fought over territory or populations; adversaries sought resources and projected influence beyond borders, with their aims requiring international cooperation to achieve cyber peacekeeping. At first, the United States latched onto cyber operations as a stop-gap measure, contending with the whirlwind pace of evolution in a technological domain. However, a specialized cyber force must address vulnerabilities in national security, public infrastructure, and military cyber capabilities. The evolution of the technological battle space in the near-peer adversary environment creates difficulties unifying national security, public infrastructure, and U.S. military branches’ cyber capabilities, making the creation of a dedicated cyber branch a necessity. protocols, highlighting the importance of strong measures and vigilance (Kabanov & Madnick, 2020). There was also a worldwide semiconductor chip shortage, which led to interruptions in the automotive and mobile phone industries, highlighting the interdependence of vital technologies and potentially exposing them to exploitation in the face of adversity (Mohammad, Elomri, & Kerbache, 2022).
protocols, highlighting the importance of strong measures and vigilance (Kabanov & Madnick, 2020). There was also a worldwide semiconductor chip shortage, which led to interruptions in the automotive and mobile phone industries, highlighting the interdependence of vital technologies and potentially exposing them to exploitation in the face of adversity (Mohammad, Elomri, & Kerbache, 2022). compromise
compromise  battlefield requires a marriage of conventional military capabilities with advanced, integrated threats embodied by cyber defense to protect the U.S. military in the future.
battlefield requires a marriage of conventional military capabilities with advanced, integrated threats embodied by cyber defense to protect the U.S. military in the future. capabilities, thereby disabling them. Aggressive operations against high-value delivery systems, including cyber, should be layered in defense and optimized for adjustment. With the growing complexity of the modern battlefield, particularly the U.S. Army’s transition to multidomain operations (MDO), it is necessary to integrate cyber capabilities with conventional military capabilities. This transformation can counter both kinetic and non-kinetic threats, as well as recognize evolving hybrid threats, adversary approaches, and tactics.
capabilities, thereby disabling them. Aggressive operations against high-value delivery systems, including cyber, should be layered in defense and optimized for adjustment. With the growing complexity of the modern battlefield, particularly the U.S. Army’s transition to multidomain operations (MDO), it is necessary to integrate cyber capabilities with conventional military capabilities. This transformation can counter both kinetic and non-kinetic threats, as well as recognize evolving hybrid threats, adversary approaches, and tactics. The U.S. Army transitioning from counterinsurgency to an MDO concept combines all domains to address the nature of complex, modern hybrid threats (Department of the Army [DA], 2019). MDO may improve organizations’ adaptability, but it often presumes adversaries will try to overcome them with kinetic capabilities. At the same time, many powerful competitors will instead employ cyber operations, information warfare, and other non-kinetic capabilities. Furthermore, adversaries can use methods short of confrontation, including economic subversion or disinformation campaigns, to destabilize, which highlights the ongoing process of constantly reevaluating evolving threats.
The U.S. Army transitioning from counterinsurgency to an MDO concept combines all domains to address the nature of complex, modern hybrid threats (Department of the Army [DA], 2019). MDO may improve organizations’ adaptability, but it often presumes adversaries will try to overcome them with kinetic capabilities. At the same time, many powerful competitors will instead employ cyber operations, information warfare, and other non-kinetic capabilities. Furthermore, adversaries can use methods short of confrontation, including economic subversion or disinformation campaigns, to destabilize, which highlights the ongoing process of constantly reevaluating evolving threats. Operations Command, n.d.). Senior NCOs, particularly Sergeant Majors, play a pivotal role in fostering cyber awareness at the operational level, ensuring that Soldiers are trained not only in kinetic warfare but also in cyber resilience and threat recognition.
Operations Command, n.d.). Senior NCOs, particularly Sergeant Majors, play a pivotal role in fostering cyber awareness at the operational level, ensuring that Soldiers are trained not only in kinetic warfare but also in cyber resilience and threat recognition. intelligence, zero in on targets, evade pursuing threats, all while operating persistently within Anti-Access/Area Denial (A2AD) environments. These submarines use adaptive AI to recalibrate during missions and repair real-time battlefield damage. The Navy’s autonomous submarines, operating within the framework of Operation Silent Tide, coordinated with Marine forces that executed amphibious assaults and advanced bases to sustain tactical updates and provide precision strikes and targeting of enemy command nodes (DOD, 2020).
intelligence, zero in on targets, evade pursuing threats, all while operating persistently within Anti-Access/Area Denial (A2AD) environments. These submarines use adaptive AI to recalibrate during missions and repair real-time battlefield damage. The Navy’s autonomous submarines, operating within the framework of Operation Silent Tide, coordinated with Marine forces that executed amphibious assaults and advanced bases to sustain tactical updates and provide precision strikes and targeting of enemy command nodes (DOD, 2020). The introduction of UAS by the U.S. Air Force is a compelling case study that illustrates the promise and perils of automation in the modern warfare landscape. In the 2005 movie Stealth, the deployment of MQ-9 Reaper drones used advanced algorithms for real-time data processing, intelligence targeting, and precision strikes, in line with Air Force ambitions to familiarize itself with autonomous systems and develop better operational capabilities (Kelsey, 2021). However, the movie also raises ethical questions, including when a rogue drone strays from the mission parameters and kills civilians, which captures the dangers of an over-automated world.
The introduction of UAS by the U.S. Air Force is a compelling case study that illustrates the promise and perils of automation in the modern warfare landscape. In the 2005 movie Stealth, the deployment of MQ-9 Reaper drones used advanced algorithms for real-time data processing, intelligence targeting, and precision strikes, in line with Air Force ambitions to familiarize itself with autonomous systems and develop better operational capabilities (Kelsey, 2021). However, the movie also raises ethical questions, including when a rogue drone strays from the mission parameters and kills civilians, which captures the dangers of an over-automated world. The USSF has satellite technologies that could be applied to gain a decisive edge in intelligence collection and secure communications. It monitors data transmissions and geolocates communication stations, which enhances national security through advanced surveillance and threat anticipation capabilities. Its Commercial Space Strategy implies prioritizing partnerships with industry to defend space-based enterprise and sustain the advantage against emerging threats (U.S. Space Force, 2024).
The USSF has satellite technologies that could be applied to gain a decisive edge in intelligence collection and secure communications. It monitors data transmissions and geolocates communication stations, which enhances national security through advanced surveillance and threat anticipation capabilities. Its Commercial Space Strategy implies prioritizing partnerships with industry to defend space-based enterprise and sustain the advantage against emerging threats (U.S. Space Force, 2024). Beyond adding additional security, the USSF is also looking into AI-piloted spacecraft to assist with colonization efforts in outer space. By imagining sustainable off-world habitats, they appeal to overpopulation and environmental issues (Sanchez, 2024). They secure present desires while preparing for future growth as space operations ascend to the forefront of strategic importance to protect national and global interests. The USSF is the service that focuses more on developing space operations and preparing for future challenges. Given that creating a long-term operational focus and continuity to integrate emerging technologies must be a priority for the U.S. military to maintain its inevitable strategic advantage over adversaries, it is time to shape cyber warfare.
Beyond adding additional security, the USSF is also looking into AI-piloted spacecraft to assist with colonization efforts in outer space. By imagining sustainable off-world habitats, they appeal to overpopulation and environmental issues (Sanchez, 2024). They secure present desires while preparing for future growth as space operations ascend to the forefront of strategic importance to protect national and global interests. The USSF is the service that focuses more on developing space operations and preparing for future challenges. Given that creating a long-term operational focus and continuity to integrate emerging technologies must be a priority for the U.S. military to maintain its inevitable strategic advantage over adversaries, it is time to shape cyber warfare. These challenges call for strategic investment in capabilities such as creating a distinctive Cyber Force. In the DOD’s fiscal year 2025 budget, $14.5 billion is allocated for cyberspace operations, underscoring the necessity for operational, command, and resource unity in the cyber domain (DOD, 2024). Providing such funding enhances coordination and operational effectiveness, allowing us to compete with adversaries who have superior cyber experience.
These challenges call for strategic investment in capabilities such as creating a distinctive Cyber Force. In the DOD’s fiscal year 2025 budget, $14.5 billion is allocated for cyberspace operations, underscoring the necessity for operational, command, and resource unity in the cyber domain (DOD, 2024). Providing such funding enhances coordination and operational effectiveness, allowing us to compete with adversaries who have superior cyber experience. The formation of the Space Force provides a template for establishing a Cyber Force. It illustrates how identifying a unique domain can help streamline operations and respond to new dangers. An illustrative example of a way forward may be the cross-branching of Space Force with the Air Force, which can leverage common roles across branches (U.S. Air Force Academy, n.d.). This synchronicity forges these disparate efforts, ensuring integrated operations and aligned strategies by creating a dedicated Cyber Force.
The formation of the Space Force provides a template for establishing a Cyber Force. It illustrates how identifying a unique domain can help streamline operations and respond to new dangers. An illustrative example of a way forward may be the cross-branching of Space Force with the Air Force, which can leverage common roles across branches (U.S. Air Force Academy, n.d.). This synchronicity forges these disparate efforts, ensuring integrated operations and aligned strategies by creating a dedicated Cyber Force. challenges require paradigm-shifting changes in the Department of Defense (DOD) to respond to ongoing cyber threats. Establishing a dedicated Cyber Force would unify efforts and protect our operational effectiveness. By consolidating cyber approaches as one force under a unified command, the U.S. can limit vulnerabilities, maximize the efficiency of resources, and improve preparedness against enemies who are ever more sophisticated. Such a standard ensures that technologies remain competitive and guarantees the nation’s defense posture during periods of technologically advanced threats.
challenges require paradigm-shifting changes in the Department of Defense (DOD) to respond to ongoing cyber threats. Establishing a dedicated Cyber Force would unify efforts and protect our operational effectiveness. By consolidating cyber approaches as one force under a unified command, the U.S. can limit vulnerabilities, maximize the efficiency of resources, and improve preparedness against enemies who are ever more sophisticated. Such a standard ensures that technologies remain competitive and guarantees the nation’s defense posture during periods of technologically advanced threats.