(Editor’s Note: Mad Scientist Laboratory is pleased to present Dr. Peter Emanuel’s guest blog post, illustrating how popular culture often presages actual technological advancements and scientific breakthroughs.)
 Did Dick Tracy’s wrist watch telephone or Star Trek’s communicator inspire future generations of scientists and engineers to build today’s smartphone? Or were they simply depicting the inevitable manifestation of future technology?
Did Dick Tracy’s wrist watch telephone or Star Trek’s communicator inspire future generations of scientists and engineers to build today’s smartphone? Or were they simply depicting the inevitable manifestation of future technology?  If we look back on old issues of Superman comic books that depict a 3D printer half a century before it was invented, we can see popular media has foreshadowed future technology, time and time again. Clearly, there are many phenomena, from time travel to force fields, that have not, and may not ever see the light of day; however, there are enough examples to suggest that dedicated and forward thinking scientists, trying to defend the United States, should consider this question:
If we look back on old issues of Superman comic books that depict a 3D printer half a century before it was invented, we can see popular media has foreshadowed future technology, time and time again. Clearly, there are many phenomena, from time travel to force fields, that have not, and may not ever see the light of day; however, there are enough examples to suggest that dedicated and forward thinking scientists, trying to defend the United States, should consider this question:
Can comic books, video games, television, and movies give us a glimpse into the battlefield of the future?
For today’s Mad Scientist blog, consider what the future may hold for defense against weapons of mass destruction.
 Let’s get the 800 lb. gorilla out of the room first! Or, perhaps, the 800 lb. dinosaur by talking about biological warfare in the future. The movie Jurassic Park depicts the hubris of man trying to control life by “containing” its DNA. Our deeper understanding of DNA shows us that life is programmed to be redundant and error prone. It’s actually a fundamental feature that drives evolution. In the year 2050, if we are to control our genetically modified products, we must master containment and control for a system designed since the dawn of time to NOT be contained. Forget bio-terror…What about bio-Error?!
Let’s get the 800 lb. gorilla out of the room first! Or, perhaps, the 800 lb. dinosaur by talking about biological warfare in the future. The movie Jurassic Park depicts the hubris of man trying to control life by “containing” its DNA. Our deeper understanding of DNA shows us that life is programmed to be redundant and error prone. It’s actually a fundamental feature that drives evolution. In the year 2050, if we are to control our genetically modified products, we must master containment and control for a system designed since the dawn of time to NOT be contained. Forget bio-terror…What about bio-Error?!  Furthermore, the lesson in Jurassic Park from the theft of the frozen dinosaur eggs shows us the asymmetric impact that theft of genetic products can yield. Today, our adversaries amass databases on our genetic histories through theft and globalization and one only has to ask, “What do they know that we should be worried about?”
Furthermore, the lesson in Jurassic Park from the theft of the frozen dinosaur eggs shows us the asymmetric impact that theft of genetic products can yield. Today, our adversaries amass databases on our genetic histories through theft and globalization and one only has to ask, “What do they know that we should be worried about?”
 Let’s move from biology to chemistry. A chemist will argue that biology is just chemistry, and at some level it’s true. Like the movie Outlander and anime like Cowboy Bebop, today’s Middle East battlefield shows the use of CAPTAGON, an addictive narcotic blend used to motivate and subjugate radical Islamists. In 2050, our mastery of tailored chemistry will likely lead to more addictive or targeted drug use that could elicit unpredictable or illogical behaviors. Controlled delivery of mood/behavior altering drugs will frustrate efforts to have a military workforce managed by reliability programs and will require layered and redundant controls even on trusted populations. Such vulnerabilities will likely be a justification for placing weapons
Let’s move from biology to chemistry. A chemist will argue that biology is just chemistry, and at some level it’s true. Like the movie Outlander and anime like Cowboy Bebop, today’s Middle East battlefield shows the use of CAPTAGON, an addictive narcotic blend used to motivate and subjugate radical Islamists. In 2050, our mastery of tailored chemistry will likely lead to more addictive or targeted drug use that could elicit unpredictable or illogical behaviors. Controlled delivery of mood/behavior altering drugs will frustrate efforts to have a military workforce managed by reliability programs and will require layered and redundant controls even on trusted populations. Such vulnerabilities will likely be a justification for placing weapons  and infrastructure under some level of artificial intelligence in the year 2050. Imagine this is the part of the blog where we talked about the Terminator and CyberDyne Systems.
and infrastructure under some level of artificial intelligence in the year 2050. Imagine this is the part of the blog where we talked about the Terminator and CyberDyne Systems.
 Today, the thought of man-machine interfaces depicted by the Borg from Star Trek and the TV shows such as Aeon Flux and Ghost in the Shell may make our skin crawl. In 2050, societal norms will likely evolve to embrace these driven by the competitive advantage that implants and augmentation affords. Cyborgs and genetic chimeras will blur the line between what is man and what is machine; it will usher in an era when a computer virus can kill, and it will further complicate our ability to identify friend from foe in a way best depicted by the recent Battlestar Galactica TV show.
Today, the thought of man-machine interfaces depicted by the Borg from Star Trek and the TV shows such as Aeon Flux and Ghost in the Shell may make our skin crawl. In 2050, societal norms will likely evolve to embrace these driven by the competitive advantage that implants and augmentation affords. Cyborgs and genetic chimeras will blur the line between what is man and what is machine; it will usher in an era when a computer virus can kill, and it will further complicate our ability to identify friend from foe in a way best depicted by the recent Battlestar Galactica TV show.  Will the point of need manufacturing systems of the future be soulless biological factories like those depicted in Frank Herbert’s book series, “Dune”? As we prepare for engaging in a multi-domain battlespace by extending our eyes and ears over the horizon with swarming autonomous drones are we opening a window into the heart and mind of our future fighting force?
Will the point of need manufacturing systems of the future be soulless biological factories like those depicted in Frank Herbert’s book series, “Dune”? As we prepare for engaging in a multi-domain battlespace by extending our eyes and ears over the horizon with swarming autonomous drones are we opening a window into the heart and mind of our future fighting force?
 Some final thoughts for the year 2050 when we maintain a persistent presence off planet Earth. As Robert Heinlein predicted, and recent NASA experiments proved, our DNA changes during prolonged exposure to altered gravity. What of humans who never stepped foot on Earth’s surface, as shown in the recent movie, The Fate of our Stars. Eventually, non-terrestrially based populations will diverge from the gene pool, perhaps kindling a debate on what is truly human? Will orbiting satellites with hyperkinetic weapons such as were pictured in GI Joe Retaliation
Some final thoughts for the year 2050 when we maintain a persistent presence off planet Earth. As Robert Heinlein predicted, and recent NASA experiments proved, our DNA changes during prolonged exposure to altered gravity. What of humans who never stepped foot on Earth’s surface, as shown in the recent movie, The Fate of our Stars. Eventually, non-terrestrially based populations will diverge from the gene pool, perhaps kindling a debate on what is truly human? Will orbiting satellites with hyperkinetic weapons such as were pictured in GI Joe Retaliation add another dimension to the cadre of weapons of mass destruction? I would argue that popular media can help spur these discussions and give future mad scientists a glimpse into the realm of the possible. To that end, I think we can justify a little binge watching in the name of national security!
add another dimension to the cadre of weapons of mass destruction? I would argue that popular media can help spur these discussions and give future mad scientists a glimpse into the realm of the possible. To that end, I think we can justify a little binge watching in the name of national security!
 If you enjoyed this post, please check out the following:
If you enjoyed this post, please check out the following:
– Headquarters, U.S. Army Training and Doctrine Command (TRADOC) is co-sponsoring the Bio Convergence and Soldier 2050 Conference with SRI International at Menlo Park, California, on 08-09 March 2018. Click here to learn more about the conference, the associated on-line game, and then watch the live-streamed proceedings, starting at 0840 PST / 1140 EST on 08 March 2018.
– Our friends at Small Wars Journal are continuing to publish the finalists from our most recent Call for Ideas — click here to check them out!
Dr. Peter Emanuel is the Army’s Senior Research Scientist (ST) for Bioengineering. In this role, he advises Army Leadership on harnessing the opportunities that synthetic biology and biotechnology can bring to National Security.

 (Editor’s Note: Originally published under the same title in
(Editor’s Note: Originally published under the same title in  The Vinge and Kruzweil articulation of the “Singularity” of biological and machine intelligence is much closer than most of us understand. The majority of the people in the world are caught up in the inertia of everyday activities, and the emergence of Virtual War is opaque to most of us. To that end and for clarity, the world is experiencing Virtual War – A Revolution in Human Affairs.
The Vinge and Kruzweil articulation of the “Singularity” of biological and machine intelligence is much closer than most of us understand. The majority of the people in the world are caught up in the inertia of everyday activities, and the emergence of Virtual War is opaque to most of us. To that end and for clarity, the world is experiencing Virtual War – A Revolution in Human Affairs.  within the defense industrial base, and among law enforcement agencies. Virtual War is drastically transforming global human affairs as we know them, and in ways that we do not yet understand. Eric Schmidt got it right when he opined that,
within the defense industrial base, and among law enforcement agencies. Virtual War is drastically transforming global human affairs as we know them, and in ways that we do not yet understand. Eric Schmidt got it right when he opined that,

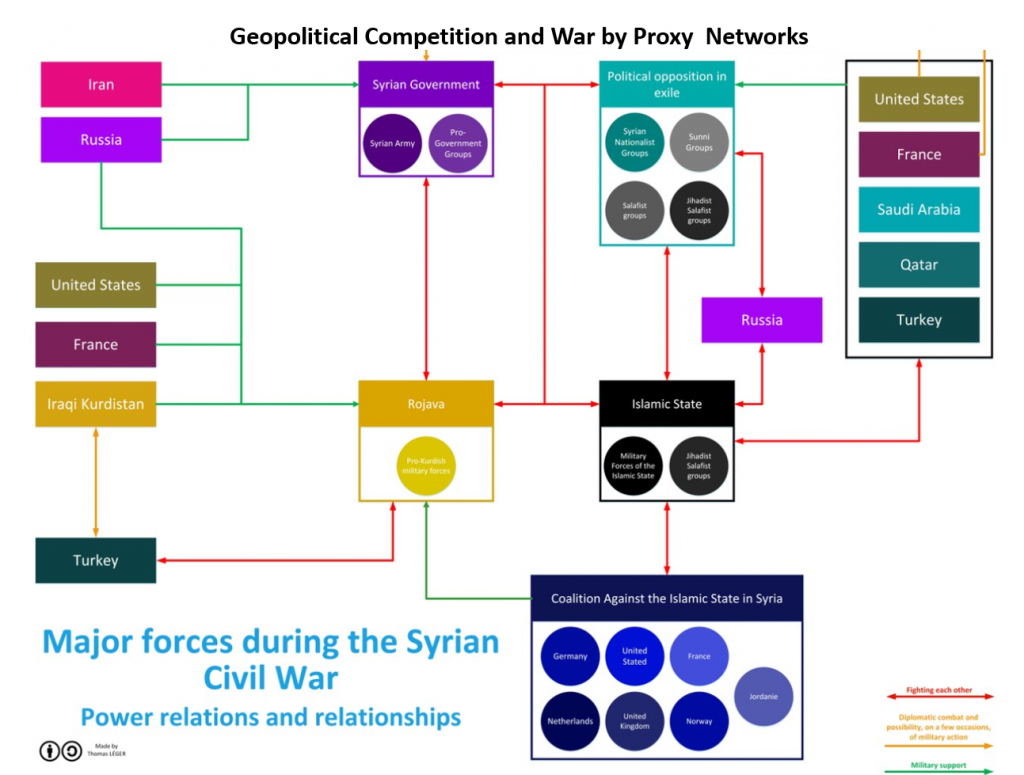
 Hundreds of other terror attacks have taken place around the world since 9/11, and were planned and coordinated in Virtual Space before the horrific attacks took place in Physical Space. What will the world’s security paradigm for warfare and law enforcement look like when the Internet of Things (IoTs) evolves to the Internet of Everything (IoET), that includes much more powerful Nano-Biologically
Hundreds of other terror attacks have taken place around the world since 9/11, and were planned and coordinated in Virtual Space before the horrific attacks took place in Physical Space. What will the world’s security paradigm for warfare and law enforcement look like when the Internet of Things (IoTs) evolves to the Internet of Everything (IoET), that includes much more powerful Nano-Biologically  The growing liminality which exists today, by way of virtual space activity, is causing a truth crisis, as the velocity of human interaction and the velocity of information is at an all-time high. The average person does not know what to believe given the ubiquity of information and the obvious bias in government and within traditional and non-traditional media sources.
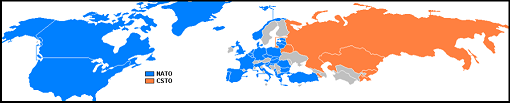
The growing liminality which exists today, by way of virtual space activity, is causing a truth crisis, as the velocity of human interaction and the velocity of information is at an all-time high. The average person does not know what to believe given the ubiquity of information and the obvious bias in government and within traditional and non-traditional media sources. On the socio-economic front, there is a growing divide between the rich and poor, as the middle class struggles with sustainability. There is also a widening chasm between globalist and nationalist. The 1648 Westphalian nation-state model is at odds with a growing number of emergent empowered actors who do not rely on monolithic state entities to govern their behavior in virtual or physical space. Each of these aforementioned variables are all interdependently joined and, to varying degrees, are technologically driven fissures in the world today.
On the socio-economic front, there is a growing divide between the rich and poor, as the middle class struggles with sustainability. There is also a widening chasm between globalist and nationalist. The 1648 Westphalian nation-state model is at odds with a growing number of emergent empowered actors who do not rely on monolithic state entities to govern their behavior in virtual or physical space. Each of these aforementioned variables are all interdependently joined and, to varying degrees, are technologically driven fissures in the world today. 
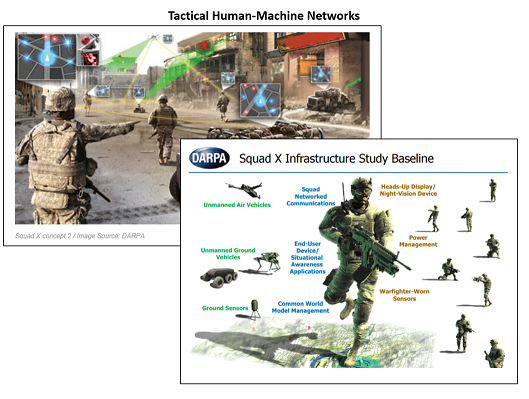
 1) Bio convergence with advanced computing is happening at the edge. Humans will become part of the network connected through their embedded and worn devices. From transhumanism to theorizing about uploading the brain, the Future OE will not be an internet of things but the internet of everything (including humans).
1) Bio convergence with advanced computing is happening at the edge. Humans will become part of the network connected through their embedded and worn devices. From transhumanism to theorizing about uploading the brain, the Future OE will not be an internet of things but the internet of everything (including humans). 2) The next 50 years will see an evolution in human society; we will be augmented by Artificial Intelligence (AI), partner with AI in centaur chess fashion, and
2) The next 50 years will see an evolution in human society; we will be augmented by Artificial Intelligence (AI), partner with AI in centaur chess fashion, and  3) This augmentation and enhanced AI partnering will require hyper-connected humans with wearables and eventually embeddables to provide continuous diagnostics and human-machine interface.
3) This augmentation and enhanced AI partnering will require hyper-connected humans with wearables and eventually embeddables to provide continuous diagnostics and human-machine interface. 4) The Army will need to measure cognitive potential and baseline neural activity of its
4) The Army will need to measure cognitive potential and baseline neural activity of its  5) The Army needs new training tools to take advantage of neuralplasticity and realize the full cognitive potential of Soldiers. Brain gyms and the promise of Augmented and Virtual Reality (AR/VR) training sets could accelerate learning and, in some cases, challenge the tyranny of “the 10,000 hour rule.”
5) The Army needs new training tools to take advantage of neuralplasticity and realize the full cognitive potential of Soldiers. Brain gyms and the promise of Augmented and Virtual Reality (AR/VR) training sets could accelerate learning and, in some cases, challenge the tyranny of “the 10,000 hour rule.” 6) Human enhancement, the unlocking of the genome, and improving AI will stress the
6) Human enhancement, the unlocking of the genome, and improving AI will stress the  7)
7)  8) Cognitive enhancement and
8) Cognitive enhancement and  9) Chemical and bio defense will need to be much more sophisticated on the next battlefield. The twin challenges of democratization and proliferation have resulted in a world where the capability of engineering
9) Chemical and bio defense will need to be much more sophisticated on the next battlefield. The twin challenges of democratization and proliferation have resulted in a world where the capability of engineering  10) We are missing the full impact of bio on all emerging trends. We must focus beyond human enhancement and address how bio is impacting materials, computing, and garage level, down scaled innovation.
10) We are missing the full impact of bio on all emerging trends. We must focus beyond human enhancement and address how bio is impacting materials, computing, and garage level, down scaled innovation.
 In order to regain this technological edge, the Department of Defense has crafted a
In order to regain this technological edge, the Department of Defense has crafted a  Much has been written about efforts to make U.S. military unmanned systems more
Much has been written about efforts to make U.S. military unmanned systems more 

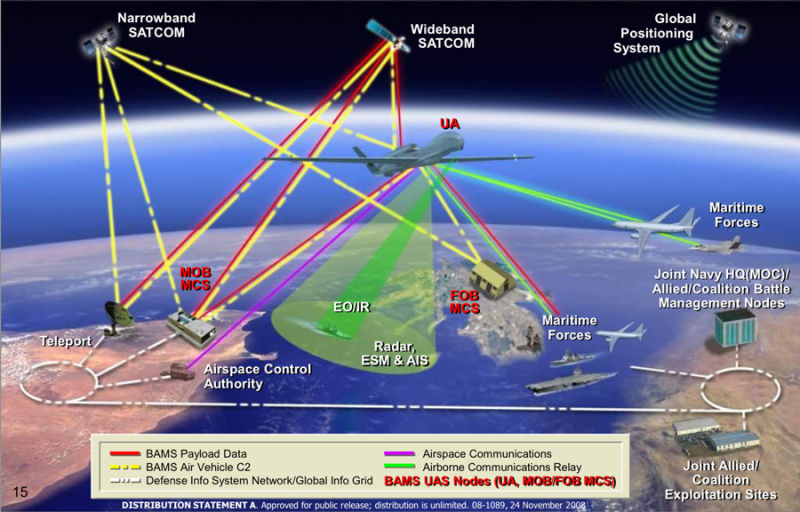
 For lethal military unmanned systems, the bar is higher for what the operator must know before authorizing the unmanned warfighting partner to fire a weapon — or as is often the case — recommending that higher authority authorize lethal action. Take the case of military operators managing an ongoing series of unmanned aerial systems flights that have been watching a terrorist and waiting for higher authority to give the authorization to take out the threat using an air-to-surface missile fired from that UAS.
For lethal military unmanned systems, the bar is higher for what the operator must know before authorizing the unmanned warfighting partner to fire a weapon — or as is often the case — recommending that higher authority authorize lethal action. Take the case of military operators managing an ongoing series of unmanned aerial systems flights that have been watching a terrorist and waiting for higher authority to give the authorization to take out the threat using an air-to-surface missile fired from that UAS. 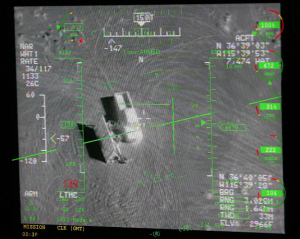

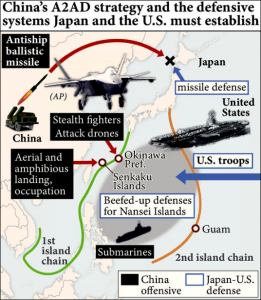
 The character of war, strategy development, and operational level challenges are changing; therefore operational approaches must do the same.
The character of war, strategy development, and operational level challenges are changing; therefore operational approaches must do the same.