 [Editor’s Note: Mad Scientist would like to thank everyone who participated in the Mad Scientist Global Perspectives in the Operational Environment Virtual Conference on 29 January 2020 — from our co-hosts at the Army Futures Command (AFC) and the U.S. Army Training and Doctrine Command (TRADOC) International Army Programs Directorate (IAPD); to TRADOC’s Foreign Liaison Officer community and the U.S. Army liaison officers overseas who helped us identify and coordinate with international subject matter experts; to each of the briefers who presented their respective nations’ insightful perspectives on a diverse array of topics affecting the Operational Environment (OE); to our audience who attended virtually via the TRADOC Watch page’s
[Editor’s Note: Mad Scientist would like to thank everyone who participated in the Mad Scientist Global Perspectives in the Operational Environment Virtual Conference on 29 January 2020 — from our co-hosts at the Army Futures Command (AFC) and the U.S. Army Training and Doctrine Command (TRADOC) International Army Programs Directorate (IAPD); to TRADOC’s Foreign Liaison Officer community and the U.S. Army liaison officers overseas who helped us identify and coordinate with international subject matter experts; to each of the briefers who presented their respective nations’ insightful perspectives on a diverse array of topics affecting the Operational Environment (OE); to our audience who attended virtually via the TRADOC Watch page’s  interactive chat room and asked penetrating questions that significantly helped broaden our aperture on the OE and the changing character of warfare. Today’s post documents the key takeaways Mad Scientist captured from the conference — Enjoy!]
interactive chat room and asked penetrating questions that significantly helped broaden our aperture on the OE and the changing character of warfare. Today’s post documents the key takeaways Mad Scientist captured from the conference — Enjoy!]
Our first Mad Scientist Virtual Conference focused on global perspectives of the operational environment. While our presenters represented only a small part of the globe, these countries do account for a significant percentage of global defense expenditures and have international defense related engagements and responsibilities.
 As expected, we heard many similarities between the Operational Environment described by the United States Army and the presenters from France, the Netherlands, Germany, the UK, Canada, and our NATO Panel. We also identified some interesting nuances in how potential challenges and threats are described and which ones are emphasized.
As expected, we heard many similarities between the Operational Environment described by the United States Army and the presenters from France, the Netherlands, Germany, the UK, Canada, and our NATO Panel. We also identified some interesting nuances in how potential challenges and threats are described and which ones are emphasized.
Here are a few takeaways from the conference — if they pique your interest, check out this conference’s Mad Scientist APAN (All Partners Access Network) page for the associated slides and video presentations (to be posted)!
1) Interoperability is key but increasingly difficult with uneven modernization and different policies for emerging technologies. Each country emphasized the future of coalition operations, but they also described interoperability in different ways. This ranged from the classic definition of  interoperability of radios, firing data, and common operating pictures to tactical integration with a country’s units inside another country’s formations. Emerging technologies like Artificial Intelligence (AI) add another level of difficulty to interoperability. Each country will develop their own AI policies outlining legal levels of autonomy and coding standards for identifying biases and ensuring transparency. How these different AI capabilities will interact in fast pace machine-to-machine collaboration is not clear.
interoperability of radios, firing data, and common operating pictures to tactical integration with a country’s units inside another country’s formations. Emerging technologies like Artificial Intelligence (AI) add another level of difficulty to interoperability. Each country will develop their own AI policies outlining legal levels of autonomy and coding standards for identifying biases and ensuring transparency. How these different AI capabilities will interact in fast pace machine-to-machine collaboration is not clear.
2) Asymmetry of Ethics is a Pink Flamingo (known challenge without program to address it) Each country mentioned the developing and differing standards for  AI. It was commonly understood that competition and conflict is speeding up but there is no clear consensus on what the tactical and operational advantages could be for an adversary that chooses to integrate AI in a more permissive manner than accepted by western armed forces. Also, lagging policy, regulations, and laws in the West create a possibility for overmatch by these potential adversaries. This is an area where experimentation with differing AI policies and approaches might identify the risks of strategic and technological surprise.
AI. It was commonly understood that competition and conflict is speeding up but there is no clear consensus on what the tactical and operational advantages could be for an adversary that chooses to integrate AI in a more permissive manner than accepted by western armed forces. Also, lagging policy, regulations, and laws in the West create a possibility for overmatch by these potential adversaries. This is an area where experimentation with differing AI policies and approaches might identify the risks of strategic and technological surprise.
3) Weaponization of information to attack societies and their armed forces is the #1 described threat and it wasn’t even close. This is understandable as  our European allies are closer geographically to the persistent Russian competition activities. The emphasis of this threat differs from the United States Army where we have focused and experimented around the idea of a return to high intensity conflict with a near–peer competitor. While each presenter discussed ongoing organizational, doctrinal, and capability changes to address the information environment, it was widely understood that this is a military problem without a military solution.
our European allies are closer geographically to the persistent Russian competition activities. The emphasis of this threat differs from the United States Army where we have focused and experimented around the idea of a return to high intensity conflict with a near–peer competitor. While each presenter discussed ongoing organizational, doctrinal, and capability changes to address the information environment, it was widely understood that this is a military problem without a military solution.
4) Climate change and mass migration are the conflict drivers of most concern. Human migration  as a consequence of climate change will create new security concerns for impacted countries as well as neighboring regions and, due to European geography, seemed to be of greater concern than our focus on great power conflict.
as a consequence of climate change will create new security concerns for impacted countries as well as neighboring regions and, due to European geography, seemed to be of greater concern than our focus on great power conflict.
5) Virtual training is increasingly important for Armies with decreasing defense budgets and the demand to improve training proficiencies. As realistic synthetic training becomes a reality, we can more readily transition troops trained for a host of contingencies in the virtual world to the rigors of diverse  operations in the physical world. This Synthetic Training Environment may also facilitate Joint and inter-coalition training of geographically-disparate assets and formations, with the concomitant issue of interoperability to conduct combined training events in the future.
operations in the physical world. This Synthetic Training Environment may also facilitate Joint and inter-coalition training of geographically-disparate assets and formations, with the concomitant issue of interoperability to conduct combined training events in the future.
6) As society evolves and changes, so does warfare. Our presenters described several pressures on their societies that are not part of or are only tangentially mentioned in the U.S. Army’s operational narrative:
-
- Declining demographics in western nations pose potential recruitment and reconstitution challenges.
- Nationalism is rising and could result in an erosion of rules-based international order. If these systems break down, smaller nations will be challenged.
- Authoritarian systems are rising and exporting technology to support other authoritarian governments. At the same time democratic systems are weakening.
- Aging populations and slow growth economies are seeing a global shift of economic strength from the West to the East.

In the future, we will host another global perspectives conference that will include presenters from Asia and South America to further broaden our perspectives and identify potential blind spots from these regions. For now, we encourage the international community to continue to share their ideas by taking our Global Perspectives Survey. Preliminary findings were presented at this conference. Stay tuned to the Mad Scientist Laboratory as we will publish the results of this survey in a series of assessments, starting in March…
… don’t forget to enter The Operational Environment in 2035 Mad Scientist Writing Contest and share your unique insights on the future of warfighting — click here to learn more (deadline for submission is 1 March 2020!)…
… and a quick reminder that the U.S. Army Mission Command Battle Lab Futures Branch is also conducting its Command Post of the Future – 2040-2050 Writing Contest. Click here to learn more about suggested contest writing prompts, rules, and how to submit your entry — deadline for their writing contest is also 1 March 2020!



 Ethnic Russian minorities’ agitation against their respective governments in Estonia, Lithuania, and Latvia spike. Simultaneously, the Russian Government ratchets up tensions, with inflammatory statements of support for these ethnic Russian minorities in the Baltic States; coordinated movements and exercises by Russian ground, naval, and air forces adjacent to the region; and clandestine support to ethnic Russians in these States. The Russian Government started a covert campaign to shape people’s views about the threats against the Russian diaspora. More than 200,000 twitter accounts send 3.6 million tweets trending #protectRussianseverywhere. This sprawling Russian disinformation campaign is focused on building internal support for the Russian President and a possible military action. The U.S. and NATO respond…
Ethnic Russian minorities’ agitation against their respective governments in Estonia, Lithuania, and Latvia spike. Simultaneously, the Russian Government ratchets up tensions, with inflammatory statements of support for these ethnic Russian minorities in the Baltic States; coordinated movements and exercises by Russian ground, naval, and air forces adjacent to the region; and clandestine support to ethnic Russians in these States. The Russian Government started a covert campaign to shape people’s views about the threats against the Russian diaspora. More than 200,000 twitter accounts send 3.6 million tweets trending #protectRussianseverywhere. This sprawling Russian disinformation campaign is focused on building internal support for the Russian President and a possible military action. The U.S. and NATO respond… The 2nd Cav Regt is placed on alert; as it prepares to roll out of garrison for Poland, several videos surface across social media, purportedly showing the sexual assault of several underage German nationals by U.S. personnel. These disturbingly graphic
The 2nd Cav Regt is placed on alert; as it prepares to roll out of garrison for Poland, several videos surface across social media, purportedly showing the sexual assault of several underage German nationals by U.S. personnel. These disturbingly graphic  the Regiment. German political and legal authorities call for an investigation and host nation protests erupt outside the gates of Rose Barracks, Vilseck, disrupting the unit’s deployment.
the Regiment. German political and legal authorities call for an investigation and host nation protests erupt outside the gates of Rose Barracks, Vilseck, disrupting the unit’s deployment. Social media accounts are hacked/hijacked, with false threats by dependents to execute mass/school shootings, accusations of sexual abuse, hate speech posts by Leaders about their minority troops, and revelations of adulterous affairs between unit spouses.
Social media accounts are hacked/hijacked, with false threats by dependents to execute mass/school shootings, accusations of sexual abuse, hate speech posts by Leaders about their minority troops, and revelations of adulterous affairs between unit spouses. Russia’s GRU (Military Intelligence) employs AI Generative Adversarial Networks (GANs) to create fake persona injects that mimic select U.S. Active Army, ARNG, and USAR commanders making disparaging statements about their confidence in our allies’ forces, the legitimacy of the mission, and their faith in our political leadership. Sowing these injects across unit social media accounts, Russian Information Warfare specialists seed doubt and erode trust in the chain of command amongst a percentage of susceptible Soldiers, creating further friction in deployment preparations.
Russia’s GRU (Military Intelligence) employs AI Generative Adversarial Networks (GANs) to create fake persona injects that mimic select U.S. Active Army, ARNG, and USAR commanders making disparaging statements about their confidence in our allies’ forces, the legitimacy of the mission, and their faith in our political leadership. Sowing these injects across unit social media accounts, Russian Information Warfare specialists seed doubt and erode trust in the chain of command amongst a percentage of susceptible Soldiers, creating further friction in deployment preparations. As these units load at railheads or begin their road march towards their respective ports of embarkation,
As these units load at railheads or begin their road march towards their respective ports of embarkation,  navigation systems to cause sealift asset collisions and groundings at key maritime chokepoints. The fly-by-wire avionics are hacked on a departing C-17, causing a crash with the loss of all 134 Soldiers onboard. All C-17s are grounded, pending an investigation.
navigation systems to cause sealift asset collisions and groundings at key maritime chokepoints. The fly-by-wire avionics are hacked on a departing C-17, causing a crash with the loss of all 134 Soldiers onboard. All C-17s are grounded, pending an investigation. the alliance for the Multi-Domain Common Operating Picture. Spoofing of these systems leads to accidental air defense engagements, resulting in Blue-on-Blue fratricide or the downing of a commercial airliner, with additional civilian deaths on the ground from spent ordnance, providing more opportunities for Russian Information Operations to spread acrimony within the alliance and create dissent in public opinion back home.
the alliance for the Multi-Domain Common Operating Picture. Spoofing of these systems leads to accidental air defense engagements, resulting in Blue-on-Blue fratricide or the downing of a commercial airliner, with additional civilian deaths on the ground from spent ordnance, providing more opportunities for Russian Information Operations to spread acrimony within the alliance and create dissent in public opinion back home. across the net via bots, these instances further stoke anti-Baltic / anti-U.S. opinion amongst Russian-sympathetic and non-aligned populations alike.
across the net via bots, these instances further stoke anti-Baltic / anti-U.S. opinion amongst Russian-sympathetic and non-aligned populations alike. The release of deepfake videos showing Baltic security forces massacring ethnic Russians creates further division and causes some NATO partners to hesitate, question, and withhold their support, as required under Article 5. The alliance is rent asunder — Checkmate!
The release of deepfake videos showing Baltic security forces massacring ethnic Russians creates further division and causes some NATO partners to hesitate, question, and withhold their support, as required under Article 5. The alliance is rent asunder — Checkmate!
 • Robotics: Forty plus countries develop military robots with some level of autonomy. Impact on society, employment.
• Robotics: Forty plus countries develop military robots with some level of autonomy. Impact on society, employment. • Artificial Intelligence: Human-Agent Teaming, where humans and intelligent systems work together to achieve either a physical or mental task. The human and the intelligent system will trade-off cognitive and physical loads in a collaborative fashion.
• Artificial Intelligence: Human-Agent Teaming, where humans and intelligent systems work together to achieve either a physical or mental task. The human and the intelligent system will trade-off cognitive and physical loads in a collaborative fashion. • Swarms/Semi Autonomous: Massed, coordinated, fast, collaborative, small, stand-off. Overwhelm target systems. Mass or disaggregate.
• Swarms/Semi Autonomous: Massed, coordinated, fast, collaborative, small, stand-off. Overwhelm target systems. Mass or disaggregate. • Internet of Things (IoT): Trillions of internet linked items create opportunities and vulnerabilities. Explosive growth in low Size Weight and Power (SWaP) connected devices (Internet of Battlefield Things), especially for sensor applications (situational awareness). Greater than 100 devices per human. Significant end device processing (sensor analytics, sensor to shooter, supply chain management).
• Internet of Things (IoT): Trillions of internet linked items create opportunities and vulnerabilities. Explosive growth in low Size Weight and Power (SWaP) connected devices (Internet of Battlefield Things), especially for sensor applications (situational awareness). Greater than 100 devices per human. Significant end device processing (sensor analytics, sensor to shooter, supply chain management). • Space: Over 50 nations operate in space, increasingly congested and difficult to monitor, endanger Positioning, Navigation, and Timing (PNT)
• Space: Over 50 nations operate in space, increasingly congested and difficult to monitor, endanger Positioning, Navigation, and Timing (PNT) • Hyper Velocity Weapons:
• Hyper Velocity Weapons: • Directed Energy Weapons: Signature not visible without technology, must dwell on target. Power requirements currently problematic.
• Directed Energy Weapons: Signature not visible without technology, must dwell on target. Power requirements currently problematic. • Synthetic Biology: Engineering / modification of biological entities
• Synthetic Biology: Engineering / modification of biological entities • Information Environment: Use IoT and sensors to harness the flow of information for situational understanding and decision-making advantage.
• Information Environment: Use IoT and sensors to harness the flow of information for situational understanding and decision-making advantage.
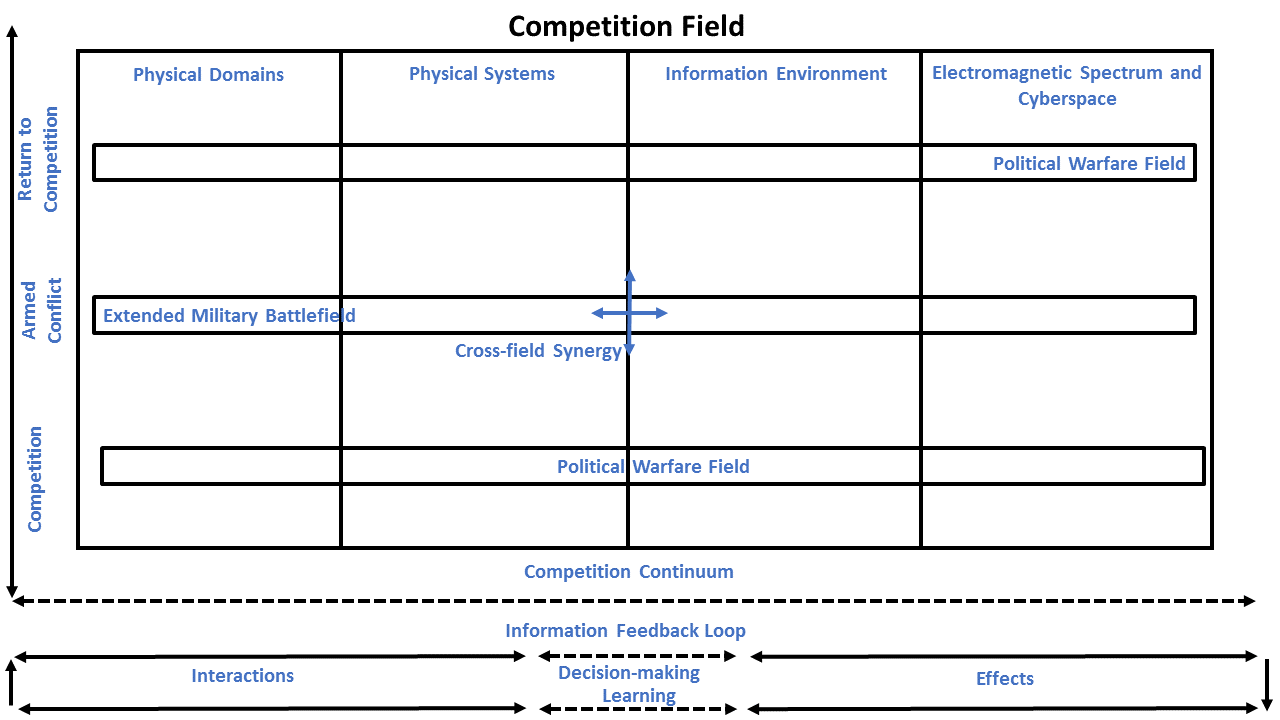
 The concept applies quantum field theory to political warfare and the “extended battlefield,” where Joint and multinational systems are the quanta of these fields, prone to excitable states like field quanta. In quantum mechanics, “quanta” refers to the minimum amount of physical entity involved in an interaction, like a photon or bit. The concept also unites the “
The concept applies quantum field theory to political warfare and the “extended battlefield,” where Joint and multinational systems are the quanta of these fields, prone to excitable states like field quanta. In quantum mechanics, “quanta” refers to the minimum amount of physical entity involved in an interaction, like a photon or bit. The concept also unites the “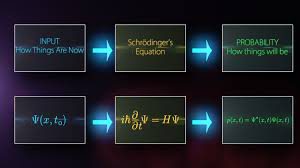 System and particle interactions are uncertain and not deterministic predictions described in exporting security as preventive war strategy and Newtonian physics. Measures short of war and war itself (i.e., violent or armed competition) are interactions in the competition field based on convergence, acceleration, force, distance, time, and other variables. Systems or things do not enter into relations; relations ground the notion of the system.
System and particle interactions are uncertain and not deterministic predictions described in exporting security as preventive war strategy and Newtonian physics. Measures short of war and war itself (i.e., violent or armed competition) are interactions in the competition field based on convergence, acceleration, force, distance, time, and other variables. Systems or things do not enter into relations; relations ground the notion of the system.  These dimensions or fields include the quanta of human beings, Internet of Things (IoT), data, and
These dimensions or fields include the quanta of human beings, Internet of Things (IoT), data, and  In theories of quantum gravity, that “thing” is the quanta of gravity, hypothetically called a graviton. In this assessment, it is the quanta of competition. The quanta of competition are not in competition; they are themselves competition and are described by links and the relation they express. The quanta of competition are also suited for quantum biology, since they involve both biological and environmental objects and problem sets.
In theories of quantum gravity, that “thing” is the quanta of gravity, hypothetically called a graviton. In this assessment, it is the quanta of competition. The quanta of competition are not in competition; they are themselves competition and are described by links and the relation they express. The quanta of competition are also suited for quantum biology, since they involve both biological and environmental objects and problem sets.