[Editor’s Note: In today’s post, returning guest blogger and proclaimed Mad Scientist Howard R. Simkin addresses the ramifications of democratized genomic engineering in the Operational Environment (OE). Comparing the genetic engineering tool Clustered Regularly Interspaced Short Palindromic Repeats (CRISPR) to the internet in terms of its revolutionary potential, Mr. Simkin examines three scenarios where this capability could be harnessed for nefarious purposes. (Note: Some of the embedded links in this post are best accessed using non-DoD networks.)]
“The Future is already here. It’s just not very evenly distributed.” – William Gibson, science fiction author who coined the word cyberspace in 1984.1
Purpose:
This paper briefly examines the convergence of trends in technology as they affect CRISPR2 technology through the lens of three possible users of the technology – the Democratic People’s Republic of Korea (DPRK), a future Aum Shinrikyo3 -like entity, and a Unabomber-like4 super-empowered individual.
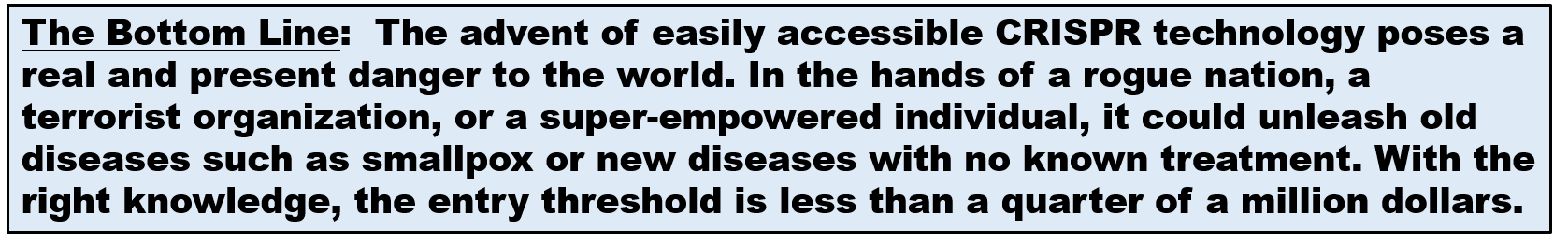
What does the Future Operating Environment (FOE) tell us?
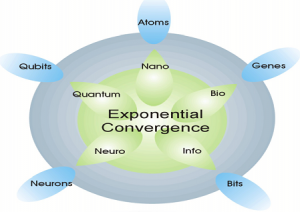
A survey of the two most commonly available, authoritative sources on the FOE points to an ever-increasing rate of technological change, the growth of mega-cities, and the diffusion of cutting-edge technology into the hands of both state and non-state actors as well as super-empowered individuals.5 Over the next ten to twenty years, the world will experience dramatic changes in technology. Governments and businesses are investing billions of dollars into research programs and tech startups associated with all five of the technological fields shown in Figure 1.6
The convergence of these technologies, impelled by increasingly capable Artificial Intelligence (AI) will drive change that will approximate that of Moore’s Law – doubling in power while halving in cost every two years. Our adversaries – states, non-state actors, and super-empowered individuals – will undoubtedly seek to harness these trends to accomplish their ends. To examine the many implications of these changes is beyond the scope of this paper. Instead, this post will concentrate on one specific technology – CRISPR.
Background
 CRISPR may be the next Internet – in terms of the impact it will have on society. CRISPR only became approved for use on humans in 2015. However, its applications to gene editing have already become significant.7 As the web magazine Futurism observed, “As the accuracy, efficiency, and cost-effectiveness of the system became more and more apparent, researchers and pharmaceutical companies jumped on the technique, modifying it, improving it, and testing it on different genetic issues.”8 This tool could lead to gene editing techniques that could strengthen disease resistance and improve strength and mental abilities. It could also lead to designer diseases for humans, plants, and animals.
CRISPR may be the next Internet – in terms of the impact it will have on society. CRISPR only became approved for use on humans in 2015. However, its applications to gene editing have already become significant.7 As the web magazine Futurism observed, “As the accuracy, efficiency, and cost-effectiveness of the system became more and more apparent, researchers and pharmaceutical companies jumped on the technique, modifying it, improving it, and testing it on different genetic issues.”8 This tool could lead to gene editing techniques that could strengthen disease resistance and improve strength and mental abilities. It could also lead to designer diseases for humans, plants, and animals.
 What was formerly only available at the cost of billions of dollars and years of research can now be achieved by a single individual at a nominal cost. The original human genome project took ten years, employed a large research team with state-of-the-art laboratories, and cost a billion dollars. Now, you can get your complete genome sequenced for about $10,000 in about six weeks. If you just want specific information, the cost is as little as $100.
What was formerly only available at the cost of billions of dollars and years of research can now be achieved by a single individual at a nominal cost. The original human genome project took ten years, employed a large research team with state-of-the-art laboratories, and cost a billion dollars. Now, you can get your complete genome sequenced for about $10,000 in about six weeks. If you just want specific information, the cost is as little as $100.
To the point, in 2017 Canadian researchers at the University of Alberta revived an extinct horsepox virus using synthetic DNA strands ordered for about $100,000. While not a trivial effort, the research lead Dr. David Evans admitted that he undertook the project to prove that it could be done. And to prove that it wouldn’t necessarily require a lot of time, money, and even biomedical skill or knowledge. His effort opened up new possibilities for researchers looking to make better vaccines, but also those looking to use these viruses as bioweapons9 including smallpox.10
 Questions
Questions
This causes a number of questions to spring to mind. What sort of enemy would use CRISPR to resurrect or design biological weapons against humans, animals, or crops? Can we prevent its use? How do we recover once it is used?
What sort of enemy would use CRISPR to resurrect or design biological weapons against humans, animals, or crops?
The sort of enemy who would employ CRISPR to design bioweapons fits one of three profiles, each of which has their own present day or historical example. The first is a nation state – the Democratic People’s Republic of Korea (DPRK). The second is an Aum Shinrikyo-like non-state actor. The third is a Unabomber-like super-empowered individual. The DPRK is a clear and present danger. The other two historical examples are not evident yet, but the potential for them to spring to life is there.
 The DPRK is extremely xenophobic. Their culture views North Koreans as the pinnacle of human development. All other cultures and races are, by definition inferior. In that sense, they are culturally akin to pre-World War II Japan or Germany. They are also materialists, in the sense that they ascribe a spiritual dimension to human affairs. With such underlying beliefs, the end justifies the means when dealing with inferiors.11 It doesn’t take much imagination to see that the DPRK would have no moral or ethical problems with creating an asymptomatic, race-specific, highly contagious and deadly disease.
The DPRK is extremely xenophobic. Their culture views North Koreans as the pinnacle of human development. All other cultures and races are, by definition inferior. In that sense, they are culturally akin to pre-World War II Japan or Germany. They are also materialists, in the sense that they ascribe a spiritual dimension to human affairs. With such underlying beliefs, the end justifies the means when dealing with inferiors.11 It doesn’t take much imagination to see that the DPRK would have no moral or ethical problems with creating an asymptomatic, race-specific, highly contagious and deadly disease.

The emergence of an Aum Shinrikyo-like organization in the near future is not beyond the realm of the possible. The original organization employed Sarin in the Tokyo subway in 1995 but it also conducted extensive research and testing into bioweapons to include anthrax, botulinum toxin, and the Ebola virus in 1992 – 1995.12 This was possible because the Aum had recruited a number of highly capable scientists. At its inception, Aum had been indistinguishable from a number of contemporary – and harmless – cults in Asia. However, it morphed into a violent doomsday cult without the Japanese authorities detecting the change. While such a failure in 1995 led to a few dozen deaths, the increasing availability of CRISPR technology could make such a failure a catastrophic event.
The final threat – the super-empowered individual – may not emerge until the latter part of the timeframe covered by this paper. Theoretically, enabled by AI and quantum computing, it will be possible to create a bioweapon that would target only specific genomic types. It is not beyond the realm of probability to envision a hate-filled racist developing and using such a highly specific bioweapon.
Can we prevent its use?
Jennifer Doudna, a University of California biochemist who helped invent CRISPR technology in 2012, calls for the “appropriate regulation” of human germline editing in her recent editorial entitled CRISPR’s unwanted anniversary in the journal Science: “Consequences for defying established restrictions should include, at a minimum, loss of funding and publication privileges. Ensuring responsible use of genome editing will enable CRISPR technology to improve the well-being of millions of people and fulfill its revolutionary potential.”
However, prevention is highly problematic when a technology is cheap, widely available, and relatively easy to use. CRISPR meets both of the first two criteria. Although inexpensive CRISPR kits are available online, the knowledge necessary to employ to create malignant products resides at the PhD level. In all probability, it would require a team of PhDs to produce a bioweapon. However, if current trends of open-source knowledge dissemination13 continue, the knowledge threshold for employment may lower significantly. The future may require the power of AI, data science, big data, and quantum computers to identify and track potential threats.
Cuiker and Mayer-Schoenberg observe that, “Using big data will sometimes mean forgoing the quest for why in return for knowing what.”14 In other words, it involves a shift from understanding causation to seeking a correlation derived from big data to provide a proxy for what you are trying to understand. A correlation is simply a relationship between two data values. As such, it can serve to focus attention on a previously unsuspected connection and lead to discovery of causation. It can also provide warning when the strength of a correlation reaches a predetermined level requiring executive attention.
 To illustrate, in 2009 the Center for Disease Control (CDC) approached Google with a problem on catching flu outbreaks as early as possible. The new H1N1 strain had been identified and CDC was concerned the outbreak might be as severe as that of the 1918 Spanish Influenza. As things stood, CDC only received warning of a flu outbreak an average of one to two weeks after its onset. The reason was simple – the data the CDC used to determine an outbreak were hospital admissions and emergency room data. Although they understood flu had broken out, they were in a constant catchup mode – not the desired mode for a possible H1N1 pandemic.
To illustrate, in 2009 the Center for Disease Control (CDC) approached Google with a problem on catching flu outbreaks as early as possible. The new H1N1 strain had been identified and CDC was concerned the outbreak might be as severe as that of the 1918 Spanish Influenza. As things stood, CDC only received warning of a flu outbreak an average of one to two weeks after its onset. The reason was simple – the data the CDC used to determine an outbreak were hospital admissions and emergency room data. Although they understood flu had broken out, they were in a constant catchup mode – not the desired mode for a possible H1N1 pandemic.
Google agreed to try to solve the puzzle. They used the “n = all” approach, querying their entire search database for the last (2007-2008) flu outbreak. Google ran over 50 million search terms through 450 million algorithms before arriving at a list of 45 search terms that – if entered with a certain frequency in any geographic area – strongly correlated with a flu outbreak. Using this approach, Google was able to detect warning signs within one or two days of an outbreak, pinpoint the geographic area, and even estimate the percentage of the population affected. They deployed this capability in time to assist the CDC in coping with the 2009 H1N1 outbreak.15,16
How do we recover once it is used?
While these three threats are possible, their solution will arise from the same technological forces that created them. Some components of the solution – like a robust public health system – are already in place in the U.S. The future public health system will rapidly identify the bioweapon and begin to develop treatments. The government will enforce such measures as social distance, allowing virulent strains to ‘burn out.’ In the future, the scientific community will use AI and quantum computing to run simulations that come up with novel approaches to mitigating the effects of any bioweapon. CRISPR and Nanotechnology will allow for the employment of payloads that counter the bioweapon. It will still be a classic game of move and countermove.
Conclusion.
The advent of easily accessible CRISPR technology poses a real and present danger to the world. In the hands of a rogue nation, a terrorist organization, or a super-empowered individual, it could unleash old diseases such as smallpox or new diseases with no known treatment. With the right knowledge, the entry threshold is less than a quarter or a million dollars. We must possess the means to identify, track, and counter these threats – preferably before they are employed at scale.
If you enjoyed this post, please also see:
-
- Mr. Simkin‘s previous posts, Sine Pari and Keeping the Edge.
- Zachary Kallenborn‘s post, A New Age of Terror: The Future of CBRN Terrorism
- Mr. Joseph DeFranco and Dr. James Giordano‘s post, Designer Genes: Made in China?
- LtCol Jennifer Snow, Dr. Giordano, and Mr. DeFranco‘s post, Dead Deer, and Mad Cows, and Humans (?) … Oh My!
- The Wide Range of Competition
- Mad Scientist Bio Convergence and Soldier 2050 Conference Final Report.
Howard R. Simkin is a Senior Concept Developer in the DCS, G-9 Concepts, Experimentation and Analysis Directorate, U.S. Army Special Operations Command. He has over 40 years of combined military, law enforcement, defense contractor, and government experience. He is a retired Special Forces officer with a wide variety of special operations experience. Within the G9 he analyzes and defines the future operating environment and required capabilities Army Special Operations Forces (ARSOF) in support of future concepts development. His subject matter expertise includes analyzing and evaluating historical, current and emerging technology as well as Combined, Joint, Multi-Service, Army and ARSOF organizational initiatives, trends, and concepts to determine the implications for ARSOF units. Mr. Simkin holds a Masters of Administrative Science from the Johns Hopkins University. He is a proclaimed TRADOC Mad Scientist as well as a certified Project Management Professional. He has written several articles that have recently been published in Naval History, Small Wars Journal, or on the TRADOC Mad Scientist Blog.
Disclaimer: The views expressed in this blog post are those of the author, and do not necessarily reflect those of the Department of Defense, Department of the Army, U.S. Army Special Operations Command (USASOC), Army Futures Command (AFC), or Training and Doctrine Command (TRADOC).
1 https://en.wikiquote.org/wiki/William_Gibson (Accessed 18 April 2017).
2 CRISPR is a gene editing technique. CRISPR stands for clustered regularly-interspaced short palindromic repeats; it is DNA used in the immune systems of prokaryotes. The system relies on the Cas9 enzyme and guide RNA’s to find specific, problematic segments of a gene and cut them out. In 2015, researchers discovered that this technique could be applied to humans.
3 Aum Shinrikyo was an apocalyptic Japanese cult that carried out a Sarin gas attack in the Tokyo Subway on 20 March 1995. See Kaplan, David E., and Andrew Marshall. The Cult at the End of the World: The Terrifying Story of the Aum Doomsday Cult, from the Subways of Tokyo to the Nuclear Arsenals of Russia. New York: Crown Publishers, Inc., 1996.
4 Theodore “Ted” Kaczynski was the Unabomber. He carried out a series of bombings from 1978 to 1995 to protest the growing influence of technology in society. See https://en.wikipedia.org/wiki/Ted_Kaczynski (Accessed 06 October 2017).
5 The FOE depicted in this paper is a synthesis of the National Intelligence Council Global Trends (2035) Paradox of Progress, National Intelligence Council, Washington DC, January 2017, see: https://www.dni.gov/index.php/global-trends-home, and the Chairman, Joint Chief of Staff, Joint Operating Environment 2035, The Joint Force in a Contested and Disordered World, Joint Staff J7, Washington, DC, 14 July 2016.
6 Taken from a PowerPoint presentation entitled “AI Futures” given by fellow Proclaimed Mad Scientist Dr. James Canton at the USASOC Futures Forum, 8 August 2017.
7 11 Incredible Things CRISPR Has Helped Us Achieve in 2017 https://futurism.com/11-incredible-things-crispr-has-helped-us-achieve-in-2017/ (Accessed 06 October 2017).
8 CRISPR Is Rapidly Ushering in a New Era in Science. https://futurism.com/crispr-is-rapidly-ushering-in-a-new-era-in-science/ (Accessed 16 August 2017)
9 Researchers Brought Back a Pox Virus Using Mail-Order DNA and it Only Cost $100,000. https://futurism.com/researchers-brought-back-a-pox-virus-using-mail-order-dna-and-it-only-cost-100000/ (Accessed 10 October 2017).
10 People Could Make Smallpox from Scratch in a Lab, Scientists Warn. https://www.livescience.com/59809-horsepox-virus-recreated.html (Accessed 10 October 2017), and Scientists synthesize smallpox cousin in ominous breakthrough. https://www.washingtonpost.com/news/speaking-of-science/wp/2017/07/07/scientists-synthesize-smallpox-cousin-in-ominous-breakthrough/?utm_term=.2c1b343dd4ec (Accessed 10 October 2017).
11 USSOCOM JISOC, Irregular Threat Analysis Branch, Socio — Cultural Awareness Section. North Korea Population Engagement Study (Unclassified). Tampa, FL: United States Special Operations Command, 2013, 15 – 16.
12 Kaplan, David E., and Andrew Marshall. The Cult at the End of the World: The Terrifying Story of the Aum Doomsday Cult, from the Subways of Tokyo to the Nuclear Arsenals of Russia. New York: Crown Publishers, Inc., 1996, 51 – 57; 96 – 7; 94 – 6.
13 The Canadian researchers mentioned earlier in this paper published an open source paper which details how they resurrected horsepox.
14 Cuiker, Kenneth and Mayer-Schoenberger, Viktor, “The Rise of Big Data: How it’s Changing the Way We Think About The World,” Foreign Affairs 92, no. 3 (May/June 2013): p. 36.
15 Cuiker, Kenneth and Mayer-Schoenberger, Viktor, “The Rise of Big Data: How it’s Changing the Way We Think About The World,” Foreign Affairs 92, no. 3 (May/June 2013): p. 29.
16 Mayer Schoenberger, Viktor and Cukier, Kenneth: Big Data, A Revolution That Will Transform How We Live, Work, And Think. Boston, New York: Mariner Books, Houghton Mifflin Harcourt, 2014, pp. 1-3. Twitter was also used to mine “flu”, and correlate results on a map. This allowed CDC to watch flu bloom on a map in near real time.
References
Cuiker, Kenneth, and Victor Mayer-Schoenberg. “The Rise of Big Data: How it’s Changing the Way We Think About The World.” Foreign Affairs 92, no. 3, May/June 2013.
Department of Defense. DOD Dictionary of Military and Associated Terms. Washington, DC: The Joint Staff, J7, As of March 2017.
Futurism.com. CRISPR Is Rapidly Ushering in a New Era in Science. March 13, 2017. https://futurism.com/crispr-is-rapidly-ushering-in-a-new-era-in-science/ (accessed July 2017, 2017).
Kaplan, David E., and Andrew Marshall. The Cult at the End of the World: The Terrifying Story of the Aum Doomsday Cult, from the Subways of Tokyo to the Nuclear Arsenals of Russia. New York: Crown Publishers, Inc., 1996.
Mayer-Schoenberg, Victor, and Kenneth Cuiker. Big Data, A Revolution That Will Transform How We Live, Work, And Think. Boston, New York: Mariner Books, Houghton Mifflin Harcourt, 2014.
National Intelligence Council. Global Trends, Paradox of Progress. Washington, DC: National Intelligence Council, January 2017.
The Joint Staff. Joint Operating Environment 2035, The Joint Force in a Contested and Disordered World. Washington, DC: Joint Staff J7, 14 July 2016.
USSOCOM JISOC, Irregular Threat Analysis Branch, Socio — Cultural Awareness Section. North Korea Population Engagement Study (Unclassified). Tampa, FL: United States Special Operations Command, 2013.




 Synthetic biology offers improved access to biological weapons agents, especially to otherwise highly controlled agents. Synthetic biology can be used to create new or modify existing organisms.
Synthetic biology offers improved access to biological weapons agents, especially to otherwise highly controlled agents. Synthetic biology can be used to create new or modify existing organisms. Drones also make CBRN agent delivery easier. Drones offer terrorists access to the air. Terrorists can use them to fly over physical barriers, such as fencing or walls to carry out an attack. Drones also give terrorists more control over where they launch an attack: they can choose a well-defended position or one proximate to an escape route. Although small drone payload sizes limit the amount of agent that can be delivered, terrorists can acquire multiple drones.
Drones also make CBRN agent delivery easier. Drones offer terrorists access to the air. Terrorists can use them to fly over physical barriers, such as fencing or walls to carry out an attack. Drones also give terrorists more control over where they launch an attack: they can choose a well-defended position or one proximate to an escape route. Although small drone payload sizes limit the amount of agent that can be delivered, terrorists can acquire multiple drones. If CBRN terrorism is becoming easier, U.S. forces can be expected to be at greater risk of CBRN attack and face more frequent attacks. An attack with infectious biological weapons from afar would not likely be discovered until well after the attack took place. Although still quite unlikely, a major biological attack could cause massive harm. Timed correctly, a CBRN terror attack could delay deployment of troops to a combat zone, inhibit launch of close-air support assets, or harm morale by delaying delivery of delicious pizza MREs.
If CBRN terrorism is becoming easier, U.S. forces can be expected to be at greater risk of CBRN attack and face more frequent attacks. An attack with infectious biological weapons from afar would not likely be discovered until well after the attack took place. Although still quite unlikely, a major biological attack could cause massive harm. Timed correctly, a CBRN terror attack could delay deployment of troops to a combat zone, inhibit launch of close-air support assets, or harm morale by delaying delivery of delicious pizza MREs.