[Editor’s Note: The Army’s Mad Scientist Laboratory is pleased to feature the next in a series of posts excerpting findings from Team Axis Insight 2035‘s Project Deterrence Final Report. This Integrated Research Project documents the findings from the group’s United States Army War College (USAWC) Strategic Research Requirement portion of the Master of Strategic Studies degree program that occurred over the academic year (from November 2024 to April 2025).
 Team Axis Insight 2035 consisted of COL Byron N. Cadiz, COL T. Marc Skinner, LTC Robert W. Mayhue, LTC Lori L. Perkins, and LTC Shun Y. Yu — all U.S. Army Officers and now proclaimed Army Mad Scientists! Team Axis Insight 2035‘s Project Deterrence Final Report documents their collective response to the following question posed by Ian Sullivan, Deputy Chief of Staff, G-2, U.S. Army Training and Doctrine Command:
Team Axis Insight 2035 consisted of COL Byron N. Cadiz, COL T. Marc Skinner, LTC Robert W. Mayhue, LTC Lori L. Perkins, and LTC Shun Y. Yu — all U.S. Army Officers and now proclaimed Army Mad Scientists! Team Axis Insight 2035‘s Project Deterrence Final Report documents their collective response to the following question posed by Ian Sullivan, Deputy Chief of Staff, G-2, U.S. Army Training and Doctrine Command:
How are China, Russia, Iran, and North Korea likely to respond to U.S.-led deterrence efforts by 2035?
To date, the Mad Scientist Laboratory has excerpted Team Axis Insight 2035‘s findings regarding “an entangled future of situational cooperation and transactional inter-dependence among China, Russia, Iran, and North Korea” in Project Deterrence — An Entangled Future; and how our adversaries are likely to integrate “four future capabilities … to create an environment where U.S. deterrence is neutralized: quantum warfare, swarm supremacy, hypersonic strike, and metamaterials” in Project Deterrence – Disruptive Technologies.
In today’s post, we excerpt Team Axis Insight 2035‘s finding exploring how our adversaries are employing gray zone activities to “saturate the competition continuum below the level of armed conflict” — what proclaimed Mad Scientist Dr. David Kilcullen described as liminal warfare — to achieve a state of persistent coercion. These efforts “are innovating in the seams between peace and war,”  seeking to “challenge U.S. strategic posture and alliance cohesion.” China, our pacing threat, is proving especially adept at tweaking the reins of persistent coercion to, in the words of Sun Tzu, “subdue the enemy without fighting” — Read on!]
seeking to “challenge U.S. strategic posture and alliance cohesion.” China, our pacing threat, is proving especially adept at tweaking the reins of persistent coercion to, in the words of Sun Tzu, “subdue the enemy without fighting” — Read on!]
Threat Vector #3: Persistent Coercion
By 2035, China, Russia, Iran, and North Korea are highly likely* to intensify their strategic use of persistent coercion tactics to expand geopolitical influence and undermine U.S. and allied interests globally. This will create time and space to pursue their national interests. Examples of persistent coercion tactics include lawfare, international peacekeeping missions, Digital Silk Road initiatives, or attacks to critical infrastructure. These tactics saturate the competition continuum below the level of  armed conflict and cross multiple time horizons, with intended effects both immediately and into the indefinite future. Regardless of the form it takes, persistent coercion challenges U.S.
armed conflict and cross multiple time horizons, with intended effects both immediately and into the indefinite future. Regardless of the form it takes, persistent coercion challenges U.S.
strategic posture and alliance cohesion.
Expansion of Persistent Coercion Activities
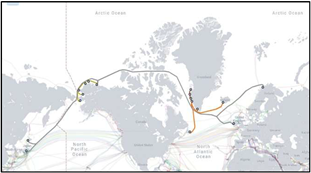
China is rapidly enhancing its capabilities within the gray zone. This activity is increasingly prominent in sensitive areas such as the Arctic, where critical U.S. infrastructure, including undersea communications cables, remains vulnerable (see figures to the right and below). Employing military-civil fusion strategies, China and Russia use commercial maritime assets and infrastructure projects as covert sabotage platforms, exploiting plausible deniability and complicating attribution. By subtly disrupting critical networks, adversaries impose
asymmetric costs and test Western response thresholds, identifying vulnerabilities without provoking direct military retaliation.

Employment of Lawfare and Information Dominance
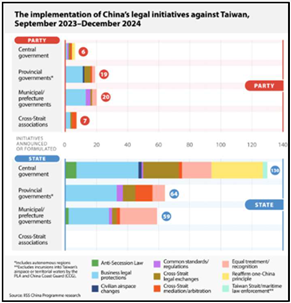
China will highly likely* leverage lawfare through the weaponized use of international law to legitimize geopolitical claims and reshape global norms, often in coordination with Russia. Promoting alternative interpretations of sovereignty and territorial rights, notably regarding the South China Sea and Taiwan, China neutralizes Western diplomatic efforts (see figure to the left). Concurrently, sophisticated disinformation campaigns via mainstream and social media undermine U.S. and allied credibility, positioning China as a responsible international actor. These narrative controls effectively erode Western diplomatic influence, gradually shifting international perceptions and norms in China’s favor, particularly in the absence of a cohesive U.S.-led counter-lawfare response.
Deployment of Military Forces
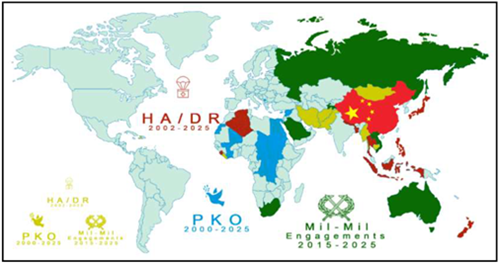
China will highly likely* use United Nations peacekeeping operations to expand its military and diplomatic influence worldwide. China contributes the most troops of all five countries on the United Nations’ Security Council (see figure below). These missions align with China’s broader Belt and Road Initiative, safeguarding economic interests abroad while embedding Chinese military forces under the mantle of international legitimacy. China also uses Humanitarian Assistance and Disaster Response missions and foreign military engagements to further leverage its military in pursuit of its diplomatic and economic goals. Collectively, these deployments facilitate the development of logistical and force-projection capabilities beyond traditional Chinese influence zones, diminishing U.S. soft power and diplomatic leverage, particularly in Africa and Southeast Asia. This visible presence enhances China’s global reputation as a responsible stakeholder, creating opportunities for increased political influence and economic integration, thereby challenging U.S. global leadership and strategic interests.
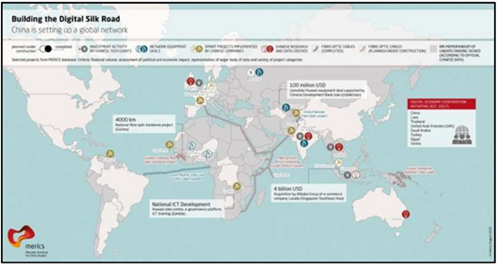
Pivot to Digital Silk Road
Due to demographic pressures such as an aging population and shrinking workforce, China will likely* shift focus from large-scale global infrastructure projects under the Belt and Road Initiative to regional digital infrastructure development via the Digital Silk Road (see figure below). Prioritizing investments in 5G networks, artificial intelligence, and green energy predominantly in southeast and central Asia, China seeks to consolidate regional influence. This shift enables China to embed its technologies deeply within partner nations’ digital ecosystems, fostering technological dependencies and influencing global digital standards. By controlling technological standards and protocols, China is almost certain* to assert long-term geopolitical influence through increased participation and leadership in international standard-setting organizations.
Infrastructure Attacks
It is highly likely* that by 2035 China, Russia, Iran, or North Korea will attempt to leverage attacks against U.S. critical infrastructure to slow or paralyze its response capabilities prior to or during a conflict scenario. Due to the increasing development and integration of counterspace capabilities, cyber warfare tactics, and the demonstrated willingness to target critical infrastructure, potential adversaries have the capability to hold U.S. critical infrastructure at risk (see figure below). Despite the risks of escalation and international condemnation associated with such actions, the perceived strategic benefits of gaining a temporary advantage by disrupting U.S. power projection and decision-making processes will likely* incentivize these nations to employ such tactics.

All roads go through China. Taken together, these findings point to a comprehensive Chinese strategy to reshape the global order by 2035 through non-kinetic, legal, technological, and persistent coercion operations. China is creating the conditions to win future conflicts before they begin, blinding, dividing, and weakening the United States and its allies through persistent, low-threshold actions. While the U.S. retains conventional military dominance now, our adversaries are innovating in the seams between peace and war seeking technological overmatch in the very near future.
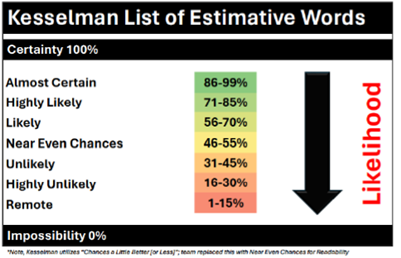
* Kesselman List of Estimative Words:
If you enjoyed this post, check out Axis Insight 2035‘s comprehensive Project Deterrence Final Report here.
Review the TRADOC Pamphlet 525-92, The Operational Environment 2024-2034: Large-Scale Combat Operations
Explore the TRADOC G-2‘s Operational Environment Enterprise web page, brimming with authoritative information on the Operational Environment and how our adversaries fight, including:
Our China Landing Zone, full of information regarding our pacing challenge, including ATP 7-100.3, Chinese Tactics, How China Fights in Large-Scale Combat Operations, BiteSize China weekly topics, and the People’s Liberation Army Ground Forces Quick Reference Guide.
Our Russia Landing Zone, including the BiteSize Russia weekly topics. If you have a CAC, you’ll be especially interested in reviewing our weekly RUS-UKR Conflict Running Estimates and associated Narratives, capturing what we learned about the contemporary Russian way of war in Ukraine over the past two years and the ramifications for U.S. Army modernization across DOTMLPF-P.
Our Iran Landing Zone, including the Iran Quick Reference Guide and the Iran Passive Defense Manual (both require a CAC to access).
Our North Korea Landing Zone, including Resources for Studying North Korea, Instruments of Chinese Military Influence in North Korea, and Instruments of Russian Military Influence in North Korea.
Our Irregular Threats Landing Zone, including TC 7-100.3, Irregular Opposing Forces, and ATP 3-37.2, Antiterrorism (requires a CAC to access).
Our Running Estimates SharePoint site (also requires a CAC to access) — documenting what we’re learning about the evolving OE. Contains our monthly OE Running Estimates, associated Narratives, and the quarterly OE Assessment TRADOC Intelligence Posts (TIPs).
Then read the following related Mad Scientist Laboratory content:
Fait Accompli: China’s Non-War Military Operations (NWMO) and Taiwan, by SGT Michael A. Cappelli II
Operation Northeast Monsoon: The Reunification of Taiwan, by Sherman Barto
Flash-Mob Warfare: Whispers in the Digital Sandstorm (Parts 1 and 2) and 50 Shades of JIFCO, by Dr. Robert E. Smith
China: Building Regional Hegemony and China 2049: The Flight of a Particle Board Dragon, the comprehensive report from which this post was excerpted
Competition and Conflict in the Next Decade
Disrupting the “Chinese Dream” – Eight Insights on how to win the Competition with China
Sub-threshold Maneuver and the Flanking of U.S. National Security, by Dr. Russell Glenn
Non-Kinetic War, Global Entanglement and Multi-Reality Warfare and associated podcast, with COL Stefan Banach (USA-Ret.)
Hybrid Threats and Liminal Warfare and associated podcast, with Dr. David Kilcullen
Weaponized Information: What We’ve Learned So Far…, Insights from the Mad Scientist Weaponized Information Series of Virtual Events, and all of this series’ associated content and videos [access via a non-DoD network]
Disclaimer: The views expressed in this blog post are those of the author, and do not necessarily reflect those of the Department of Defense, Department of the Army, Army Futures Command (AFC), or Training and Doctrine Command (TRADOC).



