[Editor’s Note: Regular readers will note that one of our enduring themes is the Internet’s emergence as a central disruptive innovation. With the publication of proclaimed Mad Scientist P.W. Singer and co-author Emerson T. Brooking’s LikeWar – The … Read the rest
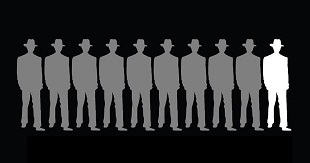
67. “The Tenth Man”
[Editor’s Note: In the movie World War Z (I know… the book was way better!), an Israeli security operative describes how Israel prepared for the coming zombie plague. Their strategy was if nine men agreed on an analysis or … Read the rest
61. Base in a Box
[Editor’s Note: Mad Scientist Laboratory is pleased to publish the following guest blog post by Mr. Lewis Jones. Originally a “Letter Home” submission to the Call for Ideas associated with the Mad Scientist Installations of the Future Conference… Read the rest
60. Mission Engineering and Prototype Warfare: Operationalizing Technology Faster to Stay Ahead of the Threat
[Editor’s Note: Mad Scientist is pleased to present the following post by a team of guest bloggers from The Strategic Cohort at the U.S. Army Tank Automotive Research, Development, and Engineering Center (TARDEC). Their post lays out a … Read the rest