[Editor’s Note: Mad Scientist Laboratory is pleased to publish today’s post by guest bloggers Colonel Montgomery Erfourth and Dr. Aaron Bazin, addressing prospective patterns of emerging technology used in the 2020-2027 timeframe by Violent Extremist Organizations (VEOs), as seen through the lens of the National Security Strategy and the Special Operations mission. This timely submission addresses the challenges and opportunities these technological advances will pose to both the Army’s General Purpose Forces and our Special Operations Forces (SOF) as they seek to protect and advance U.S. national interests abroad — Enjoy!]
“Transnational threat groups, from jihadist terrorists to transnational criminal organizations, are actively trying to harm Americans. While these challenges differ in nature and magnitude, they are fundamentally contests between those who value human dignity and freedom and those who oppress individuals and enforce uniformity.”
“To maintain our competitive advantage, the United States will prioritize emerging technologies critical to economic growth and security…”
U.S. National Security Strategy, 2017
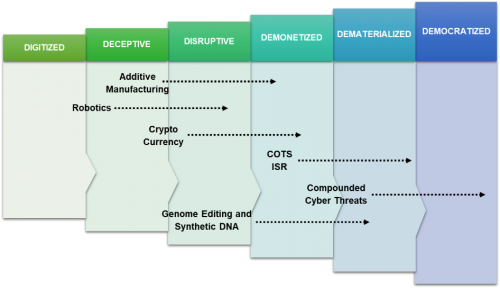
Global innovation, the ability to share information quickly, rapidly advancing technology, and distributed knowledge have created new opportunities for politically hostile groups. Lower barriers to employ new technologies offer super-empowered individuals and VEOs a range of tools across the physical, virtual, and cognitive environments to pursue their malign objectives.1 Arguably, technology is now advancing at such a velocity that a structured framework helps prioritize threats and resources. Diamandis and Kotler’s “Six Ds” of exponential technology is one such framework to determine the impact and pace of growth for potential technologies, based on how far the technology has progressed. They argue that technology progresses along the following consecutive phases:
-
- Digitized: Once people digitize a physical commodity or service (represented in ones and zeros), it embarks on the first step of the exponential growth curve. This type of digital information is easy to access, share, and distribute.
- Deceptive: During the next phase of growth, the technology does not appear to expand quickly or make an impact. This period is often deceptively slow due to the nature of exponential change.
- Disruptive: The technology becomes disruptive once it outperforms other technologies in effectiveness and cost.
- Demonetized: In this phase, the technology becomes cheaper, and in some cases free, further reducing barriers for its use by actors with limited resources.
- Dematerialized: When advancements in technologies significantly reduce the size of the physical element of the technology and/or it is absorbed into other products (e.g., maps, radio, camera in mobile phone), it is considered dematerialized.
- Democratized: In the final stage of the exponential growth curve, the digitization, reduced cost, and dematerialization of the technology’s original form result in the increasingly public access to the new technology 2
This paper uses the Six D’s to evaluate the threats of six emerging technologies that VEOs could use: additive manufacturing, cryptocurrency, genome editing and synthetic DNA, robotics, and Commercial off the Shelf Intelligence Surveillance and Reconnaissance (COTS ISR). This list does not represent a comprehensive account of all technologies that VEOs may leverage in the future. Instead, this list includes the top six technologies that either have reached the democratization stage or will reach it by 2027 and pose a threat to U.S. national interests.
Additive Manufacturing: Although scientists developed additive manufacturing or three dimensional (3D) printing in the 1980s, 3D printing reached the democratization phase in the 2010s.3 The internet allows the maker communities to create 3D designs through free software, share data and expertise through tutorial videos, and create 3D objects. Today, countless companies offer 3D printing services with a click of a button. The democratization of this technology is of particular interest to VEOs as it affords them the potential to create unconventional weapons at scale.4 SOF can anticipate that VEOs will leverage the accessibility of this technology to design and print unconventional fit-for-purpose weapons. Further, the next iteration of 3D printed weapons on the horizon is 3D printed explosives. While it is unlikely that this technology is yet in the hands of VEOs, they could gain this capability in the next seven years.5

Given these technological advancements, it is highly likely that VEOs will use additive manufacturing capabilities to 3D print weapons, design custom projectiles, and innovate with creative accessories. VEOs may seek to print 3D printed guns and share digital “weapon files” with likeminded individuals, bypassing arms control mechanisms and making attacks difficult to anticipate or prevent.
Cryptocurrency: A VEO’s ability to recruit, self-organize, conduct attacks, and develop capabilities relies on funding. The secure blockchain platforms upon which cryptocurrencies operate have made illicit finance more difficult to track, stop, and prevent. At present, extremist organizations use cryptocurrencies to receive, manage, transfer, and spend money. Cryptocurrencies are transitioning from the deceptive phase of growth to the disruptive phase; as they gain traction  in the mainstream, their use will also become more pervasive amongst VEOs.6 Given the above, it is highly likely that VEOs will continue to leverage the anonymity of cryptocurrency to fund raise, launder money, and pay for goods and services while bypassing the regulated international financial system. This will allow VEOs the financial freedom of movement they require to operate in the shadows.
in the mainstream, their use will also become more pervasive amongst VEOs.6 Given the above, it is highly likely that VEOs will continue to leverage the anonymity of cryptocurrency to fund raise, launder money, and pay for goods and services while bypassing the regulated international financial system. This will allow VEOs the financial freedom of movement they require to operate in the shadows.
Genome Editing and Synthetic DNA: In the future, VEOs may continue to seek biological weapons and viruses as a means to attack the homeland.7 Advancements in genome editing and synthetic DNA (e.g., synthetic viruses that can infect large populations, agro-terrorism that can irreversibly destroy crops, and gene-drive editing which perpetually alters the evolution of the organism edited with unpredictable effects8) have increased the potential threat of these types of weapons. While specialists in the genomics field are demonetizing and dematerializing this technology through inexpensive kits and DNA editing  software, such as Clustered Regularly Interspaced Short Palindromic Repeats (CRISPR), its use still requires a high level of expertise.9 Considering these factors, it is very likely that VEOs will seek to acquire synthetic biology capabilities for malicious use. However, their ability to do so within the next seven years will be limited by the high technical skill needed to use the technology and weaponize it effectively. There is a low probability (but high risk) that a VEO could recruit an expert in this field who could overcome these challenges.
software, such as Clustered Regularly Interspaced Short Palindromic Repeats (CRISPR), its use still requires a high level of expertise.9 Considering these factors, it is very likely that VEOs will seek to acquire synthetic biology capabilities for malicious use. However, their ability to do so within the next seven years will be limited by the high technical skill needed to use the technology and weaponize it effectively. There is a low probability (but high risk) that a VEO could recruit an expert in this field who could overcome these challenges.
Robotics: VEOs are adept at employing Unmanned Aerial Vehicles (UAV), or “drones,” on the battlefield. Initially, VEOs used Commercial-Off-The-Shelf (COTS) drones for reconnaissance and surveillance, later attaching explosive devices to deliver lethal effects. Currently, VEOs use them as a management tool to enable drone pilots to coordinate and assign vehicles to locations to commit coordinated suicide attacks. The VEOs then leverage the video  footage of these attacks for propaganda purposes.10 Looking ahead, the character of conflict may change as VEOs develop ways to embed chemical, biological, radioactive, or nuclear (CBRN) substances into drone payloads. In the coming years, as VEOs gain access to Unmanned Underwater Vehicles (UUV), they could explore their use to strike vulnerable U.S. maritime targets.11 Given these advances, it is highly likely that VEOs will continue to experiment with UAVs for surveillance and kinetic force application purposes in the operating environment. They may attempt to use swarms of drones to create confusion in the battlefield, allowing them windows of advantage to conduct follow-on attacks. It is very likely that if VEOs could obtain CBRN material, they would use drones as a delivery vehicle. This scenario is low probability but high risk. While initially VEOs may use UAVs for surveillance or trafficking goods, they could eventually progress to offensive attacks on friendly targets.
footage of these attacks for propaganda purposes.10 Looking ahead, the character of conflict may change as VEOs develop ways to embed chemical, biological, radioactive, or nuclear (CBRN) substances into drone payloads. In the coming years, as VEOs gain access to Unmanned Underwater Vehicles (UUV), they could explore their use to strike vulnerable U.S. maritime targets.11 Given these advances, it is highly likely that VEOs will continue to experiment with UAVs for surveillance and kinetic force application purposes in the operating environment. They may attempt to use swarms of drones to create confusion in the battlefield, allowing them windows of advantage to conduct follow-on attacks. It is very likely that if VEOs could obtain CBRN material, they would use drones as a delivery vehicle. This scenario is low probability but high risk. While initially VEOs may use UAVs for surveillance or trafficking goods, they could eventually progress to offensive attacks on friendly targets.
COTS ISR: Advances in artificial intelligence (AI) and the ubiquity of video surveillance have given rise to gait recognition technology.12 Some systems “can identify people from up to 50 meters (165 feet) away, even with their back turned or face covered.”13 As the network of the Internet of Things (IoT) becomes more pervasive in public and private spaces, passive  reconnaissance of movement will become more accessible. Researchers have developed a silent reconnaissance technology that uses radio frequency (RF) signals emitted by Wi-Fi devices to monitor individuals passively inside rooms and buildings.14 This technology is publicly available and people may soon democratize it.15 Considering the above, it is highly likely that VEOs may seek to leverage COTS ISR-related technology. An increasingly digitally connected world with sensors gathering sound, video, and signals will challenge SOF operators.
reconnaissance of movement will become more accessible. Researchers have developed a silent reconnaissance technology that uses radio frequency (RF) signals emitted by Wi-Fi devices to monitor individuals passively inside rooms and buildings.14 This technology is publicly available and people may soon democratize it.15 Considering the above, it is highly likely that VEOs may seek to leverage COTS ISR-related technology. An increasingly digitally connected world with sensors gathering sound, video, and signals will challenge SOF operators.
Compounded Cyber Threats: IoT, AI, and DeepFakes: In the future, one can expect that VEOs will seek to combine multiple cyber capabilities into further misleading or false narratives, targeting the U.S. and partner populations by creating content with DeepFake, IoT, and AI capabilities, and  amplifying their messaging with social media. Friendly use of these capabilities has contributed to the development of smart infrastructure across industries (energy, agriculture, finance, health, transportation, etc.), the commercial reliance on digital infrastructure, and the digitization of homes with IoT. Together, these trends result in a growing number of digital and physical assets that VEOs can attack remotely. AI has already begun to change the character of these cyber threats.16 As these technologies evolve, they will become more accessible. Arguably, VEOs may seek to use them to automate, accelerate, and further spread their cyber offensive actions.
amplifying their messaging with social media. Friendly use of these capabilities has contributed to the development of smart infrastructure across industries (energy, agriculture, finance, health, transportation, etc.), the commercial reliance on digital infrastructure, and the digitization of homes with IoT. Together, these trends result in a growing number of digital and physical assets that VEOs can attack remotely. AI has already begun to change the character of these cyber threats.16 As these technologies evolve, they will become more accessible. Arguably, VEOs may seek to use them to automate, accelerate, and further spread their cyber offensive actions.
With this in mind, it is highly likely that VEOs will seek to use DeepFakes, AI, and the IoT as a cognitive attack vector to sow doubt and confusion among their adversaries to advance their interests and narratives. If SOF lacks the capability to track and address these technologies, it may affect overall mission success.
If you enjoyed this blog post, check out the entire article posted on the Mad Scientist All Partners Access Network (APAN) page to see Colonel Erfouth‘s and Dr. Bazin‘s recommendations to the SOF Enterprise on how to mitigate the challenges that VEOs may present as they seek the innovation advantage on the battlefield of the future…
… and also read the following related blog posts:
Weaponized Information: One Possible Vignette and The Information Environment: Competition and Conflict Mad Scientist Anthology
Dead Deer, and Mad Cows, and Humans (?) … Oh My! by proclaimed Mad Scientists LtCol Jennifer Snow and Dr. James Giordano, and Joseph DeFranco
CRISPR Convergence by Howard R. Simkin
A New Age of Terror: New Mass Casualty Terrorism Threats and A New Age of Terror: The Future of CBRN Terrorism by Zachary Kallenborn
Colonel Montgomery Erfourth is currently the Integration Division Chief with the J5 at U.S. Special Operations Command in Tampa, Florida. He has over 25 years of professional military and civilian experience in the areas of leadership, planning, strategy, research, transportation, supply chain management, marketing, budget, and financial management. Monte has worked closely with U.S. Ambassadors, highest level of military leadership, and policy makers and performed duties in over 25 countries, several of which were in non-permissive environments.
Dr. Aaron Bazin adds value to organizations by helping them explore the possibilities of the future and develop unique, visionary strategies. He is a skilled researcher, facilitator, presenter, and writer. Aaron is currently the Managing Director of the Donovan Strategy and Innovation Group, U.S. Special Operations Command in Tampa, Florida. His team acts as catalyst for change and innovation across the Joint SOF enterprise to improve its ability to further national interests globally.
Disclaimer: The views expressed in this blog post are solely those of the authors and do not necessarily reflect those of the Department of Defense, U.S. Special Operations Command, Department of the Army, Army Futures Command, or the Training and Doctrine Command.
1 Adam Elkus, A. and Burke, C., (2010), WikiLeaks, Media, and Policy: A Question of Super- Empowerment, Retrieved from: https://smallwarsjournal.com/blog/journal/docs-temp/558-elkus.pdf
2 The 6 Ds of Exponential Growth, from the book Bold by Peter Diamandis and Steven Kotler. https://singularityhub.com/2017/12/29/what-are-the-6-ds-of-exponential-organizations/
3 3D Printing Industry (2019). History of 3D Printing. https://3dprintingindustry.com/3d- printing-basics-free-beginners-guide#02-history
4 Dearden, L. (2019). Use of 3D printed guns in German synagogue shooting must act as warning to security services, experts say. Independent UK. https://www.independent.co.uk/news/world/europe/3d-gun-print-germany-synagogue-shooting-stephan-balliet-neo-nazi-a9152746.html
5 Los Alamos National Laboratory (2016). Explosiv3Design. https://www.lanl.gov/discover/publications/1663/2016-march/explosive-3d-design.php
6 Schoeberl, Richard. (2018). Gene Drives – An Emerging Terrorist Threat. Domestic Preparedness. https://www.domesticpreparedness.com/preparedness/gene-drives-an-emerging-terrorist-threat/
7 Memri (2018). Pro-ISIS Media Outlet Circulates Video Calling for Biological Attacks in the West. Middle East Media Research Institute TV Monitor Project.
8 Schoeberl, Richard. (2018). Gene Drives – An Emerging Terrorist Threat. Domestic Preparedness. https://www.domesticpreparedness.com/preparedness/gene-drives-an-emerging-terrorist-threat/
9 Sneed, Annie. (2017). Mail-Order CRISPR Kits Allow Absolutely Anyone to Hack DNA. Scientific American. https://www.scientificamerican.com/article/mail-order-crispr-kits-allow-absolutely-anyone-to-hack-dna/
10 Balkan, Serkan. (2017). DAESH’s Drone Strategy: Technology and the Rise of Innovative Terrorism. SETA. https://www.setav.org/en/daeshs-drone-strategy-technology-and-the-rise-of-innovative-terrorism/
11 Suguna, VS. Rahman, Faizal. (2018). Aquatic drone terror attacks a growing possibility. Today Online. https://www.todayonline.com/commentary/aquatic-drone-terror-attacks-growing-possibility
12 Giles, Jim. (2012). Cameras know you by your walk. New Scientist. https://www.newscientist.com/article/mg21528835-600-cameras-know-you-by-your-walk/
13 Kang, Dake. (2018). Chinese ‘gait recognition’ tech IDs people by how they walk. AP News. https://www.apnews.com/bf75dd1c26c947b7826d270a16e2658a
14 Yanzi Zhu, Zhujun Xiao, Yuxin Chen, Zhijing Li, Max Liu, Ben Y. Zhao, Haitao Zheng. (2019). Et Tu Alexa? When Commodity WiFi Devices Turn into Adversarial Motion Sensors. https://arxiv.org/pdf/1810.10109.pdf
15 Vincent, James. (2019). New AI deepfake app creates nude images of women in seconds. The Verge. https://www.theverge.com/2019/6/27/18760896/deepfake-nude-ai-app-women-deepnude-non-consensual-pornography
16 Warner, Bernhard. (2019). Artificial Intelligence Is About to Make Ransomware Hack Attacks Even Scarier. Fortune. https://fortune.com/2019/06/21/ai-ransomeware-hack-attacks/



