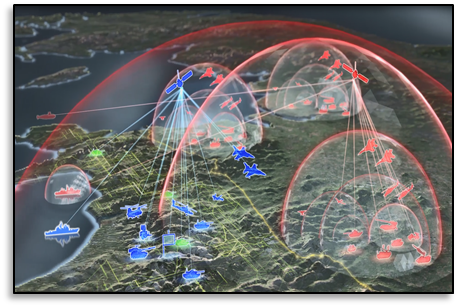
[Editor’s Note: Mad Scientist Laboratory is pleased to excerpt today’s post from Dr. James Mancillas‘ paper entitled Integrating Artificial Intelligence into Military Operations: A Boyd Cycle Framework (a link to this complete paper may be found at the … Read the rest
131. Omega
[Editor’s Note: Story Telling is a powerful tool that allows us to envision how innovative and potentially disruptive technologies could be employed and operationalized in the Future Operational Environment. In today’s guest blog post, proclaimed Mad Scientist Mr. August … Read the rest
86. Alternet: What Happens When the Internet is No Longer Trusted?
[Editor’s Note: Mad Scientist Laboratory is pleased to present a post by Mad Scientist and guest blogger Lt Col Jennifer “JJ” Snow, addressing the emergence of a post-internet world.]
“The Internet of the 1990s was about choosing your own … Read the rest
80. “The Queue”
[Editor’s Note: Mad Scientist Laboratory is pleased to present our August edition of “The Queue” – a monthly post listing the most compelling articles, books, podcasts, videos, and/or movies that the U.S. Army’s Training and Doctrine Command (TRADOC) Mad … Read the rest
79. Character vs. Nature of Warfare: What We Can Learn (Again) from Clausewitz
[Editor’s Note: Mad Scientist Laboratory is pleased to present the following post by guest blogger LTC Rob Taber, U.S. Army Training and Doctrine Command (TRADOC) G-2 Futures Directorate, clarifying the often confused character and nature of warfare, and … Read the rest