[Editor’s Note: Recently, we’ve seen the proliferation of UAVs granting dismounted infantry the ability to reach out and strike their enemies with both precision and enhanced lethality, far deeper than ever before; enabling lesser powers with asymmetrical advantage in the Air Domain; and empowering Violent Extremist Organizations (VEOs) with the ability to “punch above their weight class.” We’ve also seen UAVs employed in Large-Scale Combat Operations (LSCO), with Russia and Ukraine wrapping up their third year of conflict — characterized by rapid cycles of innovation in both UAV development and Counter-Unmanned Aerial Systems (C-UAS).
Simultaneously, we’ve witnessed the resurgent scourge of chemical weapons and explored the emergent potential of Artificial Intelligence (AI) in shaping the future of biological and chemical warfare. Perhaps most disturbingly, we’ve seen the repeated use of chemical weapons on the battlefields of Ukraine by Russian forces — as of 18 January 2025, the Ukrainian General Staff reported “that Russian forces used ammunition equipped with chemical agents banned by the Chemical Weapons Convention (CWC) 434 times in Ukraine in December 2024, contributing to a total of 5,389 documented cases since February 2023.” As observed in TRADOC Pamphlet 525-92, The Operational Environment 2024-2034 Large-Scale Combat Operations:
“Adversaries view weapons of mass destruction (WMD) as an asymmetric advantage that has an outsized impact on U.S. operations and will likely seek to employ WMD in LSCO.“
Today’s submission — co-authored by frequent contributor and proclaimed Mad Scientist Dr. James Giordano and returning contributor Dr. Diane DiEuliis — addresses the “nexus of drones and bioweapons” in Twenty-first century conflict, exploring how “drone technology, synthetic biology, and gene-editing pose a formidable challenge to global security.” This convergent challenge demands we “invest in fostering interagency and international collaboration, advanced surveillance systems, and develop robust countermeasures to mitigate the risks associated with these technologies” — Read on!]
 The United States National Drone Association (USNDA) recently announced its sponsorship of the inaugural, international U.S. Military Drone Crucible Drone Championship to provide a venue for exercising U.S. and allied military drone training, advanced piloting, operational utility, and counter-measures’ capability. The relevance – and importance – of such incentives and initiatives is clear in light of iterative development, availability, and utilization of drone technology in military operations, and potential manifestations of envisioned large-scale drone employment in kinetic and
The United States National Drone Association (USNDA) recently announced its sponsorship of the inaugural, international U.S. Military Drone Crucible Drone Championship to provide a venue for exercising U.S. and allied military drone training, advanced piloting, operational utility, and counter-measures’ capability. The relevance – and importance – of such incentives and initiatives is clear in light of iterative development, availability, and utilization of drone technology in military operations, and potential manifestations of envisioned large-scale drone employment in kinetic and  non-kinetic engagements. As the National Defense Strategy warned, advances in such emerging technology not only changes the nature of conflict, but can also be used to disrupt day-to-day U.S. supply chains, logistics, and economic stability. As readily evidenced by the Ukraine war, the use of drones in combat scenarios is being tested in real time; and the United States’ acute threat – Russia – is amassing significant experience with their battlefield deployment. Such experience can certainly be used to further develop drone capability and defenses in response.
non-kinetic engagements. As the National Defense Strategy warned, advances in such emerging technology not only changes the nature of conflict, but can also be used to disrupt day-to-day U.S. supply chains, logistics, and economic stability. As readily evidenced by the Ukraine war, the use of drones in combat scenarios is being tested in real time; and the United States’ acute threat – Russia – is amassing significant experience with their battlefield deployment. Such experience can certainly be used to further develop drone capability and defenses in response.
Indeed, drones — ranging from commercially available systems to custom-engineered platforms — can be effectively and efficiently committed in a variety of battlescape scenarios. Their small size, affordability, and versatility make them attractive tools for adversaries seeking to leverage asymmetrical advantage. Key attributes of drones include:
-
-
- Ease of Modification: Commercial drones can be developed and/or modified to deliver a variety of types and volumes of payloads.
-
-
-
- Stealth and Precision: Drones can evade radar and air defense systems, enabling covert operations in urban or rural environments.
-
-
-
- Range and Scalability: Advanced drones can operate over long distances and be deployed either individually (for granular, precision-engagements) or in swarms, fortifying their operational impact and value.
-
The accessibility of drones provides cost-efficient means of payload delivery in state-vs-state engagements and lowers the barrier to entry for non-state actors, including terrorist organizations and criminal networks; thereby creating a dispersed and decentralized threat that is challenging to monitor and mitigate.
The convergence of advanced drone technology with novel biotechnological tools, such as synthetic biology and gene editing, poses a further – and escalating – risk to global security. As the sophistication and accessibility of these technologies increase, so does their potential misuse by state and non-state actors for malicious purposes.
S ynthetic biology and gene editing technologies, such as CRISPR-Cas systems, represent transformative tools with vast potential in precision medicine, agriculture, and industrial processes. However, these same technologies have dual-use potential, and may be repurposed to develop biological agents capable of targeting select individuals, particular populations, ecosystems, and/or critical resources.
ynthetic biology and gene editing technologies, such as CRISPR-Cas systems, represent transformative tools with vast potential in precision medicine, agriculture, and industrial processes. However, these same technologies have dual-use potential, and may be repurposed to develop biological agents capable of targeting select individuals, particular populations, ecosystems, and/or critical resources.

Key capabilities of these bio-scientific and technological tools include:
-
-
- Pathogen Enhancement: Modifying existing pathogens to increase virulence, transmissibility, escape diagnostics, or confer resistance to medical countermeasures.
-
-
-
- Precision Bioengineering: Designing pathogens to target specific genetic markers within populations, enabling selective effects.
-
-
-
- Environmental Disruption: Engineering microorganisms to degrade infrastructure materials or disrupt ecosystems, creating widespread collateral damage.
-
The Nexus of Drones and Bioweapons: Capabilities and Counters
When combined with the deployment capabilities of drones, these biotechnological innovations pose an unprecedented challenge to traditional security frameworks. Such synergy amplifies the threat of bioweapons. Possible scenarios that illustrate the operational potential of this nexus include:
-
-
- Targeted Attacks: Drones equipped with aerosol dispersal mechanisms can release bioengineered agents in specific locations, targeting critical infrastructure or densely populated areas.
-
-
-
- Bio-Terrorism: State and non-state actors could exploit drones to execute high-profile attacks, creating psychological, economic, and political disruption.
-
-
-
- Diversion of Commercial Drones for Malicious Purposes: Drones that enable precision agriculture, frequently sourced from adversary nations such as China, can be compromised or diverted to disrupt food/agricultural security.
-
-
-
- Assassination and Sabotage: Precision bioengineering can enable the creation of agents designed to target specific individuals or groups based on genetic profiles, delivered by drones to precise locations.
-
To be sure, this convergence creates tactical and strategic challenges for military forces tasked with deterrence, defense, and response. The increasing  sophistication of drone-based bioweapons necessitates a reevaluation of existing military doctrines and operational paradigms. We opine that critical implications emerge in four principal domains:
sophistication of drone-based bioweapons necessitates a reevaluation of existing military doctrines and operational paradigms. We opine that critical implications emerge in four principal domains:
1. Detection and Prevention: Current surveillance systems must evolve to detect drones and biotechnological threats effectively. This includes:
Drone Detection: Developing advanced radar, acoustic, and visual systems capable of identifying drones, particularly those designed for stealth operations.
Bio-surveillance: Enhanced capabilities to monitor environmental and public health indicators for early detection of bioweapon deployment.
2. Countermeasure Development: Defensive measures must include:
Counter-Drone Systems: Deploying technologies such as jamming, directed-energy weapons, and drone swarms to neutralize hostile drones.
Bio-defense Research: Enabling early warning and enhanced bio-detection, particularly in the environment, and, accelerating the development of vaccines, therapeutics, and diagnostic tools to counter novel biological agents.
 3. Training and Preparedness: Military personnel must be trained to operate in environments where biotechnological weapons may be used. This includes:
3. Training and Preparedness: Military personnel must be trained to operate in environments where biotechnological weapons may be used. This includes:
Augmented Training: Expanding chemical, biological, radiological, and nuclear (CBRN) training to include scenarios involving drone-delivered biological (and other unconventional) weapons.
Interagency Coordination: Strengthening collaboration between military, intelligence, public health, and law enforcement agencies to create a unified assessment and response framework.
4. Intelligence and Risk Assessment: Enhanced intelligence capabilities are essential for identifying peer-competitor and potential adversaries’ use of drones, and developing and implementing technological advancements necessary to identify, track, and deter such threats. This includes:
Threat Profiling: Monitoring state and non-state actors known to have access to both drone and biotechnological technologies.
Supply Chain Monitoring: Identifying and disrupting the flow of materials and knowledge required to develop bioweapons.
Ethical and Legal Considerations
The use of drones to deliver biotechnological weapons raises profound ethical and legal challenges. These include:
Attribution: Identifying the perpetrators of drone-based bioweapon attacks can be difficult, particularly if and when (a) the drone is destroyed in executing the mission; and/or (b) non-state actors or proxy forces are involved.
Accountability: Ensuring that states adhere to international norms, such as the Biological Toxins and Weapons Convention, and regulations for drone deployment can be irrelevant if drones are clandestinely or covertly used (see above), and if state or non-state actors exploit legal loopholes.
Proportionality: Developing response protocols that balance the need for decisive action with the potential for escalation and collateral damage (e.g., can/should a drone-based engagement be countered with non-drone, conventional weapon, and/or human actor response?)
As drones and biotechnology are iteratively developed and advanced, it will be crucial for the U.S. and its allies to monitor, navigate, and address these complexities while upholding established principles of discrimination, necessity, and proportionality in response.
The Future of the Threat – and Response – Landscape
 The integration of artificial intelligence (AI) into both drone and biotechnological platforms represents a next phase of this threat evolution. AI-driven systems coupled to open-source biotechnology platforms lowers the barriers for adversaries to develop and deploy bioweapons, and the use of AI
The integration of artificial intelligence (AI) into both drone and biotechnological platforms represents a next phase of this threat evolution. AI-driven systems coupled to open-source biotechnology platforms lowers the barriers for adversaries to develop and deploy bioweapons, and the use of AI  could enable increasingly autonomous decision-making, swarm coordination, and precision targeting of drones; which when taken either separately or in combination, further complicates defensive efforts.
could enable increasingly autonomous decision-making, swarm coordination, and precision targeting of drones; which when taken either separately or in combination, further complicates defensive efforts.
To address this evolving threat, we propose a proactive and forward-looking, multi-focal approach, to entail:
Technology Foresight: To anticipate capabilities of emerging technologies and their potential misuse.
Scenario Planning: Toward developing and assessing response protocols for a range of plausible threat scenarios.
International Collaboration: So as to engage allies, international organizations, and the private sector to share knowledge, develop standards, and build collective resilience and coordinated response protocols and parameters.
Conclusion
 The convergence of drone technology, synthetic biology, and gene-editing represents a formidable challenge to global security. As history often demonstrates, the misuse of innovative technologies often outpaces an ability to expediently respond. We posit that vigilance, foresight, and preparedness will be vital to address these challenges and protect against the exploitation of emerging technology for malicious purposes. For military forces, this emerging threat necessitates a paradigm shift in the detection, mitigation, and prevention of drone-based attacks. Indeed, the military’s role in this endeavor is critical—not only as a defensive force but also as a leader in shaping the ethical and legal frameworks that govern the use of emerging technologies. With the new administration, it will be important to invest in fostering interagency and international collaboration, advanced surveillance systems, and developing robust countermeasures to mitigate the risks associated with these technologies while preserving strategic and operational stability.
The convergence of drone technology, synthetic biology, and gene-editing represents a formidable challenge to global security. As history often demonstrates, the misuse of innovative technologies often outpaces an ability to expediently respond. We posit that vigilance, foresight, and preparedness will be vital to address these challenges and protect against the exploitation of emerging technology for malicious purposes. For military forces, this emerging threat necessitates a paradigm shift in the detection, mitigation, and prevention of drone-based attacks. Indeed, the military’s role in this endeavor is critical—not only as a defensive force but also as a leader in shaping the ethical and legal frameworks that govern the use of emerging technologies. With the new administration, it will be important to invest in fostering interagency and international collaboration, advanced surveillance systems, and developing robust countermeasures to mitigate the risks associated with these technologies while preserving strategic and operational stability.
If you enjoyed this post, check out the following related TRADOC G-2 and Mad Scientist Laboratory content on UAVs:
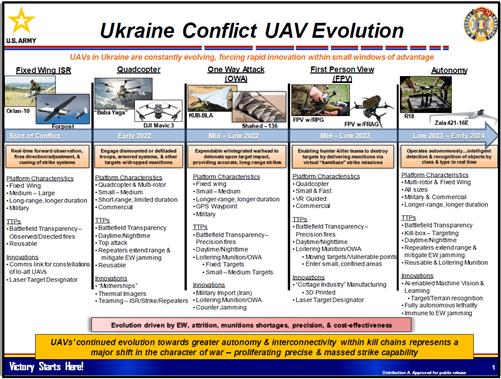
Ukraine Conflict UAV Evolution, by Colin Christopher
Unmanned Capabilities in Today’s Battlespace
Revolutionizing 21st Century Warfighting: UAVs and C-UAS
The Operational Environment’s Increased Lethality
Top Attack: Lessons Learned from the Second Nagorno-Karabakh War and associated podcast, with proclaimed Mad Scientist COL John Antal (USA-Ret.)
Redefining Asymmetric Warfare, by Ethan Sah
… and Biological-Chemical Warfare:
Artificial Intelligence: Shaping the Future of Biological-Chemical Warfare by Jared Kite
CRISPR Convergence, by proclaimed Mad Scientist Howard R. Simkin
Designer Genes: Made in China? by proclaimed Mad Scientist Dr. James Giordano and Joseph DeFranco
WMD Threat: Now and in the Future
The Resurgent Scourge of Chemical Weapons, by Ian Sullivan
A New Age of Terror: New Mass Casualty Terrorism Threat and A New Age of Terror: The Future of CBRN Terrorism by proclaimed Mad Scientist Zak Kallenborn
Dead Deer, and Mad Cows, and Humans (?) … Oh My! by proclaimed Mad Scientists LtCol Jennifer Snow and Dr. James Giordano, and Joseph DeFranco
Read our TRADOC Pamphlet 525-92, The Operational Environment 2024-2034: Large-Scale Combat Operations
Then explore the TRADOC G-2‘s Operational Environment Enterprise web page, brimming with information on the Operational Environment and how our adversaries fight, including:
Our China Landing Zone, full of information regarding our pacing challenge, including ATP 7-100.3, Chinese Tactics, BiteSize China weekly topics, People’s Liberation Army Ground Forces Quick Reference Guide, and our thirty-plus snapshots captured to date addressing what China is learning about the Operational Environment from Russia’s war against Ukraine (note that a DoD Common Access Card [CAC] is required to access this last link).
Our Russia Landing Zone, including the BiteSize Russia weekly topics. If you have a CAC, you’ll be especially interested in reviewing our weekly RUS-UKR Conflict Running Estimates and associated Narratives, capturing what we learned about the contemporary Russian way of war in Ukraine over the past two years and the ramifications for U.S. Army modernization across DOTMLPF-P.
Our Iran Landing Zone, including the latest Iran OE Watch articles, as well as the Iran Quick Reference Guide and the Iran Passive Defense Manual (both require a CAC to access).
Our Running Estimates SharePoint site (also requires a CAC to access), containing our monthly OE Running Estimates, associated Narratives, and the 2QFY24, 3QFY24, 4QFY24, and 1QFY25 OE Assessment TRADOC Intelligence Posts (TIPs).
About the Authors:
Mad Scientist Dr. James Giordano is Director of the Center for Disruptive Technology and Future Warfare of the Institute for National Strategic Studies at the National Defense University, Washington, DC; and is Professor Emeritus in the Departments of Neurology and Biochemistry, Georgetown University Medical Center, Washington, DC.
Dr. Diane DiEuliis is a Distinguished Research Fellow at National Defense University, where she researches the impacts of emerging technologies on biodefense, biosecurity
Disclaimer: The views expressed in this blog post are solely those of the authors, and do not necessarily reflect those of the U.S. Government, the Department of Defense, Department of the Army, Army Futures Command (AFC), Training and Doctrine Command (TRADOC), and/or those institutions and organizations that provide support for the authors’ work.



