[Editor’s Note: Mad Scientist welcomes guest blogger CW4 Charles Davis with his timely submission on the role of Information Advantage in competition, crisis, and conflict. As we’ve seen during the past several weeks in Ukraine, while the combat potential of massed military might at first appear intimidating, to paraphrase Josef Stalin, “Information Advantage has a quality of its own!”
President Volodymyr Zelensky, his Defense Forces, and the plucky Ukrainian citizens are demonstrating the power of Information Advantage in galvanizing both domestic and Western support for the defense of Ukraine. In spite of Russia’s initial massive cyber offensive, Elon Musk‘s Starlink provided Dishy ground stations and space internet services to help ensure Ukraine’s continued connectivity. Social media has entered the kill chain, with every Ukrainian Soldier and civilian serving as a sensor. As addressed in our previous post and podcast with MAJ John Spencer (USA-Ret.) on the ongoing conflict in Ukraine, information from around the world is being received in the combat zone and directly influencing on-going kinetic operations, demonstrating that the information age is changing the character of war. CW4 Davis’ post today serves as an Information Advantage primer, addressing how our understanding of its power has evolved over time and defining the positional advantages it offers our warfighters — Read on!]
“Future conflicts could well be decided by information advantage, success going to the side that transforms vast amounts of data from distributed sensors and weapons systems across multiple domains into actionable information for better, faster decision making and precision effects.” — David L. Norquist, Deputy Secretary of Defense, September 2020
 During the Clinton Administration, The White House addressed the need for Maintaining Military Advantage Through Science and Technology Investment. “We seek to preserve an information advantage over the adversary in all conflicts. Military forces need 24-hour all-weather surveillance. They need the ability to see through foliage and camouflage, under water, and through the earth’s surface. They need the ability to track difficult targets such as cruise, anti-ship, and ballistic missiles as well as quiet submarines. They need the means to positively distinguish friend from foe in combat. The military also needs to know if and where weapons of mass destruction are being produced and in what quantity.”1 The administration’s focus during this period was on collection of information, not particularly security, control, and dissemination.
During the Clinton Administration, The White House addressed the need for Maintaining Military Advantage Through Science and Technology Investment. “We seek to preserve an information advantage over the adversary in all conflicts. Military forces need 24-hour all-weather surveillance. They need the ability to see through foliage and camouflage, under water, and through the earth’s surface. They need the ability to track difficult targets such as cruise, anti-ship, and ballistic missiles as well as quiet submarines. They need the means to positively distinguish friend from foe in combat. The military also needs to know if and where weapons of mass destruction are being produced and in what quantity.”1 The administration’s focus during this period was on collection of information, not particularly security, control, and dissemination.
 Information advantage was again addressed in the 2018 National Defense Strategy. “During peace or in war, the Joint Force will deter nuclear and non-nuclear strategic attacks and defend the homeland. To support these missions, the Joint Force must gain and maintain information superiority; and develop, strengthen, and sustain U.S. security relationships. Investments will prioritize developing resilient, survivable, federated networks and information ecosystems from the tactical level up to strategic planning. We will emphasize new skills and complement our current workforce with information experts, data scientists, computer programmers, and basic science researchers and engineers—to use information, not simply manage it. Our allies and partners provide complementary capabilities and forces along with unique perspectives, regional relationships, and information that improve our understanding of the environment and expand our options.”2 This administration expanded on the idea that we need more information and addressed the necessity of managing information, as well as the need to strengthen partnership sharing. However, information advantage is not defined.
Information advantage was again addressed in the 2018 National Defense Strategy. “During peace or in war, the Joint Force will deter nuclear and non-nuclear strategic attacks and defend the homeland. To support these missions, the Joint Force must gain and maintain information superiority; and develop, strengthen, and sustain U.S. security relationships. Investments will prioritize developing resilient, survivable, federated networks and information ecosystems from the tactical level up to strategic planning. We will emphasize new skills and complement our current workforce with information experts, data scientists, computer programmers, and basic science researchers and engineers—to use information, not simply manage it. Our allies and partners provide complementary capabilities and forces along with unique perspectives, regional relationships, and information that improve our understanding of the environment and expand our options.”2 This administration expanded on the idea that we need more information and addressed the necessity of managing information, as well as the need to strengthen partnership sharing. However, information advantage is not defined.
 Information advantage is again mentioned in The Strategy for Operations in the Information Environment (IE). More importantly it states that the purpose of the strategy is to lay out a path for the DoD to “gain advantage in the IE.”3 The IE strategy identifies four lines of effort (LoE) intended to secure and sustain advantage. However, it does not provide clarity as to what an advantage in the IE looks like. A Similar approach was taken in Joint Concept for Operating in the Information Environment. While it addresses the things required to gain and maintain information advantage, it does not help leaders visualize what that advantage will look like.4
Information advantage is again mentioned in The Strategy for Operations in the Information Environment (IE). More importantly it states that the purpose of the strategy is to lay out a path for the DoD to “gain advantage in the IE.”3 The IE strategy identifies four lines of effort (LoE) intended to secure and sustain advantage. However, it does not provide clarity as to what an advantage in the IE looks like. A Similar approach was taken in Joint Concept for Operating in the Information Environment. While it addresses the things required to gain and maintain information advantage, it does not help leaders visualize what that advantage will look like.4
As we move forward in developing doctrine which defines and discusses information advantage, we should address operational terms such as degradation, disruption, and disorder; reinforcing the need to mask those events associated with the friendly state and exploit them when they appear in our adversaries. We must control the message and perception. Furthermore information advantage doctrine must include direct effects to the adversaries OODA Loop (shown below), through effective messaging and dis-misinformation. Information advantage cannot be viewed as simply effectively and expeditiously collecting information. Joint Forces must include controlling when, how, and what information the adversary receives.
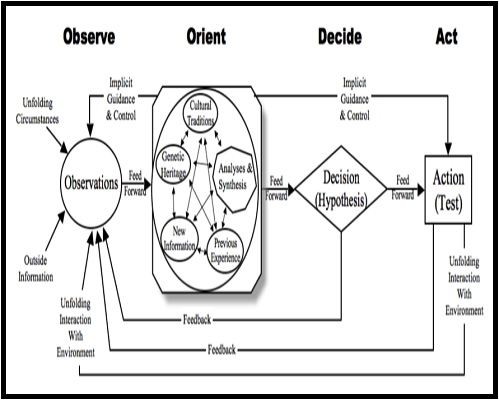
 This approach can be found in a Joint Concept Note by the United Kingdom’s Ministry of Defense, identifying information advantage as “the credible advantage gained through the continuous, adaptive, decisive and resilient employment of information and information systems.”5 Similar observations are evident in a change for JP 3-13, Information Operations, “The operational advantage derived from the ability to collect, process, and disseminate an uninterrupted flow
This approach can be found in a Joint Concept Note by the United Kingdom’s Ministry of Defense, identifying information advantage as “the credible advantage gained through the continuous, adaptive, decisive and resilient employment of information and information systems.”5 Similar observations are evident in a change for JP 3-13, Information Operations, “The operational advantage derived from the ability to collect, process, and disseminate an uninterrupted flow  of information while exploiting or denying an adversary’s ability to do the same.”6 A final example comes in how information operations are defined as the integrated employment, during military operations, of information-related capabilities in concert with other lines of operation to influence, disrupt, corrupt, or usurp the decision-making of adversaries and potential adversaries while protecting our own.
of information while exploiting or denying an adversary’s ability to do the same.”6 A final example comes in how information operations are defined as the integrated employment, during military operations, of information-related capabilities in concert with other lines of operation to influence, disrupt, corrupt, or usurp the decision-making of adversaries and potential adversaries while protecting our own.
Given these examples and what the Joint Force needs to secure information advantage, it could be defined as Gains associated with effective employment of information security, control, and dissemination. This would include protecting information that could be exploited by our adversaries and controlling the type, time, and volume of information our adversaries can access. In this context, Information Advantage would include not only collection/intelligence, but also information operations and disinformation.
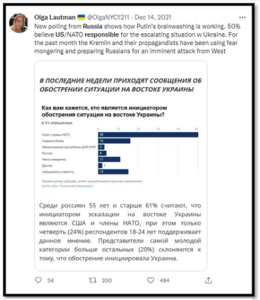
Dis-misinformation is a critical component to the information advantage process, as a Massachusetts Institute of Technology study recently demonstrated. “We found that falsehood diffuses significantly farther, faster, deeper, and more broadly than the truth, in all categories of information, and in many cases by an order of magnitude.” Their findings are staggering, with an assessment that false news is 70% more likely to be retweeted than the truth, with true stories taking six times as long to reach the same number of people.7 This is why changing a narrative is so time consuming and often futile, reinforcing the need for effective and timely messaging capabilities within the Joint Force.
In his paper Understanding and Pursuing Information Advantage, Dr. Christopher Paul provides a table which includes six categories of information: 1) Situational awareness; 2) Command and control; 3) Factors that degrade C2 and SA; 4) Factors leading to contrary behavior; 5) Efforts to affect behavior, and 6) Efforts to affect behavior more broadly. Similarly, George Seffers identifies five essential tasks in his Army Officials Teach Information Advantage 101. These tasks are to enable decision making, protect friendly information, inform and educate domestic audiences, inform and influence international audiences, and conduct information warfare.8 In both cases, these categories are easily applied to the suggested definition Gains associated with effective employment of information security, control, and dissemination.
Chris Dougherty’s Confronting Chaos: A New Concept for Information Advantage clearly articulates his point, “Information advantage should be understood as gaining a temporary and contested edge in using information through technical systems, cognitive processes, and perceptual/psychological influence to achieve tactical, operational, or strategic advantages against a competitor in peacetime or an adversary in war.”9 Dougherty argues information was defined broadly, and advantage was meant to express continuous challenges in the information environment with adversaries like China or Russia. “Advantage was meant to be marginal, ephemeral, contingent, and constantly fought over.”10 Dougherty intuitively points to how both Russia and China are likely to attempt limited conflict to avoid western encroachments, seeing themselves as locked in a continuous information confrontation or struggle in which they counter U.S. information operations while creating advantageous conditions for themselves.11
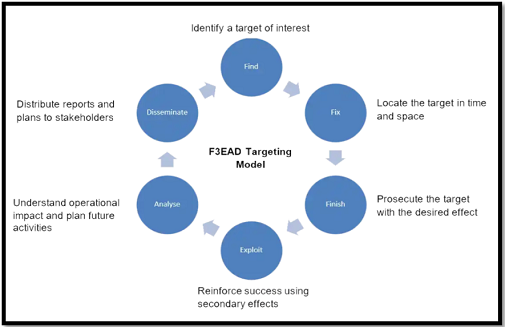
Sam Qaisar, a UK-based capabilities engineer, suggests that information warfare can lead to significant operational benefits in Exploiting Information to you Operational Advantage. “This can be most easily understood by considering the Find, Fix, Finish, Exploit, Analyze, Disseminate (F3EAD) targeting model. A key element of this is understanding information flow around the battlespace and using this to create models of the decision-making process which can be used to aid in targeting.” The process must also be applied to friendly forces in order to identify and mitigate our own vulnerabilities.12 Qaisar goes on to advocate for media operations, network analysis and application of both offensive and defensive cyber operations.
Brigadier General Paul Stanton, Commander of the Cyber Center of Excellence, has stated: “What you’re allowed to do for military deception operations is very different from what you’re allowed to do from public affairs. Messaging is very different from what you do in terms of achieving a strategic cyber effect. Putting all those pieces together is the future command-and-control model that we have to experiment and learn.”13 To that end, the Army is considering a G-39 C2 element to effectively nest information advantage opportunities with operational priorities.
 Regarding our near peer or pacing adversaries, the Army must be careful of setting mission or capability constraints which gravely undermine actionable information advantage. Lightning Press’ INFO1: The Information Operations & Capabilities SMARTbook (Guide to Information Operations & the IRCs) provides examples of what is termed positional advantage. When applied against an understanding of information advantage, certain objectives can be developed and applied against Army COA development and the Military Decision Making Process.
Regarding our near peer or pacing adversaries, the Army must be careful of setting mission or capability constraints which gravely undermine actionable information advantage. Lightning Press’ INFO1: The Information Operations & Capabilities SMARTbook (Guide to Information Operations & the IRCs) provides examples of what is termed positional advantage. When applied against an understanding of information advantage, certain objectives can be developed and applied against Army COA development and the Military Decision Making Process.
Positional Advantages
-
-
 Physical and geographical (including strategic positioning, sanctuary, and control of key terrain): Information advantage applied here would include understanding when, why, and for how long this terrain provides advantage or disadvantage, and what perceptions of this situation can be masked or exploited to secure operational success.
Physical and geographical (including strategic positioning, sanctuary, and control of key terrain): Information advantage applied here would include understanding when, why, and for how long this terrain provides advantage or disadvantage, and what perceptions of this situation can be masked or exploited to secure operational success.
-
-
-
- Combat power and warfighting function overmatch (including range, lethality, precision, and mass): Information advantage applied here would include understanding when, why, and for how long this overmatch will exist for us or our adversaries, and what perceptions of this situation can be masked or exploited to secure operational success.
-
-
-
 Relationships and influence (including allies, interoperability, access, and indigenous forces): Information advantage applied here would include understanding the reason/drivers of the relationship, the extent to which they could be strained, and what fractures exist that might be exploited by us or our adversaries to strengthen/erode the relationship in an effort to secure operational success.
Relationships and influence (including allies, interoperability, access, and indigenous forces): Information advantage applied here would include understanding the reason/drivers of the relationship, the extent to which they could be strained, and what fractures exist that might be exploited by us or our adversaries to strengthen/erode the relationship in an effort to secure operational success.
-
-
-
- Legitimacy, ideas, and popular perception (including what is good versus bad, accepted versus opposed, and a believable narrative): Information advantage applied here would include understanding how legitimacy is established; the drivers of popular perception; and how ideas, identities, and perceptions could be masked or exploited to reinforce/erode perceptions and secure operational success.
-
-
-
- Time (including speed of recognition, speed of decision making, speed of action, and operational tempo): Information advantage applied here
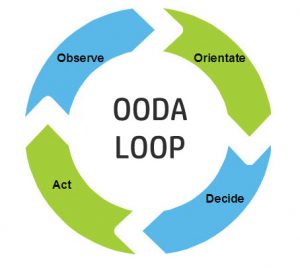 would include understanding how long the information is of value and how that window can be manipulated, distorted, or disrupted to affect the adversary’s OODA Loop and secure operational success.
would include understanding how long the information is of value and how that window can be manipulated, distorted, or disrupted to affect the adversary’s OODA Loop and secure operational success.
- Time (including speed of recognition, speed of decision making, speed of action, and operational tempo): Information advantage applied here
-
-
-
- Freedom of action (including secure lines of communications, standoff, depth, access to cyberspace, maritime and air enablers, and friendly A2 & AD measures): Information advantage applied here would include understanding where our adversary perceives an advantage exists and
 who they believe holds the advantage; then reinforcing misperceptions by exploiting true advantage or masking disadvantage to secure operational success.
who they believe holds the advantage; then reinforcing misperceptions by exploiting true advantage or masking disadvantage to secure operational success.
- Freedom of action (including secure lines of communications, standoff, depth, access to cyberspace, maritime and air enablers, and friendly A2 & AD measures): Information advantage applied here would include understanding where our adversary perceives an advantage exists and
-
-
-
- Moral (including alignment of words and deeds, just and unjust, international support): Information advantage applied here would include nesting messaging to friendly forces and the population in order to secure ongoing support and reinforce relationships, while identifying and exploiting fractures and misconceptions among our adversaries to secure operational success.
-
-
-
 Will (including doing what must be done, continuing as long as it takes, and maintaining support from domestic leaders): Information advantage applied here would include understanding how our adversaries will attempt to exploit fissures in US domestic politics and popular support at home to reduce public will. Operational success here will depend on our ability to reduce adversarial exploitation of media platforms to produce false narratives and exploit emotional vulnerabilities within the American population and civilian leadership.
Will (including doing what must be done, continuing as long as it takes, and maintaining support from domestic leaders): Information advantage applied here would include understanding how our adversaries will attempt to exploit fissures in US domestic politics and popular support at home to reduce public will. Operational success here will depend on our ability to reduce adversarial exploitation of media platforms to produce false narratives and exploit emotional vulnerabilities within the American population and civilian leadership.
-
The Army is contending with challenges presented by a very different global order, changes in battlefield capabilities, and high paced technological shifts impacting military operations. As such, doctrine shifts must be reviewed with a broader aperture, giving consideration to realized and developing capabilities in the Army arsenal.
In his paper Operations in the Information Environment, LtCol C. Travis Reese, USMC, sums it up very effectively. “Conducting operations in the information environment (OIE) to implement the information war fighting function does not require radical alteration to the art and science of warfare. Rather, it is entirely backward compatible with established principles, the modern iteration of which simply requires reimagining the role of information in conflict.”

If you enjoyed this post, check out the following related content:
War in Ukraine: The Urban Fight is Happening Now, and associated podcast
Are We Ready for the Post-digital Hyper-war? by Capt Martin Crilly, British Army
China and Russia: Achieving Decision Dominance and Information Advantage by Ian Sullivan, along with the comprehensive paper from which it was excerpted
The Future of War is Cyber! by CPT Casey Igo and CPT Christian Turley
Sub-threshold Maneuver and the Flanking of U.S. National Security, by Dr. Russell Glenn
Global Entanglement and Multi-Reality Warfare and associated podcast, with COL Stefan Banach (USA-Ret.)
Hybrid Threats and Liminal Warfare and associated podcast, with Dr. David Kilcullen
Two Vignettes: How Might Combat Operations be Different under the Information Joint Function? by proclaimed Mad Scientist Dr. Christopher Paul
The Erosion of National Will – Implications for the Future Strategist, by Dr. Nick Marsella
Weaponized Information: What We’ve Learned So Far…, Insights from the Mad Scientist Weaponized Information Series of Virtual Events, and all of this series’ associated content and videos
Weaponized Information: One Possible Vignette and Three Best Information Warfare Vignettes
About the Author: CW4 Charles Davis serves on the faculty of the Warrant Officer Career College. He currently instructs International Strategic Studies at all levels of warrant officer education. CW4 Davis is a graduate of the U.S. Army War College Strategic Broadening Program and holds a master’s degree with honors in intelligence studies from American Military University. CW4 Davis is also a recipient of the Military Intelligence Corp Knowlton Award.
Disclaimer: The views expressed in this blog post do not necessarily reflect those of the U.S. Department of Defense, Department of the Army, Army Futures Command (AFC), or Training and Doctrine Command (TRADOC).
1https://clintonwhitehouse4.archives.gov/WH/EOP/OSTP/nssts/html/chapt2.html
2 https://dod.defense.gov/Portals/1/Documents/pubs/2018-National-Defense-Strategy-Summary.pdf
3 U.S. Department of Defense, Strategy for Operations in the Information Environment, Washington, D.C., June 2016, 4. https://dod.defense.gov/Portals/1/Documents/pubs/DoD-Strategy-for-Operations-in-the-IE-Signed-20160613.pdf
4 Joint Concept for Operating in the Information Environment, Washington, D.C.: U.S. Joint Chiefs of Staff, July 2018, preface
5 Ministry of Defence, Information Advantage, Joint Concept Note 2/18, November 2018, 7, https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/919262/20200909-JCN_2_18_Information_Advantage_accessible.pdf
6 Joint Publication 3-13, Information Operations, Washington, D.C.: U.S. Joint Chiefs of Staff, incorporating change 1, November 20, 2014, GL-3, https://www.jcs.mil/Portals/36/Documents/Doctrine/pubs/jp3_13.pdf
7 https://news.mit.edu/2018/study-twitter-false-news-travels-faster-true-stories-0308
8 https://www.afcea.org/content/army-officials-teach-information-advantage-101
9 https://warontherocks.com/2021/09/confronting-chaos-a-new-concept-for-information-advantage/
10 Ibid
11 Ibid
12 https://uk.leonardocompany.com/en/news-and-stories-detail/-/detail/exploiting-information-to-your-operational-advantage
13 https://www.defensenews.com/digital-show-dailies/ausa/2021/10/14/the-next-tool-the-army-needs-for-information-advantage/



