[Editor’s Note: Our strategic competitors have not sat idly by during the past 18 years while the United States has been protractedly and decisively engaged militarily in the Long War’s two theaters of operation (Afghanistan and Iraq). They have watched and learned how we wage war, and discerned how critical our information networks are to multi-domain situational awareness and mission command. Today’s post describes the requisite hybrid Peer-to-Peer (P2P) / Client-Server (C/S) architecture essential to rapidly and continuously integrating the Joint Forces’ multi-domain capabilities, enabling effective mission command and disciplined initiative against near-peer threats in the future.]
 The U.S. Army in Multi-Domain Operations, 2028 describes how U.S. Army forces, as part of the Joint Force, will militarily compete with, penetrate, dis-integrate, and exploit our adversaries in the future. To accomplish this, the Army must develop or improve capabilities that contribute cross-domain options within the Joint Force to “set the theater” (i.e., establish and maintain conditions to seize the initiative and retain freedom of action in the theater of operation). Key amongst these required Army capability sets are computer networks that enable our commanders and staffs at each echelon to visualize and command a battle in all domains, the electromagnetic spectrum (EMS), and the information environment, converging organic and external capabilities at decisive spaces.
The U.S. Army in Multi-Domain Operations, 2028 describes how U.S. Army forces, as part of the Joint Force, will militarily compete with, penetrate, dis-integrate, and exploit our adversaries in the future. To accomplish this, the Army must develop or improve capabilities that contribute cross-domain options within the Joint Force to “set the theater” (i.e., establish and maintain conditions to seize the initiative and retain freedom of action in the theater of operation). Key amongst these required Army capability sets are computer networks that enable our commanders and staffs at each echelon to visualize and command a battle in all domains, the electromagnetic spectrum (EMS), and the information environment, converging organic and external capabilities at decisive spaces.
 However, as noted in The Operational Environment and the Changing Character of Future Warfare, “strategic advantages held during the post-Cold War period … will erode, allowing for increasingly aggressive challengers fielding a full-range of modern, advanced capabilities with hybrid strategies to challenge our ability to bring forces to the fight while undermining our political and national will to do so. Our adversaries’ investments in electronic warfare and space control will threaten our command and control and multi-domain capabilities.”
However, as noted in The Operational Environment and the Changing Character of Future Warfare, “strategic advantages held during the post-Cold War period … will erode, allowing for increasingly aggressive challengers fielding a full-range of modern, advanced capabilities with hybrid strategies to challenge our ability to bring forces to the fight while undermining our political and national will to do so. Our adversaries’ investments in electronic warfare and space control will threaten our command and control and multi-domain capabilities.”
Operating in the cyber domain given a contested EMS presents great vulnerabilities to our current communications systems and architecture. In 2015, over 460 million new pieces of malware were detected across the world.1 Recently, there has been a rise in AI driven cyber-attacks. These AI driven attacks can use machine  learning to adapt and evade detection, causing as much damage or collecting as much information as possible. As time goes on, there will be more surfaces for cyber-attacks as more people are connected on multiple devices.
learning to adapt and evade detection, causing as much damage or collecting as much information as possible. As time goes on, there will be more surfaces for cyber-attacks as more people are connected on multiple devices.
The Army will have to deal with a cultural shift as the human and cyber networks — now considered two distinct entities — form one single human-cyber network.2 Humans will be connected with other human bodies all over the world and the idea of connecting to a network exclusively through a  device will be archaic. The Soldier will have small tattoo-like sensors on several areas of the body, monitoring and communicating with other Soldiers, Command and Control Elements, and autonomous counterparts. Because these sensors and devices will be pervasive, a Machine to Machine (M2M) or Device to Device (D2D) architecture will be dominant. This type of information communications architecture will be primarily Peer to Peer (P2P). This is a fundamental deviation of the classical client-server (C/S) communications.3
device will be archaic. The Soldier will have small tattoo-like sensors on several areas of the body, monitoring and communicating with other Soldiers, Command and Control Elements, and autonomous counterparts. Because these sensors and devices will be pervasive, a Machine to Machine (M2M) or Device to Device (D2D) architecture will be dominant. This type of information communications architecture will be primarily Peer to Peer (P2P). This is a fundamental deviation of the classical client-server (C/S) communications.3
Currently, our devices operate on a network that calls back to a central server (client-server relationship). If communications to the server are disrupted or denied, the entire system loses connectivity. Using a P2P architecture, one can connect to an entity to communicate directly to it or use it as a node to communicate to other devices connected to that node. If that node goes down, or is denied, one can connect to any other available node in the area. The Future Multi-Domain Army must use a hybrid system consisting of P2P and C/S.
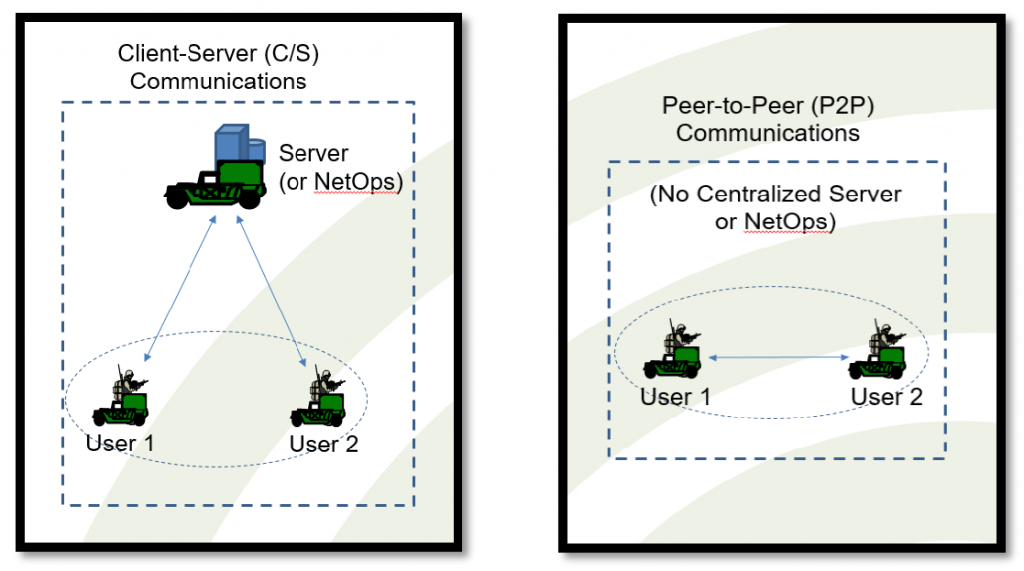
This P2P architecture will be imperative to robotic system swarming. Swarming requires each entity to be aware of and anticipate the moves of the other entities in the swarm. That means that each entity in the swarm needs to be able to directly communicate with the others.  Swarms will be self-organized, and/or collaborative actions of robots with varying degrees of freedom that require P2P communications without fixed infrastructures (i.e., Mobile Ad-Hoc Networks [MANET]).4 The client-server paradigm will be used less often, mainly as back up for process-intensive actions that less powerful devices can off-load.
Swarms will be self-organized, and/or collaborative actions of robots with varying degrees of freedom that require P2P communications without fixed infrastructures (i.e., Mobile Ad-Hoc Networks [MANET]).4 The client-server paradigm will be used less often, mainly as back up for process-intensive actions that less powerful devices can off-load.
Because of the sheer speed and frequency of cyber-attacks, humans will be overmatched. However, with algorithms, machine learning, and natural language processing, cyber-attacks can be prevented, detected, and repaired at machine speed without reliance on humans.  Machine learning will allow them to adapt to newer and more sophisticated attacks, and the decentralized nature of P2P architecture will enable each machine to work independently without needing to wait for other entities.
Machine learning will allow them to adapt to newer and more sophisticated attacks, and the decentralized nature of P2P architecture will enable each machine to work independently without needing to wait for other entities.
Current network architectures and paradigms will not sufficiently support the Army of 2035. The centralized nature of a client-server architecture is not fast enough or dynamic enough to keep up with the pace of AI enabled cyber-attacks. The Army must move to a mostly P2P network allowing individual entities to act, process, and communicate independently, serve as nodes, and take advantage of swarming capabilities. In multi-domain operations, this new architecture will allow the Army to better and more efficiently communicate, reduce points of failure, and minimize cyber-attack surfaces.

If you enjoyed this post, please also see:
-
- Dr. Radhika A. Roy and Mr. Brian M. Dempsey‘s briefing on Commanding in Multi-Domain Formations: Vision 2050 Warfighter Cyber-Security, Command, and Control Architecture, Parts 1 and 2, from the Mad Scientist Visioning Multi Domain Battle in 2030-2050 Conference at Georgetown University in Washington, DC, on 25 & 26 July 2017
-
- Dr. Roy and Mr. Dempsey‘s associated paper Commanding in Multi-Domain Formations: Vision 2050 Warfighter Cyber-Security, Command and Control Architecture, hosted by our colleagues at Small Wars Journal.
-
- Mad Scientist Laboratory‘s posts on:
– Ground Warfare in 2050: How It Might Look, and
– Connected Warfare, by COL James K. Greer (USA-Ret.).
1 ISTR: Internet Security Threat Report, vol. 21, April 2016.
2 Dr. Radhika Roy, “Commanding in Multi-Domain Formations: Vision 2050 Warfighter Cyber-Security, Command and Control Architecture” (speech, Washington, D.C., July 26, 2017)
3 Ibid
4 Ibid



